Recently I was asked this question:
Is it supported to revoke permissions (selectively) for an enterprise application?
This blogpost shows how to manage enterprise applications permissions. Note that Azure Portal UI doesn't allow these actions, so you have to rely on some scripting. Hence this blog post.
What is an enterprise application?
I will take a snippet from one of my old posts to save some time.

To list permissions of an Enterprise Application
To get the list of permissions granted for a given service application you can use script posted to my GitHub Gist. Here is example output:
![]()
To revoke existing permissions of an Enterprise Application
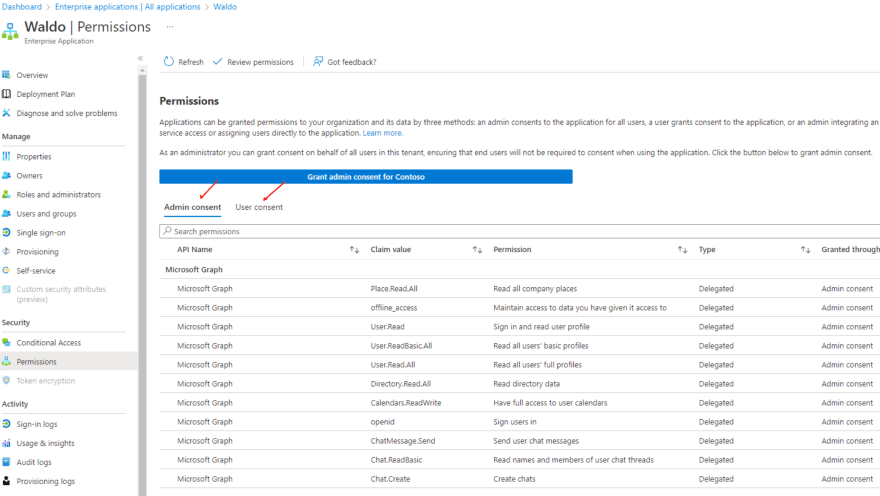
Let's take Waldo App as an example. Here is the enterprise application of Waldo app. Note the object id of this service principal.

Next, view the permissions granted for this app. You can see the permissions in two tabs:
- Admin consent and
- User consent.
 To get the permissions grant for the Waldo app, run below cmdlet with its Object Id.
To get the permissions grant for the Waldo app, run below cmdlet with its Object Id.
Get-MgServicePrincipalOauth2PermissionGrant -ServicePrincipalId 090beef1-f5b6-4f35-9326-6d8596e42942
ConsentType column in the output signifies if its the Admin consent (AllPrincipals) or User consent (Principal) permissions.

