Hacking is not a crime! Or is it? Well, it depends on which hat you are wearing. Find all about Offense-Defense dilemmas, theories, and practicals here!
Enter the cybersecurity writing contest sponsored by Twingate. Win from monthly $1000 prize pool!
1. The Sneakiest Ethereum “Scam” (honeypot) Ever
 I’ve recently saw a tweet about a sneaky scam where someone would leak a privatekey of an account that owns some token and needs gas to withdraw them. It had a smart contract that would transfer any eth send to its address to another contract. I thought it was pretty good and it reminded of another “scam” I’ve seen few months ago that in my opinion is even sneakier. The common point is that both of these scams are trying to get money from people who had bad intentions in the first place.
I’ve recently saw a tweet about a sneaky scam where someone would leak a privatekey of an account that owns some token and needs gas to withdraw them. It had a smart contract that would transfer any eth send to its address to another contract. I thought it was pretty good and it reminded of another “scam” I’ve seen few months ago that in my opinion is even sneakier. The common point is that both of these scams are trying to get money from people who had bad intentions in the first place.
2. Next Steps in GDPR: What’s to Come in 2019?
 When the General Data Protection Regulation (GDPR) came into effect in May 2018 for entities operating in the European Union or targeting its citizens, most people assumed things would change immediately.
When the General Data Protection Regulation (GDPR) came into effect in May 2018 for entities operating in the European Union or targeting its citizens, most people assumed things would change immediately.
3. How to Avoid Credit Card Skimming: 5 Tips to Keep Your Information Safe
 Credit card skimming occurs when someone places an electronic device on or near a credit card reader. This device captures and stores your credit card details.
Credit card skimming occurs when someone places an electronic device on or near a credit card reader. This device captures and stores your credit card details.
4. Reverse shell !?!
 Whats a reverse shell? It’s that turtle that you jump on and it bounces off a wall and comes back at you right?
Whats a reverse shell? It’s that turtle that you jump on and it bounces off a wall and comes back at you right?
5. How the Nintendo Switch prevents downgrades by irreparably blowing its own fuses
 Downgrade prevention has been a cat-and-mouse game between consumers and companies since the inception of remote updates. The Nintendo Switch adopts a worrisome-strategy of preventing firmware downgrades by permanently modifying your device every time it updates. While this isn’t a new concept (the Xbox 360 was doing it back in 2007), it is part of a greater effort to prevent end users from modifying their devices to their liking.
Downgrade prevention has been a cat-and-mouse game between consumers and companies since the inception of remote updates. The Nintendo Switch adopts a worrisome-strategy of preventing firmware downgrades by permanently modifying your device every time it updates. While this isn’t a new concept (the Xbox 360 was doing it back in 2007), it is part of a greater effort to prevent end users from modifying their devices to their liking.
6. 5 Best Programming Languages to Learn for Cyber Security
 Becoming successful as a cyber security expert requires diverse skills. An all-round professional can confidently implement and monitor security measures that guard computer systems against attacks and unauthorized access.
Becoming successful as a cyber security expert requires diverse skills. An all-round professional can confidently implement and monitor security measures that guard computer systems against attacks and unauthorized access.
7. Hacking my IP camera
 DISCLAIMER: All data and information provided in this article are for informational purposes only. The main goal is to increase security awareness, teach about information security, countermeasures and give readers information on how to implement a safe and functional system. If you plan to use the information for illegal purposes, please leave this website now.
DISCLAIMER: All data and information provided in this article are for informational purposes only. The main goal is to increase security awareness, teach about information security, countermeasures and give readers information on how to implement a safe and functional system. If you plan to use the information for illegal purposes, please leave this website now.
8. Why You Should Never Save Passwords on Chrome or Firefox
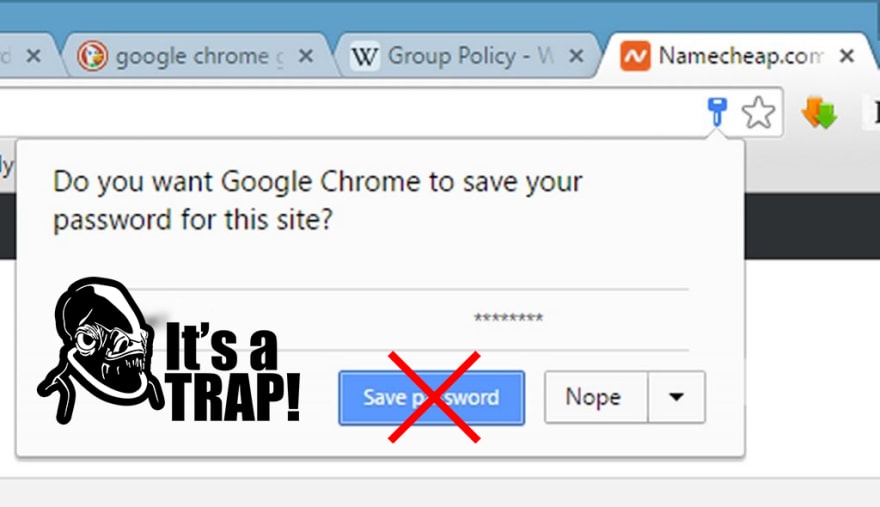 In this article I will demonstrate how easy it is for hackers to extract every username and password saved on your Chrome profile. One would think that Chrome would have safety measures to encrypt your password, but apparently that is not the case — sorta. My Chrome profile, like many others, is set up so that there is another encryption password that I have to enter in order to sync all my passwords, bookmarks, settings, browser history, and etc. so it was pretty shocking to me how easy it was for me to extract and decrypt my passwords. Twelve lines of code easy.
In this article I will demonstrate how easy it is for hackers to extract every username and password saved on your Chrome profile. One would think that Chrome would have safety measures to encrypt your password, but apparently that is not the case — sorta. My Chrome profile, like many others, is set up so that there is another encryption password that I have to enter in order to sync all my passwords, bookmarks, settings, browser history, and etc. so it was pretty shocking to me how easy it was for me to extract and decrypt my passwords. Twelve lines of code easy.
9. Formjacking: Hackers’ New Favorite Way to Steal Credit Card Information (And How to Avoid it)
 You’ve added your favorite products to the shopping cart. Now, it’s time to take your credit card out of your wallet and make the payment. As the site is secure and you have already done shopping on this e-commerce website in the past, you don’t think much before entering your credit/debit card details during the checkout.
