Issue:
- You need to use two different github accounts from one computer.
- You don't want to have to configure your ssh keys every time you switch accounts.
- You don't want to edit the repo's ssh address every time you clone a repo either as suggested by a lot of online tutorials.
Solution: You put all your work repos in one folder and update your ssh config to conditionally use a different SSH key. Everything else will use the default ssh key (your personal account).
Github uses the SSH protocol with the RSA cryptosystem to authenticate your computer. When you generate a new SSH key, there will be two keys created - a private key and a public key. You'll need to add the public key to your github account but leave the private key on your machine. You can read more about public-key cryptography here.
If you've already generated and added your SSH keys to your github account, skip this section.
Generating and Adding SSH keys to your github account.
Checking for existing keys
- First, check if there are SSH keys present on your machine by going to terminal and run
ls -al ~/.ssh. By default, the filenames of the public keys start withid_rsaand end in.pub. - If you're not sure which key belongs to which account and want to start with new keys, you can delete your keys by running
ssh-add -Dfrom terminal. This only removes manually added keys so if you're running into issues, take a look at this stackoverflow answer. Make sure to go to the folder where your SSH keys are located - runopen ~/.sshfrom terminal and save a copy before overwriting them.
Generating new keys
-
From terminal, run
ssh-keygen -t rsa -f ~/.ssh/id_rsa -C "your.email@example.com"If you get asked to overwrite an existing key of the same name, type
yif you want to overwrite it. If you don't want to overwrite it, typenand reenter the above command with a new filename. Just changeid_rsato something else likeid_rsa_PERSONAL. Enter a secure passphrase. This will generate two a private key
id_rsaand a public keyid_rsa.pub.Copy the public key
id_rsa.pubby runningpbcopy < ~/.ssh/id_rsa.pubfrom terminal. You can also open the SSH key directory by runningopen ~/.ssh, dragging theid_rsa.pubfile into your code editor and copying the contents of the file.-
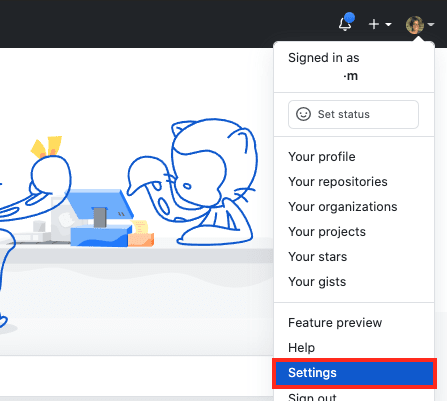
From a browser, go to the settings of your github account by clicking your profile picture from the top right corner.
-
In the user settings sidebar, click
SSH and GPG keys. -
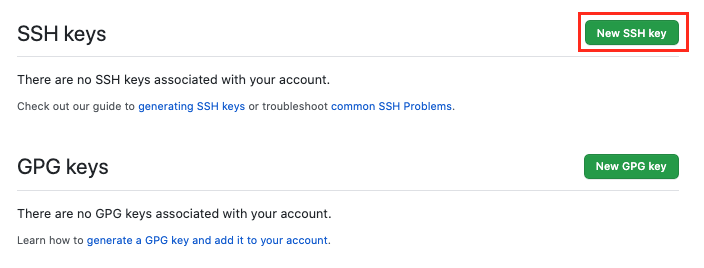
Click
New SSH key -
Paste your copied public key in the "Key" field and give it an appropriate title in the "Title" field.
Click
Add SSH key.
Repeat the above steps to generate and add a new key for your second github account. Just make sure to give a different name like id_rsa_COMPANY .
Setting up SSH config
- From terminal, run
cd ~/.ssh. - Check if a config file exists by running -
ls config. If you seels: config: No such file or directory, create a new config file by runningtouch config. - Open the config file by dragging it into your code editor.
-
Paste the following into the file:
Host github.com HostName github.com User git IdentitiesOnly yes AddKeysToAgent yes UseKeychain yes Match Host github.com !exec "pwd | grep '/COMPANY' > /dev/null" IdentityFile ~/.ssh/id_rsa Match Host github.com exec "pwd | grep '/COMPANY' > /dev/null" IdentityFile ~/.ssh/id_rsa_$COMPANYSource for the above snippet.
Setting
UseKeychainto yes stores your passphrase in the keychain so you don't have to retype it every time.exec "pwd | grep '/COMPANY' > /dev/null"checks if the current folder is nested inside yourCOMPANYfolder. If it is, it'll useid_rsa_$COMPANYSSH key and your default one otherwise. [1] Then run
chmod 600 ~/.ssh/config.
Setting your user.name and user.email
Now that you've set up your SSH keys, you still need to configure your user.name and user.email variables. These determine what ends up in the author and committer field of commit objects. Without setting this, you'll be able to push to your work directory but if you want your commits to have your work email and name, you have set up your .gitconfig files.
- Check if you have an existing
.gitconfigin your root by runningls ~/.gitconfig. If you don't have one, create one by runningtouch ~/.gitconfig. - Do the same for your work directory.
-
Open the
.gitconfigin your root and inside there add your personal git user name and email. Also include anincludeIfpath that tells git to use a different.gitconfigfor your work repos.
# ~/.gitconfig [user] email = your.email@example.com name = your-user-name [user] email = your.email@example.com name = your-user-name [includeIf "gitdir:~/PATH/TO/WORK/DIR/RELATIVE/TO/ROOT"] path = ~/PATH/TO/WORK/DIR/RELATIVE/TO/ROOT/.gitconfig -
Inside the
.gitconfigin your work directory, add your work email and work user name.
# ~/PATH/TO/WORK/DIR/RELATIVE/TO/ROOT/.gitconfig [user] email = your.work.email@example.com name = your-work-user-name
Now you'll be able to use both git accounts with SSH and your commits will have the right email and name for author.
[1] Note: Detailed breakdown of exec "pwd | grep '/COMPANY' > /dev/null":
pwd stands for print working directory . The | takes the standard output of the command on the left, and pipes it as standard input to the command on the right. grep searches plain text for a match. > redirects the results of the previous command to the file on the right. /dev/null is a "black hole" where all data written gets discarded. Read more about /dev/null here.
So the command is basically saying to get your current working directory, search for your COMPANY name and discard the returned value. The exit code from this command will determine which SSH key to use.








Top comments (1)
Very good, thanks for sharing!
I had to change the config file, because I received this message:
'/.ssh/config: line 6: Bad configuration option: usekeychain'
The solution:
Host *
IgnoreUnknown UseKeychain
UseKeychain yes
stackoverflow.com/a/47455373