 As a follow-up to the SSH: RSA keys, and ssh-agent for SSH keys and their passwords management post.
As a follow-up to the SSH: RSA keys, and ssh-agent for SSH keys and their passwords management post.
The idea now is to make simpler to work with password-protected SSH keys, to avoid the necessity to enter a password each time when you want to load a key to the ssh-agent.
One of the possible solutions is to use KeePass, which will store keys and their passwords and will decrypt keys before load them to the ssh-agent.
To achieve this – we need in three components – an ssh-client (ssh, ssh-add, git, etc), the KeePass itself with a KeeAgent plugin, and the ssh-agent which will keep unencrypted files to pass them to clients.
In the examples below the KeePassXC will be used instead of vanilla KeePass, but there is no difference in their configuration (the only difference here is that KeePassXC already has the plugin installed).
In total, the workflow looks like next:
- an
ssh-agentis started, creates a UNIX-socket for communication with other components - KeePass is started, where are keys and their passwords are stored, and KeePass will decrypt keys and push them to the ssh-agent using its UNIX-socket
- any ssh-agent is started, connects via the same socket to the ssh-agent, gets an RSA key for a connect requested by the user
KeePass configuration
Stop already running agents:
[setevoy@setevoy-arch-work ~] $ sudo killall ssh-agent
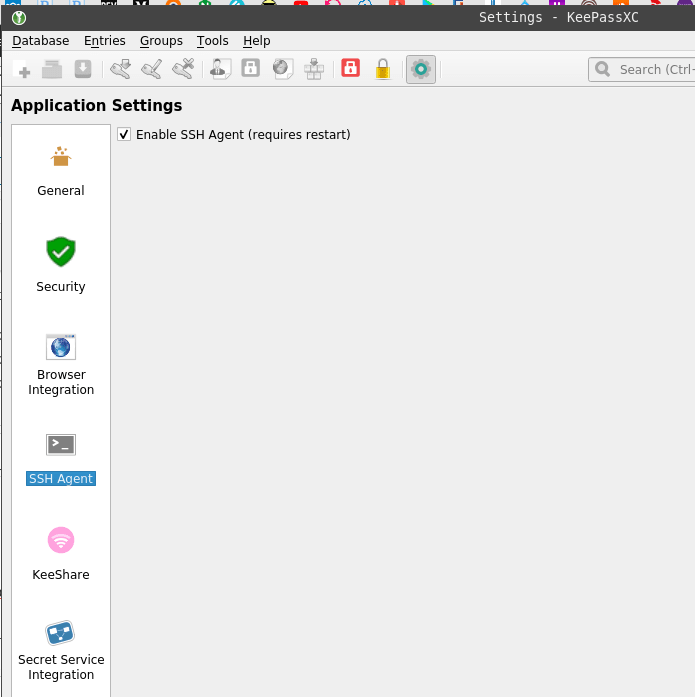
Start KeePass, go to the Tools > Settings > SSH Agent, enable it:
Restart KeePass and see the “_ No agent running, cannot add identity _” error:
It’s OK for now as we didn’t start any agent yet. There are various ways to start it during system startup, check the Running ssh-agent with multitype terminals.
Adding an SSH key to the KeePass
Create a new item:
In the Password field specify a key’s password.
On the left side go to the SSH Agent, via External File chose the key’s file:
ssh-agent
And let’s check how it will work.
Start an agent:
$ eval “$(ssh-agent -s)”
Agent pid 365774
Check variables:
$ env | grep SSH
SSH_AUTH_SOCK=/tmp/ssh-mR9l9Xdx9C8k/agent.1327013
SSH_AGENT_PID=1327014
From the same terminal, to use the $SSH_AUTH_SOCK variable restart KeePass:
$ keepassxc &
Check keys available in the ssh-agent using ssh-add:
$ ssh-add -l
4096 SHA256:WRTfqnw0TPf26r1Zx8eie2fbgxdq7fYdOKjCOtQbjbg This is comment for the Test Key (RSA)
Update your ~/.ssh/confg, add authentication with RSA key:
Host rtfm
Hostname rtfm.co.ua
User setevoy
IdentityFile /home/setevoy/.ssh/test-key
Ty to log in:
$ ssh rtfm
…
setevoy@rtfm-do-production:~$
“It works!”. (c)
“Require user confirmation when this key is used” and “sign_and_send_pubkey: signing failed: agent refused operation“
If you’ll also enable the “Require user confirmation when this key is used” option in the KeePass, during login you can face the “ sign_and_send_pubkey: signing failed: agent refused operation ” error:
$ ssh rtfm
sign_and_send_pubkey: signing failed: agent refused operation
setevoy@rtfm.co.ua’s password:
To solve it – install the ssh-askpass package:
$ sudo pacman -S x11-ssh-askpass
Set the $SSH_ASKPASS variable:
$ export SSH_ASKPASS=/usr/bin//usr/lib/ssh/ssh-askpass
And log in again:
Still, the openssh-askpass won’t work in Arch Linux, see this>>> thread.
Done.










Top comments (0)