You’ve added your favorite products to the shopping cart. Now, it’s time to take your credit card out of your wallet and make the payment. As the site is secure and you have already done shopping on this e-commerce website in the past, you don’t think much before entering your credit/debit card details during the checkout.
10. Your Digital Photos Can Reveal Information About You
 There is a saying that a “picture is worth a thousand words.” It was supposed to mean that an image can tell a story about the subject or about the picture. Our photos bring back memories that in itself tells us a lot about what we are viewing. In the age of digital photography that is so true because an image taken with a digital camera records information about the image as well. The problem is that the information is not only viewable to the user, but to everyone else as well. It may seem harmless at first, but so much information can be revealed by a photo once it is uploaded on the Internet to photo sharing websites, social media apps and blogs.
There is a saying that a “picture is worth a thousand words.” It was supposed to mean that an image can tell a story about the subject or about the picture. Our photos bring back memories that in itself tells us a lot about what we are viewing. In the age of digital photography that is so true because an image taken with a digital camera records information about the image as well. The problem is that the information is not only viewable to the user, but to everyone else as well. It may seem harmless at first, but so much information can be revealed by a photo once it is uploaded on the Internet to photo sharing websites, social media apps and blogs.
11. Forcing a device to disconnect from WiFi using a deauthentication attack
 Click here to view the updated version of this post:
Click here to view the updated version of this post:
12. Mine for Bitcoin with ANY Computer
 Mining is a great way to enter the cryptocurrency ecosystem. However, Bitcoin/Litecoin is almost impossible to mine for the average user. It requires expensive equipment called ASICs that are made by a controversial, centralized company called Bitmain. These ASIC chips consume high amounts of electricity, and ASIC mining farms often use cheap & ecologically-destructive coal power. These centralized mining cartels mint the vast majority of new Bitcoin, and are responsible for contentious forks of Bitcoin in order to maintain a monopoly of the network.
Mining is a great way to enter the cryptocurrency ecosystem. However, Bitcoin/Litecoin is almost impossible to mine for the average user. It requires expensive equipment called ASICs that are made by a controversial, centralized company called Bitmain. These ASIC chips consume high amounts of electricity, and ASIC mining farms often use cheap & ecologically-destructive coal power. These centralized mining cartels mint the vast majority of new Bitcoin, and are responsible for contentious forks of Bitcoin in order to maintain a monopoly of the network.
13. How one hacker stole thousands of dollars worth of cryptocurrency with a classic code injection…
 The attack detailed in this post has already been fixed by the EtherDelta team. I share this as a cautionary tale for Dapp developers and cryptocurrency users.
The attack detailed in this post has already been fixed by the EtherDelta team. I share this as a cautionary tale for Dapp developers and cryptocurrency users.
14. How to Hack Facebook Messenger: 6 Methods and Vulnerabilities
 Spyier, keylogging, and hacking using cookies are some of the most common ways Facebook Messenger accounts get hacked.
Spyier, keylogging, and hacking using cookies are some of the most common ways Facebook Messenger accounts get hacked.
15. A hacker intercepted your WiFi traffic, stole your contacts, passwords, & financial data.
 As the holiday season was in full swing, a hacker sporting a hoodie, sitting in a car with antennae on the dashboard and a computer on his lap, sat in a parking lot outside a popular cafe chain. Passersby, busied and high on holiday cheer, buzzed in and out and sometimes even stayed for a while.
As the holiday season was in full swing, a hacker sporting a hoodie, sitting in a car with antennae on the dashboard and a computer on his lap, sat in a parking lot outside a popular cafe chain. Passersby, busied and high on holiday cheer, buzzed in and out and sometimes even stayed for a while.
16. McDonalds India is leaking 2.2 million users data
 The McDonald’s India app, McDelivery is leaking personal data for more than 2.2 million of its users which includes name, email address, phone number, home address, accurate home co-ordinates and social profile links. We contacted McDelivery on 7th Feb and received an acknowledgement from a Senior IT Manager on 13th Feb (33 days ago). The issue has not been fixed yet and our continued effort to get an update for the fix after the initial acknowledgement has failed.
The McDonald’s India app, McDelivery is leaking personal data for more than 2.2 million of its users which includes name, email address, phone number, home address, accurate home co-ordinates and social profile links. We contacted McDelivery on 7th Feb and received an acknowledgement from a Senior IT Manager on 13th Feb (33 days ago). The issue has not been fixed yet and our continued effort to get an update for the fix after the initial acknowledgement has failed.
17. Why we need RISC-V
 The RISC-V (Reduced Instruction Set Computer) processor is a chip that is still in it’s infancy, but it’s a chip that everyone should be supporting. You might be wondering, what makes this chip so great?
The RISC-V (Reduced Instruction Set Computer) processor is a chip that is still in it’s infancy, but it’s a chip that everyone should be supporting. You might be wondering, what makes this chip so great?
18. 5 Best Free Proxy Servers To Visit Sites Anonymously In 2020
 A proxy server will assist you to mask your identity on the web. Perhaps you wish to access suspicious websites, bypass net censorship in your country or on your office/school network having a proxy website among your reach is very important.
A proxy server will assist you to mask your identity on the web. Perhaps you wish to access suspicious websites, bypass net censorship in your country or on your office/school network having a proxy website among your reach is very important.
19. 7 Interesting Books About Hacking to Read This Year
 Are you looking for new hacking-themed books to read this year? Of course you are. There are tons of great options out there, whether you want to learn a new skill, advance your cybersecurity career or just read a gripping hacking tale.
Are you looking for new hacking-themed books to read this year? Of course you are. There are tons of great options out there, whether you want to learn a new skill, advance your cybersecurity career or just read a gripping hacking tale.
20. Security vulnerabilities in GO-JEK
 GO-JEK is an Indonesian unicorn transport startup, often seen as the most famous and biggest startup to come out of Indonesia. GO-JEK provides services like biketaxi, cabs, food delivery, mobile payments ticket booking and more.
GO-JEK is an Indonesian unicorn transport startup, often seen as the most famous and biggest startup to come out of Indonesia. GO-JEK provides services like biketaxi, cabs, food delivery, mobile payments ticket booking and more.
21. Reverse Engineering The Medium App (and making all stories in it free)
 Last week I realized it’s been a year since my last post here. I enjoy writing my stories as much as I enjoy reading others’, but only if I consider them interesting enough, and that’s a high bar honestly. I’ve been into reverse engineering Android apps recently, so I tried to think of a project that could involve that field, along with being interesting to the readers on Medium.