Revoke all the permissions
You can remove all the permissions completely using below cmdlet and passing the ID value from the output as the GrantId:
Remove-MgOauth2PermissionGrant -OAuth2PermissionGrantId 8e4LCbb1NU-TJm2FluQpQjqF4W-UGkRLtzPexGZThns
Revoke the permissions selectively
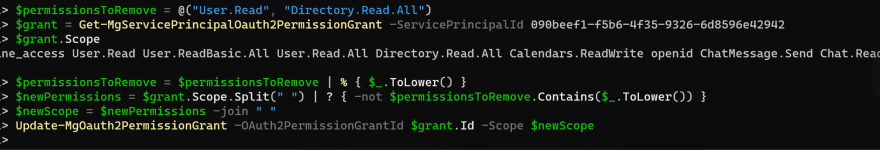
In order to remove the permissions (aka scopes) selectively. Here is an example. Let's say I want to remove "User.Read" and "Directory.Read.All" scopes but retain other scopes. Create an array for the scopes to be removed:
$permissionsToRemove = @("User.Read", "Directory.Read.All")
Get the grants using the object id:
$grant = Get-MgServicePrincipalOauth2PermissionGrant -ServicePrincipalId 090beef1-f5b6-4f35-9326-6d8596e42942
$grant.Scope
Here is the sample output of the scopes that are already granted:
Place.Read.All offline_access User.Read User.ReadBasic.All User.Read.All Directory.Read.All Calendars.ReadWrite openid ChatMessage.Send Chat.ReadBasic Chat.Create
Create a new array of scopes by removing the unwanted scopes.
$permissionsToRemove = $permissionsToRemove | % { $_.ToLower() }
$newPermissions = $grant.Scope.Split(" ") | ? { -not $permissionsToRemove.Contains($_.ToLower()) }
$newScope = $newPermissions -join " "
Finally update the grant with the new scopes using the grant id.
Update-MgOauth2PermissionGrant -OAuth2PermissionGrantId $grant.Id -Scope $newScope
Here is a sample run of the above cmdlets:
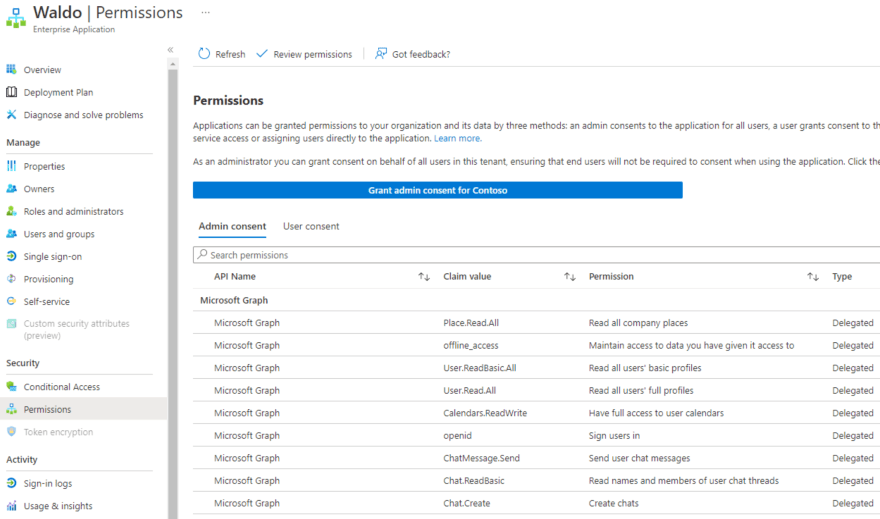
After removing the 2 scopes here is the current permissions:
To grant permissions to an enterprise application
Below is a sample script that shows how to add Microsoft Graph permissions to an enterprise application.
# The object id of the enterprise application
$ObjectId = "b29d7573-2f76-49b6-b660-cc85b34fe516"
# Add the correct Graph scope to grant (e.g. User.Read)
$graphScope = "Sites.Selected"
Connect-MgGraph -Scope AppRoleAssignment.ReadWrite.All
# Get the Microsoft Graph service principal
$graph = Get-MgServicePrincipal -Filter "AppId eq '00000003-0000-0000-c000-000000000000'"
# Get the graph app role for the scope that we want to grant
$graphAppRole = $graph.AppRoles | ? Value -eq $graphScope
# Prepare the app role assignment
$appRoleAssignment = @{
"principalId" = $ObjectId
"resourceId" = $graph.Id
"appRoleId" = $graphAppRole.Id
}
# Grant the app role
New-MgServicePrincipalAppRoleAssignment -ServicePrincipalId $ObjectID -BodyParameter $appRoleAssignment | Format-List
The above script uses the AppRoleAssignment.ReadWrite.All which is a privileged permission. You can grant application permissions using app grant consent policy which doesn't require the privileged permissions. Here is a blog post from Sahil Malik that goes into details of how its done.







Oldest comments (1)
Hi. I tried to revoke the permissions selectively, but getting following error: see the last line in bold please. (I've removed the actual 'Service Principal ID')
PS C:> $permissionsToRemove = @("Group.ReadWrite.All")
PS C:> $grant = Get-MgServicePrincipalOauth2PermissionGrant -ServicePrincipalId 0000-0000-0000...
PS C:> $grant.Scope
User.Read Group.Read.All
DeviceManagementManagedDevices.PrivilegedOperations.All DeviceManagementManagedDevices.ReadWrite.All DeviceManagementRBAC.ReadWrite.All DeviceManagementApps.ReadWrite.All DeviceManagementConfiguration.ReadWrite.All DeviceManagementServiceConfig.ReadWrite.All Group.ReadWrite.All Directory.Read.All openid
PS C:> $permissionsToRemove = $permissionsToRemove | % { $.ToLower() }
PS C:> $newPermissions = $grant.Scope.Split(" ") | ? { -not $permissionsToRemove.Contains($.ToLower()) }
PS C:> $newScope = $newPermissions -join " "
PS C:> Update-MgOauth2PermissionGrant -OAuth2PermissionGrantId $grant.Id -Scope $newScope
Update-MgOauth2PermissionGrant: Cannot process argument transformation on parameter 'OAuth2PermissionGrantId'. Cannot convert value to type System.String.