Last week I realized it’s been a year since my last post here. I enjoy writing my stories as much as I enjoy reading others’, but only if I consider them interesting enough, and that’s a high bar honestly. I’ve been into reverse engineering Android apps recently, so I tried to think of a project that could involve that field, along with being interesting to the readers on Medium.
22. LeakLooker: Find Open Databases in Seconds

With LeakLooker you can find publicly open MongoDB, CouchDB and Elasticsearch database, it also includes Kibana instances. Script parses results from Shodan, excluding empty and compromised databases. Everything is sorted and presented in clickable way.
23. Writing a Basic Keylogger for macOS in Python
 ⚠️This post is for educational purposes only⚠️
⚠️This post is for educational purposes only⚠️
24. afl-unicorn: Fuzzing Arbitrary Binary Code
 American Fuzzy Lop (AFL) is awesome. It’s easily the best thing out there for quickly doing cutting-edge fuzzing analysis on command line applications. But what about the situations where accessing the stuff you want to fuzz via command line isn’t so simple? Lots of times you can write a test harness (or maybe use libFuzzer instead), but what if you could just emulate the parts of the code that you want to fuzz and still get all the coverage-based advantages of AFL? For example, maybe you want to fuzz a parsing function from an embedded system that receives input via RF and isn’t easily debugged. Maybe the code you’re interested in is buried deep within a complex, slow program that you can’t easily fuzz through any traditional tools.
American Fuzzy Lop (AFL) is awesome. It’s easily the best thing out there for quickly doing cutting-edge fuzzing analysis on command line applications. But what about the situations where accessing the stuff you want to fuzz via command line isn’t so simple? Lots of times you can write a test harness (or maybe use libFuzzer instead), but what if you could just emulate the parts of the code that you want to fuzz and still get all the coverage-based advantages of AFL? For example, maybe you want to fuzz a parsing function from an embedded system that receives input via RF and isn’t easily debugged. Maybe the code you’re interested in is buried deep within a complex, slow program that you can’t easily fuzz through any traditional tools.
25. Understanding the Deep & Dark Web

26. Deep Web & Dark Web Explained..!!!
27. AI: Scary for the Right Reasons
 Artificial intelligence, AI, has grabbed headlines, hype, and even consternation at the beast we are unleashing. Every powerful technology can be used for good and bad, be it nuclear or biotechnology, and the same is true for AI. While much of the public discourse from the likes of Elon Musk and Stephen Hawking reflects on sci-fi like dystopian visions of overlord AI’s gone wrong (a scenario certainly worth discussing), there is a much more immediate threat when it comes to AI. Long before AI goes uncontrollable or takes over jobs, there lurks a much larger danger: AI in the hands of governments and/or bad actors used to push self-interested agendas against the greater good.
Artificial intelligence, AI, has grabbed headlines, hype, and even consternation at the beast we are unleashing. Every powerful technology can be used for good and bad, be it nuclear or biotechnology, and the same is true for AI. While much of the public discourse from the likes of Elon Musk and Stephen Hawking reflects on sci-fi like dystopian visions of overlord AI’s gone wrong (a scenario certainly worth discussing), there is a much more immediate threat when it comes to AI. Long before AI goes uncontrollable or takes over jobs, there lurks a much larger danger: AI in the hands of governments and/or bad actors used to push self-interested agendas against the greater good.
28. How does Tor really work?
 I read the whitepaper so you don’t have to.
I read the whitepaper so you don’t have to.
29. 5G Networks Can Change The Way We Live: For Better or Worse?
 The advances in wireless communications has led to an exponential growth in mobile devices i.e. smartphones. The deployment of 4G and LTE (Long Term Evolution) networks has delivered us more rich content, from video streaming to live gaming. It is taking its toll on bandwidth, which now needs to be addressed as demand grows. This time around a new class of applications that are bandwidth intensive like VR (Virtual Reality), AR (Augmented Reality) and OTT will require it. The telecom industry have specified a new standard called 5G to meet the growth of network demands. High speed data communications made possible by more bandwidth sounds like an excellent business proposition for wireless carriers to expand their networks, appease users and gain more subscribers while generating more revenues.
The advances in wireless communications has led to an exponential growth in mobile devices i.e. smartphones. The deployment of 4G and LTE (Long Term Evolution) networks has delivered us more rich content, from video streaming to live gaming. It is taking its toll on bandwidth, which now needs to be addressed as demand grows. This time around a new class of applications that are bandwidth intensive like VR (Virtual Reality), AR (Augmented Reality) and OTT will require it. The telecom industry have specified a new standard called 5G to meet the growth of network demands. High speed data communications made possible by more bandwidth sounds like an excellent business proposition for wireless carriers to expand their networks, appease users and gain more subscribers while generating more revenues.
30. How to Hack Your Alexa using a Voice Command-SQL Injection
 Based on your previous coverage of similar topics, we thought you may be interested in this recently discovered voice activation device hack, and a new technique we call Voice-Command SQL Injection.
Based on your previous coverage of similar topics, we thought you may be interested in this recently discovered voice activation device hack, and a new technique we call Voice-Command SQL Injection.
31. afl-unicorn: Part 2 — Fuzzing the ‘Unfuzzable’
 Unicorn Mode as demonstrated in my previous article is not overly useful on the surface. It has lots of limitations that make it clumsy and slow to employ against most real-world situations. For example, what if the binary you want to emulate calls an imported library function that is likely to call into the kernel such as malloc() or printf()? What if the code you want to fuzz is highly stateful, and requires lots of memory regions (heap allocations, stack pointers, global variables, etc.) that aren’t known until run-time? In fact, just about the only straightforward use of it that I’ve found is when working with flat embedded run-time system memory snapshots recovered from firmware by a debugger.
Unicorn Mode as demonstrated in my previous article is not overly useful on the surface. It has lots of limitations that make it clumsy and slow to employ against most real-world situations. For example, what if the binary you want to emulate calls an imported library function that is likely to call into the kernel such as malloc() or printf()? What if the code you want to fuzz is highly stateful, and requires lots of memory regions (heap allocations, stack pointers, global variables, etc.) that aren’t known until run-time? In fact, just about the only straightforward use of it that I’ve found is when working with flat embedded run-time system memory snapshots recovered from firmware by a debugger.
32. What is the difference between Information Security and Information Technology?

33. Wifi Cracking
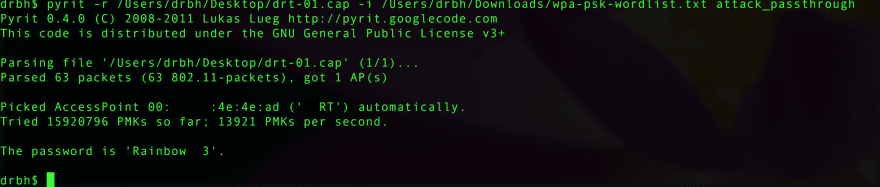 Hacking into Networks has a long history. Ever since the advent of the wireless networking, and obvious challenge is securing pieces of data over this non visible network. There have been various attempts at securing this phenom. These security attempts come in a few flavors called:
Hacking into Networks has a long history. Ever since the advent of the wireless networking, and obvious challenge is securing pieces of data over this non visible network. There have been various attempts at securing this phenom. These security attempts come in a few flavors called:
34. Simple Image Steganography in Python
 In this post I’ll demonstrate how to achieve simple image steganography using Python. All digital file formats use internal structures and schemas, therefore unique implementations are required for different mediums, and often for different formats within those mediums.
In this post I’ll demonstrate how to achieve simple image steganography using Python. All digital file formats use internal structures and schemas, therefore unique implementations are required for different mediums, and often for different formats within those mediums.
35. IoT without Internet… how does it affect its functionality?
 The Internet of things (IoT) is the network of devices such as vehicles, and home appliances that contain electronics, software, sensors, actuators, and connectivity which allows these things to connect, interact and exchange data. (Thank you for that definition, Wikipedia!)
The Internet of things (IoT) is the network of devices such as vehicles, and home appliances that contain electronics, software, sensors, actuators, and connectivity which allows these things to connect, interact and exchange data. (Thank you for that definition, Wikipedia!)
36. SMS Spoofing Used to Swindle Retailers & Merchants
 Websites that allow an individual to send a text message to any number are being used by fraudsters to send fake transaction messages impersonating a legitimate bank. The ability of these websites to modify the sender name of the SMS, i.e. to spoof any genuine entity, is what the fraudsters exploit for their benefits and typically form part of a larger scam chain. Numerous cases have been brought to the authorities regarding such SMS spoofing websites, which have called for legal proceedings against such service providers. These kinds of websites have continued to thrive exponentially. The victims of such scams are typically retailers who deal with high-end electronic equipment, jewelry, branded merchandise etc. A fraudster may initiate the scam by visiting a store and proceeding to select multiple items. The aim is to select items that amount to a large sum, thereby creating a situation wherein the fraudster pretends to have insufficient cash in hand to complete the purchase. The fraudster then requests for the bank details of the outlet so he can perform the bank transfer immediately. Once the bank details are in his possession, the fraudster accesses a SMS spoofing website, using it to send a message to the merchant’s mobile number which he had attained prior to the attack. This text message utilizes the victim’s bank name as the SMS sender, stating that his/her account has been accredited with a total sum owed for the items bought. The message would consist of the outlet’s account number (hashed till the last 4 digits), amount transferred and date of transaction. The structure of the message is intended to dupe the SMS recipient by prompting them to complete the purchase and handing over the merchandise. New elaborate schemes have been identified recently that show the SMS containing a landline number pretending to be the bank which is, in fact controlled by the fraudsters. A few moments after the SMS is received, a fake call is made to the SMS recipient pretending to verify the transaction and suggesting that the purpose of the call is to verify and check for any fraudulent activity. These messages may also have URL links which could be malicious. Further investigation has revealed that the recipient mobile number and bank details collected from the victim are used in other scams as well. A more prevalent scam involves a call placed from a fake landline, pretending to be from the bank asking to verify the victim’s information so that his/her records are up to date.
Websites that allow an individual to send a text message to any number are being used by fraudsters to send fake transaction messages impersonating a legitimate bank. The ability of these websites to modify the sender name of the SMS, i.e. to spoof any genuine entity, is what the fraudsters exploit for their benefits and typically form part of a larger scam chain. Numerous cases have been brought to the authorities regarding such SMS spoofing websites, which have called for legal proceedings against such service providers. These kinds of websites have continued to thrive exponentially. The victims of such scams are typically retailers who deal with high-end electronic equipment, jewelry, branded merchandise etc. A fraudster may initiate the scam by visiting a store and proceeding to select multiple items. The aim is to select items that amount to a large sum, thereby creating a situation wherein the fraudster pretends to have insufficient cash in hand to complete the purchase. The fraudster then requests for the bank details of the outlet so he can perform the bank transfer immediately. Once the bank details are in his possession, the fraudster accesses a SMS spoofing website, using it to send a message to the merchant’s mobile number which he had attained prior to the attack. This text message utilizes the victim’s bank name as the SMS sender, stating that his/her account has been accredited with a total sum owed for the items bought. The message would consist of the outlet’s account number (hashed till the last 4 digits), amount transferred and date of transaction. The structure of the message is intended to dupe the SMS recipient by prompting them to complete the purchase and handing over the merchandise. New elaborate schemes have been identified recently that show the SMS containing a landline number pretending to be the bank which is, in fact controlled by the fraudsters. A few moments after the SMS is received, a fake call is made to the SMS recipient pretending to verify the transaction and suggesting that the purpose of the call is to verify and check for any fraudulent activity. These messages may also have URL links which could be malicious. Further investigation has revealed that the recipient mobile number and bank details collected from the victim are used in other scams as well. A more prevalent scam involves a call placed from a fake landline, pretending to be from the bank asking to verify the victim’s information so that his/her records are up to date.
37. 6 Cybersecurity Tools You’ll Need to Know About in 2019
 It doesn’t take such a deep dive into 2018’s most important tech trends to understand how vital cybersecurity will be in the coming year. With the idea of cybersecurity taking a central role in US electoral politics and the world’s most sophisticated platforms demonstrating their inability to thwart savvy hackers, 2019 and the plethora of events scheduled for the year are in a precarious position.
It doesn’t take such a deep dive into 2018’s most important tech trends to understand how vital cybersecurity will be in the coming year. With the idea of cybersecurity taking a central role in US electoral politics and the world’s most sophisticated platforms demonstrating their inability to thwart savvy hackers, 2019 and the plethora of events scheduled for the year are in a precarious position.
38. The NuID Ecosystem: An Improved Identity Layer Putting Identity Ownership In Users’ Hands
 The internet grew without an identity layer, meaning it grew without a reliable way of knowing or verifying who you were connecting to which can be dangerous.
The internet grew without an identity layer, meaning it grew without a reliable way of knowing or verifying who you were connecting to which can be dangerous.
39. EternalPulsar — A practical example of a made up name
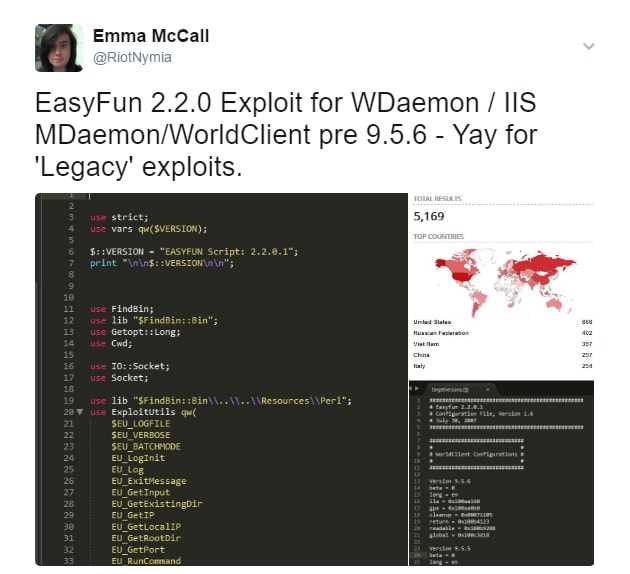 Yesterday we were talking about this weekends ShadowBrokers dump (I suggest you read that before continuing here) and noted that within the approximately 32 exploit dump there were several that caught our eye, and have been super fun over the past few days.
Yesterday we were talking about this weekends ShadowBrokers dump (I suggest you read that before continuing here) and noted that within the approximately 32 exploit dump there were several that caught our eye, and have been super fun over the past few days.
40. The Difference Between Risk Assessment & Risk Analysis
 The more you delve deeper into information compliance, the more likely you are to begin humming the term risk in a manner that is akin to how Jan Brady would shout, “Marcia! Marcia! MARCIA!” You may have heard of this term a lot, to the point that it almost loses meaning. Nonetheless, you should know that the difference between risk analysis and risk assessment could be the difference between security control and data breach.
The more you delve deeper into information compliance, the more likely you are to begin humming the term risk in a manner that is akin to how Jan Brady would shout, “Marcia! Marcia! MARCIA!” You may have heard of this term a lot, to the point that it almost loses meaning. Nonetheless, you should know that the difference between risk analysis and risk assessment could be the difference between security control and data breach.
41. Myths and Legends of SPF
 SPF is an abbreviation for Sender Policy Framework (SPF) for Authorizing Use of Domains in Email. Email domains use this protocol to specify which Internet hosts are authorized to use this domain in the SMTP HELO and MAIL FROM commands. You do not have to use any additional software to publish the SPF policy and therefore this procedure is extremely simple: Simply add a TXT record containing the policy to the DNS zone. An example of this type of entry is given at the end of this article. There are numerous manuals and even online constructors for working with SPF.
SPF is an abbreviation for Sender Policy Framework (SPF) for Authorizing Use of Domains in Email. Email domains use this protocol to specify which Internet hosts are authorized to use this domain in the SMTP HELO and MAIL FROM commands. You do not have to use any additional software to publish the SPF policy and therefore this procedure is extremely simple: Simply add a TXT record containing the policy to the DNS zone. An example of this type of entry is given at the end of this article. There are numerous manuals and even online constructors for working with SPF.
42. How to Detect if an iOS Device is Jailbroken
 Thanks to the mobile era we have mobile apps for everything these days. Every business from a barber shop to huge retailers has apps so that they can be closer to their customers. On one hand, we really leverage this convenience but on the other hand, there are risks of exposing a lot of confidential information while using these apps. And it becomes very vital when dealing with payments and other sensitive information.
Thanks to the mobile era we have mobile apps for everything these days. Every business from a barber shop to huge retailers has apps so that they can be closer to their customers. On one hand, we really leverage this convenience but on the other hand, there are risks of exposing a lot of confidential information while using these apps. And it becomes very vital when dealing with payments and other sensitive information.
43. How To Find Out If A Hacker Has Attacked You
 Computer crimes are all those online attacks carried out by a hacker whose purpose is to breach a computer system in order to gain financial gain in some way
Computer crimes are all those online attacks carried out by a hacker whose purpose is to breach a computer system in order to gain financial gain in some way
44. [CTF Series #1] The Reverse Engineering Challenge
45. What is 2-Factor Authentication and Why Should You Care?
 In the digital world that we live in, our virtual identity has become as important as the real one. We are becoming more and more aware of our virtual presence, social activity and how we act and how we are perceived online.
In the digital world that we live in, our virtual identity has become as important as the real one. We are becoming more and more aware of our virtual presence, social activity and how we act and how we are perceived online.
46. The Ultimate Security Guide for Cryptocurrency Investors
47. PlayerUnknown’s Battlegrounds Main Menu Is Vulnerable to Hacking
 Update: This security hole has been plugged. See my next post for details.
Update: This security hole has been plugged. See my next post for details.
48. Ditch your SSH keys and enable AWS SSM!
 If you manage AWS for an organization, big or small, chances are you have several Secure Shell (SSH) keys laying around you hardly use, OR WORSE, you don’t recall the account the key was made for. SSH key management is a rabbit hole in itself and most people understand the security concerns that arise with improper SSH key hygiene. Luckily for us, there is a way to bid farewell to the the cumbersome practice of using SSH to remote into an EC2 instance. Allow me to introduce you the AWS service, Systems Manager (SSM).
If you manage AWS for an organization, big or small, chances are you have several Secure Shell (SSH) keys laying around you hardly use, OR WORSE, you don’t recall the account the key was made for. SSH key management is a rabbit hole in itself and most people understand the security concerns that arise with improper SSH key hygiene. Luckily for us, there is a way to bid farewell to the the cumbersome practice of using SSH to remote into an EC2 instance. Allow me to introduce you the AWS service, Systems Manager (SSM).
49. How to Protect Your Netflix Account from Getting Hacked
 Netflix accounts getting hacked are the least bit of anyone’s concern. Not because it doesn’t mean anything to us, but we anticipate little harm from it. After all, what more can a hacker do than to watch a few titles, get to see their favorite shows or movies? But that’s not always the case. We have left this issue unsupervised for far too long, and there is harm more significant than we give credit for.
Netflix accounts getting hacked are the least bit of anyone’s concern. Not because it doesn’t mean anything to us, but we anticipate little harm from it. After all, what more can a hacker do than to watch a few titles, get to see their favorite shows or movies? But that’s not always the case. We have left this issue unsupervised for far too long, and there is harm more significant than we give credit for.
50. Cyber Security Trends and Threats to Watch for in 2018

51. Is WhatsApp Safe?
 WhatsApp is the most popular messenger owned by Facebook. According to the official stats, the number of WhatsApp active users has reached 1 billion in 2020. Just imagine, approximately 65 million messages are sent via this social app daily. Since the app is so popular, it’s very attractive for hackers. In this article, I’ll tell you about the major WhatsApp security threats, which will help you protect your chats and shared media from hackers, WhatsApp spy apps, and keylogging software.
WhatsApp is the most popular messenger owned by Facebook. According to the official stats, the number of WhatsApp active users has reached 1 billion in 2020. Just imagine, approximately 65 million messages are sent via this social app daily. Since the app is so popular, it’s very attractive for hackers. In this article, I’ll tell you about the major WhatsApp security threats, which will help you protect your chats and shared media from hackers, WhatsApp spy apps, and keylogging software.
52. Do ATMs running Windows XP pose a security risk? You can bank on it!
 I originally wrote this article for CSO back in February 2014. Even though my piece is now three years old, unfortunately this issue is still timely and relevant! It’s 2017, and ATMs around the world are still running Windows XP embedded, long after Microsoft ceased support with security and stability patches. See these more recent articles that other people have written for more information:
I originally wrote this article for CSO back in February 2014. Even though my piece is now three years old, unfortunately this issue is still timely and relevant! It’s 2017, and ATMs around the world are still running Windows XP embedded, long after Microsoft ceased support with security and stability patches. See these more recent articles that other people have written for more information:
53. How I hacked modern Vending Machines
 Indisputably, Vending Machines are objects of cult. Delicious morsels of Hackers, always. In the beginning they worked offline with coins only, then, NFC- keys/cards models started spreading. If I say “COGES” I’m sure that better times will come to someone’s mind. But… In a bunch of years things changed radically. You distract and a moment after, find the world superseded by things connected to the internet…
Indisputably, Vending Machines are objects of cult. Delicious morsels of Hackers, always. In the beginning they worked offline with coins only, then, NFC- keys/cards models started spreading. If I say “COGES” I’m sure that better times will come to someone’s mind. But… In a bunch of years things changed radically. You distract and a moment after, find the world superseded by things connected to the internet…
54. A Guide to Password Hashing: How to Keep your Database Safe
 Hashing algorithms are one-way functions. They take any string and turn it into a fixed-length “fingerprint” that is unable to be reversed. This means that if your data in your database is compromised, the hacker cannot get the user’s passwords if they were hashed well because at no point were they ever stored on the drive without being in their hashed form.
Hashing algorithms are one-way functions. They take any string and turn it into a fixed-length “fingerprint” that is unable to be reversed. This means that if your data in your database is compromised, the hacker cannot get the user’s passwords if they were hashed well because at no point were they ever stored on the drive without being in their hashed form.
55. Samsung Leaking Customer Information
 About four months ago, I ordered a new TV directly from Samsung’s online store. A few days later, I received a tracking link via email.
About four months ago, I ordered a new TV directly from Samsung’s online store. A few days later, I received a tracking link via email.
56. Domain Fronting 101: What is Domain Fronting and How Does it Work?
 Domain fronting is one technique that hackers use to bypass internet censorship. This method is used to access restricted sites that would typically be blocked.
Domain fronting is one technique that hackers use to bypass internet censorship. This method is used to access restricted sites that would typically be blocked.
57. What is Hacking? Common Objectives, Types, and How to Guard Against It
 Hacking is the process of gaining unauthorized access into a computer system, or group of computer systems. This is done through cracking of passwords and codes which gives access to the systems. Cracking is the term which specifies the method by which the password or code is obtained. The person who undertakes hacking is known as the hacker. The hacking can be done on single systems, a group of systems, an entire LAN network, a website or a social media site or an email account. The access to a password is obtained by the hacker through password cracking algorithms programs.
Hacking is the process of gaining unauthorized access into a computer system, or group of computer systems. This is done through cracking of passwords and codes which gives access to the systems. Cracking is the term which specifies the method by which the password or code is obtained. The person who undertakes hacking is known as the hacker. The hacking can be done on single systems, a group of systems, an entire LAN network, a website or a social media site or an email account. The access to a password is obtained by the hacker through password cracking algorithms programs.
58. How to Hack Instagram: 5 Common Vulnerabilities
 There are 5 common methods attackers may use to hack Instagram accounts such as weak passwords, phishing email, OS vulnerabilities & zero day vulnerabilities.
There are 5 common methods attackers may use to hack Instagram accounts such as weak passwords, phishing email, OS vulnerabilities & zero day vulnerabilities.
59. 6 Domain Name Registration Drivers in Q2 2022
 WhoisXML API researchers identified six notable domain registration drivers for Q2 2022. Check an overview of the key findings and takeaways.
WhoisXML API researchers identified six notable domain registration drivers for Q2 2022. Check an overview of the key findings and takeaways.
60. We survived a DDoS attack that peaked at 250k requests-per-second. It cost us $10
 With the surge in interest in cryptocurrencies, the door has been opened for bad actors trying to crack blockchain-related businesses. The industry has been among the fifth most attacked by DDoS since the second half of 2017, and it doesn’t look like it’s losing its position anytime soon. Arranging a black market DDoS attack can cost as little as $7 per hour, while the affected company can lose thousands — or even millions — of dollars.
With the surge in interest in cryptocurrencies, the door has been opened for bad actors trying to crack blockchain-related businesses. The industry has been among the fifth most attacked by DDoS since the second half of 2017, and it doesn’t look like it’s losing its position anytime soon. Arranging a black market DDoS attack can cost as little as $7 per hour, while the affected company can lose thousands — or even millions — of dollars.
61. How to Hack Bluetooth Devices: 5 Common Vulnerabilities
 This article discusses the five common vulnerabilities (BlueBorne, Bluesnarfing, Bluejacking, BIAS & Bluebugging) that allow hackers to hack Bluetooth devices.
This article discusses the five common vulnerabilities (BlueBorne, Bluesnarfing, Bluejacking, BIAS & Bluebugging) that allow hackers to hack Bluetooth devices.
62. How to Hack TikTok Accounts : 5 Common Vulnerabilities
 As TikTok has become a popular platform, it has also become an easy target for hackers. These are the 5 common vulnerabilities that can be used to hack TikTok.
As TikTok has become a popular platform, it has also become an easy target for hackers. These are the 5 common vulnerabilities that can be used to hack TikTok.
63. How Twitter Can Satisfy Elon Musk's Request for Fake Account Clarity
 Twitter claims that less than 5% of users are fake. Is Elon Musk right to be skeptical? Until a proper test is run, nobody truly knows how bad the situation is.
Twitter claims that less than 5% of users are fake. Is Elon Musk right to be skeptical? Until a proper test is run, nobody truly knows how bad the situation is.
64. Man in the Middle iOS Attacks: The Danger of Relying on a Single Layer of Security
 Author Note: This write-up will not examine any new vulnerability. Rather, it explores a common methodology used in trivially hacking iOS apps, in which you perform a man-in-the-middle (MitM) attack on yourself.
Author Note: This write-up will not examine any new vulnerability. Rather, it explores a common methodology used in trivially hacking iOS apps, in which you perform a man-in-the-middle (MitM) attack on yourself.
65. Delete These Apps to Speed and Space up Your Phone
 Smartphones, the smart technology at our fingertips has geared our lifestyles to optimal levels.
Smartphones, the smart technology at our fingertips has geared our lifestyles to optimal levels.
66. 5 Best Cybersecurity Books for Beginners
 These are the five cybersecurity books that you should start with if you are considering a career within the industry.
These are the five cybersecurity books that you should start with if you are considering a career within the industry.
67. The Rise of Zero-Trust Architecture
 What is Zero-Trust Architecture and why is it Relevant Today?Breaking Down Zero Trust Architecture:
What is Zero-Trust Architecture and why is it Relevant Today?Breaking Down Zero Trust Architecture:
68. Windows Sticky Keys Exploit: The War Veteran That Never Dies
 Did you ever hear of Sticky Keys Exploit? You probably did, since it has been known for ages. It was used as an exploit many times, fought in many windows versions, and it has never been killed. That’s why I’m calling it the “War Veteran”, although it never retired…
Did you ever hear of Sticky Keys Exploit? You probably did, since it has been known for ages. It was used as an exploit many times, fought in many windows versions, and it has never been killed. That’s why I’m calling it the “War Veteran”, although it never retired…
69. 5 Best Browser Extensions For Protecting Your Privacy Online
 It is essential for every internet user to comprehend the importance of browser security capabilities to assure they browse the internet safely. Protecting your browser might mean limited functionality of some web sites, but it’ll shield your most sensitive information as well.
It is essential for every internet user to comprehend the importance of browser security capabilities to assure they browse the internet safely. Protecting your browser might mean limited functionality of some web sites, but it’ll shield your most sensitive information as well.
70. How I hacked the MIT Technology Review website to gain unlimited online access to all their stories
 DISCLAIMER: All data and information provided in this article are for informational purposes only. The main goal is to increase security awareness, teach about information security, countermeasures and give readers information on how to implement a safe and functional system (in our case, a website). If you plan to use the information for illegal purposes, please leave this website now. I cannot be held responsible for any misuse of the given information. I do not use this method to avoid paying and neither should you.
DISCLAIMER: All data and information provided in this article are for informational purposes only. The main goal is to increase security awareness, teach about information security, countermeasures and give readers information on how to implement a safe and functional system (in our case, a website). If you plan to use the information for illegal purposes, please leave this website now. I cannot be held responsible for any misuse of the given information. I do not use this method to avoid paying and neither should you.
71. How I Hacked DePauw University Using Hidden Inputs
 For the past month I have been in a conflict with my undergrad university, DePauw, over a vulnerability I found involving university provided student mailboxes. I have been threatened while also being told that they are grateful for what I’ve done.
For the past month I have been in a conflict with my undergrad university, DePauw, over a vulnerability I found involving university provided student mailboxes. I have been threatened while also being told that they are grateful for what I’ve done.
72. How Facebook tracks you on Android (even if you don't have a Facebook account)
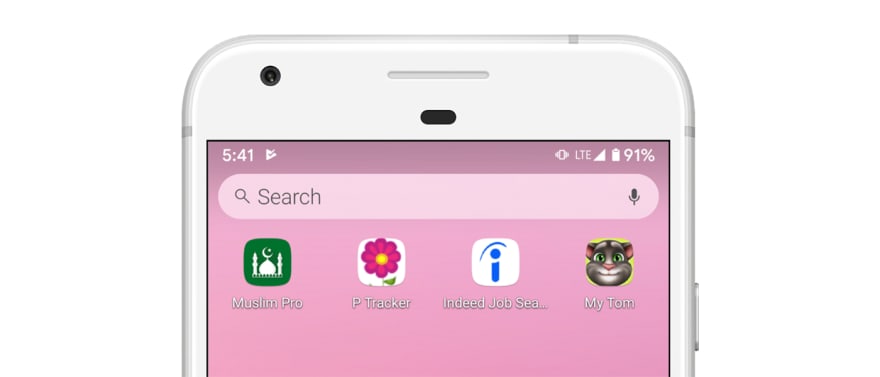 Suppose you’ve picked up an Android phone on the street and you saw the 4 apps above. Can you guess the profile of the phone user?
Suppose you’ve picked up an Android phone on the street and you saw the 4 apps above. Can you guess the profile of the phone user?
73. Hacker to Security Pro! On the Shoulders of #InfoSec Giants
 I want to do my part to demystify IT Security — to exclaim to the world that it is not rocket science! It turns out the trick is just to start. Start anywhere.
I want to do my part to demystify IT Security — to exclaim to the world that it is not rocket science! It turns out the trick is just to start. Start anywhere.
74. Inside a Hacker's Backpack: Gadgets, Tips, and Tricks for Hackers
 Not ever hack job requires just a laptop and some software to gain privileges into a system. Sometimes, something extra is required to make the job very easy
Not ever hack job requires just a laptop and some software to gain privileges into a system. Sometimes, something extra is required to make the job very easy
75. Risk DAO Conducts Technology Risk Assessment on Aurigami Finance
 Aurigami conducted a risk analysis of the protocol's risk parameters in an effort to reduce technological risks and improve capital efficiency.
Aurigami conducted a risk analysis of the protocol's risk parameters in an effort to reduce technological risks and improve capital efficiency.
76. How to Hack Android Phones
 There's a big difference between hackers (people who like to experiment with computer systems to make them do unintended things) and attackers .
There's a big difference between hackers (people who like to experiment with computer systems to make them do unintended things) and attackers .
77. What are the Primary Security Architectures in use Today?
 In my latest article about “The Rise Of Zero Trust Architecture”, I wrote about the broad and rapid adoption of this relatively new concept in the world of cybersecurity. However, there are still several other security architectures which are in use today:
In my latest article about “The Rise Of Zero Trust Architecture”, I wrote about the broad and rapid adoption of this relatively new concept in the world of cybersecurity. However, there are still several other security architectures which are in use today:
78. The Hidden Danger of QR Codes
 It would seem, what danger can a QR code pose? It turns out that you can even lose your cryptocurrency as well as internet logins because of QR code attacks
It would seem, what danger can a QR code pose? It turns out that you can even lose your cryptocurrency as well as internet logins because of QR code attacks
79. How to Hack Facebook Accounts: 5 Common Vulnerabilities
 There are 5 common vulnerabilities that attackers can exploit to hack Facebook accounts. They include weak passwords, phishing, remote loggers, MITM, and DoS.
There are 5 common vulnerabilities that attackers can exploit to hack Facebook accounts. They include weak passwords, phishing, remote loggers, MITM, and DoS.
80. Cryptography + Malware = Ransomware
 When you combine cryptography with malware, you get a very dangerous mix of problems. This is a type of computer virus that goes by another name, “ransomware”. This type of virus is part of a field of study called “cryptovirology”. Through the use of techniques called phishing, a threat actor sends the ransomware file to an unknowing victim. If the file is opened it will execute the virus payload, which is malicious code. The ransomware runs the code that encrypts user data on the infected computer or host. The data are user files like documents, spreadsheets, photos, multimedia files and even confidential records. The ransomware targets your personal computer files and applies an encryption algorithm like RSA which makes the file unaccessible. The only way to access them is if the user pays a ransom to the threat actor by following instructions which appear encoded into the encrypted files. Thus it is called ransomware, because a form of payment is demanded in order to fix the problem.
When you combine cryptography with malware, you get a very dangerous mix of problems. This is a type of computer virus that goes by another name, “ransomware”. This type of virus is part of a field of study called “cryptovirology”. Through the use of techniques called phishing, a threat actor sends the ransomware file to an unknowing victim. If the file is opened it will execute the virus payload, which is malicious code. The ransomware runs the code that encrypts user data on the infected computer or host. The data are user files like documents, spreadsheets, photos, multimedia files and even confidential records. The ransomware targets your personal computer files and applies an encryption algorithm like RSA which makes the file unaccessible. The only way to access them is if the user pays a ransom to the threat actor by following instructions which appear encoded into the encrypted files. Thus it is called ransomware, because a form of payment is demanded in order to fix the problem.
81. I hacked 40,000 passwords with Python. Yours might've been one of them.
 Remember the good old days when you were passing love notes to your crush across the classroom?
Remember the good old days when you were passing love notes to your crush across the classroom?
82. How to Map Your Home Networks Using NMAP
 Here's to learning basics of networking and an awesome tool called NMAP
Here's to learning basics of networking and an awesome tool called NMAP
83. Why You Should Protect Your Cell Phone Number and How to Do It
 With only your cell phone number hackers become you!
With only your cell phone number hackers become you!
84. Kali Linux vs Parrot Security OS: Operating System for Penetration Testing in a Nutshell

85. IT Audit | Step-by-Step Guide
 In 2020, an IT audit is important for all organizations. It provides insights into the business’ IT infrastructure and how it can be improved.
In 2020, an IT audit is important for all organizations. It provides insights into the business’ IT infrastructure and how it can be improved.
86. Facts You Probably Didn't Know About The Dark Web
 The dark web refers to encrypted online content that is not indexed by conventional search engines. Sometimes, the dark web is also called the dark net.
The dark web refers to encrypted online content that is not indexed by conventional search engines. Sometimes, the dark web is also called the dark net.
87. Why Governments Use Mass Surveillance—And What To Do About It
 “I’m not a terrorist, why should I be worried about my data being monitored?”
“I’m not a terrorist, why should I be worried about my data being monitored?”
88. The Infamous Hacker Bjorka's Top 7 Leaks that Shocked the Public
 In addition to sharing personal data of essential people in Indonesia, Bjorka also studied death cases such as Munir and Brigadier J. Who was Bjorka?
In addition to sharing personal data of essential people in Indonesia, Bjorka also studied death cases such as Munir and Brigadier J. Who was Bjorka?
89. Part 2: How to stop me harvesting credit card numbers and passwords from your site
 I wrote a post recently describing how I distributed malicious code that gathers credit card numbers and passwords from thousands of sites in a way that’s quite difficult to detect.
I wrote a post recently describing how I distributed malicious code that gathers credit card numbers and passwords from thousands of sites in a way that’s quite difficult to detect.
90. 7 Cybersecurity Skills in High Demand
 Is there any more called-for tech specialist these days than one schooled in cybersecurity? It seems like every business is, crying out for skilled individuals with a super-charged cybersecurity salary to boot. As networks, systems, and software become more complex, this makes the field of cybersecurity more diversified. In turn, this means the that the in demand cybersecurity jobs are becoming more niche. It’s no longer always a requirement to be the sys admin of cybersecurity.
Is there any more called-for tech specialist these days than one schooled in cybersecurity? It seems like every business is, crying out for skilled individuals with a super-charged cybersecurity salary to boot. As networks, systems, and software become more complex, this makes the field of cybersecurity more diversified. In turn, this means the that the in demand cybersecurity jobs are becoming more niche. It’s no longer always a requirement to be the sys admin of cybersecurity.
91. Real-Life Software Security Vulnerabilities And What You Can Do To Stay Safe
 Most important aspects of our life including our finance, identity, and healthcare now depend on code. Software security is now a critical aspect for not just companies, but individuals as well.
Most important aspects of our life including our finance, identity, and healthcare now depend on code. Software security is now a critical aspect for not just companies, but individuals as well.
cybersecurity
Photo credit, HackerNoon AI

![Cover image for Everything You Need to Know About Cybersecurity [91 Blog Posts]](https://media.dev.to/cdn-cgi/image/width=1000,height=420,fit=cover,gravity=auto,format=auto/https%3A%2F%2Fdev-to-uploads.s3.amazonaws.com%2Fuploads%2Farticles%2Ftxqaj5wjmmpz7p4p09h3.png)








Latest comments (0)