Secrets are the backbone of how developers work in today's data-driven and service world. Password manager apps like 1Password, Lastpass, and Bitwarden have been keeping our passwords safe for years.
Developers have not stuck with the same approach when it comes to secrets though. In the best-case scenario secrets are encrypted and worst case they are plaintext stored within config files.
With that in mind, this article will aim to help you source secrets from your 1Password vault locally leading to better security and a single source of truth.
First thing is to make sure you have the 1Password CLI installed and configured. Now we can start configuring our .env file to load things from the vault.
Here I've created an API Credential that lives in the "Secrets" vault which I've named "Demo Secret".
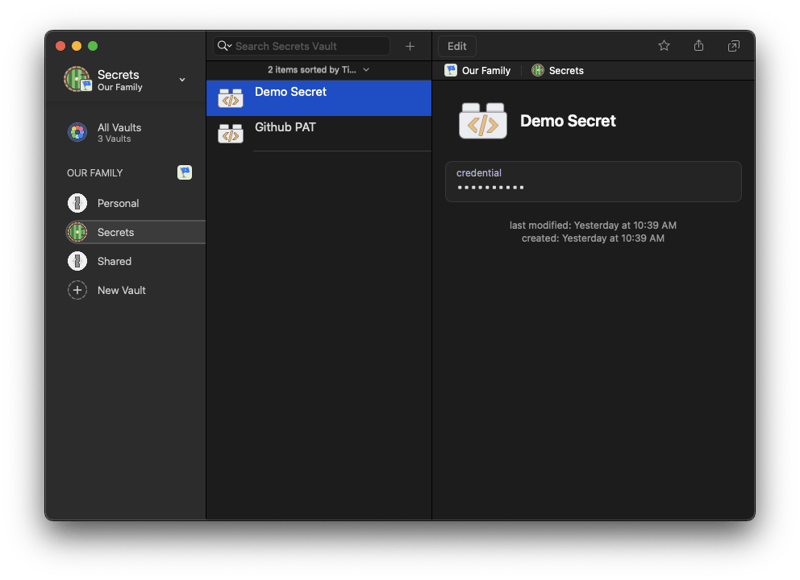
We can access this secret using the following schema
op://vault-name/item-name/[section-name/]field-name
Create a file in your home directory somewhere, I'll be using $HOME/personal/.env but feel free to change this.
Example:
SECRET_DEMO="op://secrets/demo secret/credential"
Now we'll want to create a nice shell helper function that can go into your profile.
# added to my $HOME/.zshrc file
# where we will store the env file
ENV_PATH=$HOME/personal/.env
# call this function anything you'd
function sec {
# see if we are logged in, will return exit code > 0 if not
op whoami
# if we are logged skip if not ask for master password
if [[ $? != 0 ]]; then
eval $(op signin)
fi
# this will inject the env vars we defined in our .env file
op run --env-file=$ENV_PATH -- $@
}
Make sure to reload your shell so we have access to the new sec helper function we made.
Now clone the demo repo, change into the new directory, and start the app with the sec util.
# clone the demo project
git clone https://github.com/Hacksore/demo-1pass-secrets.git
# change directory
cd demo-1pass-secrets
# start with the prefixed util
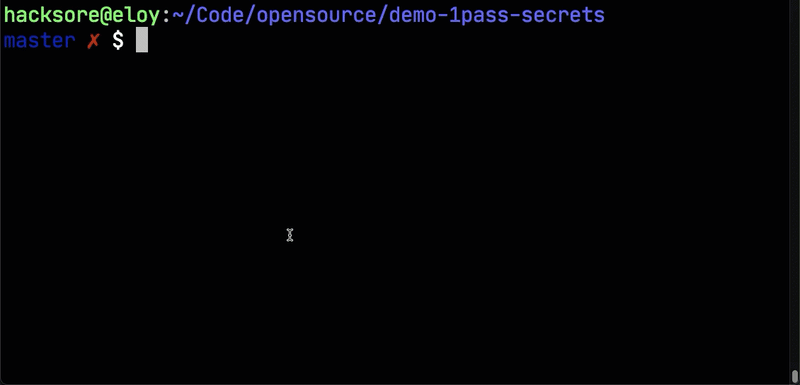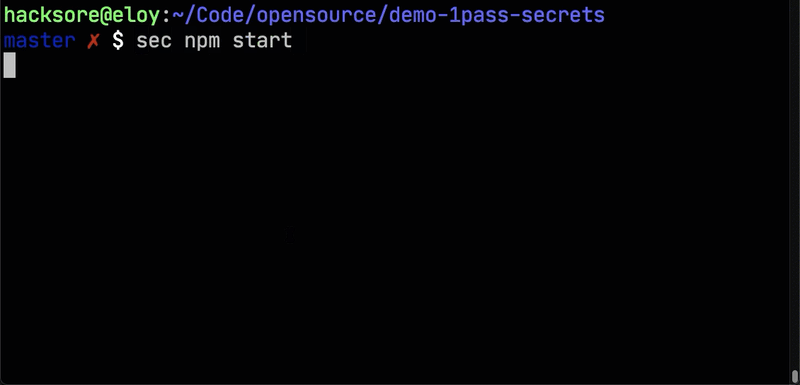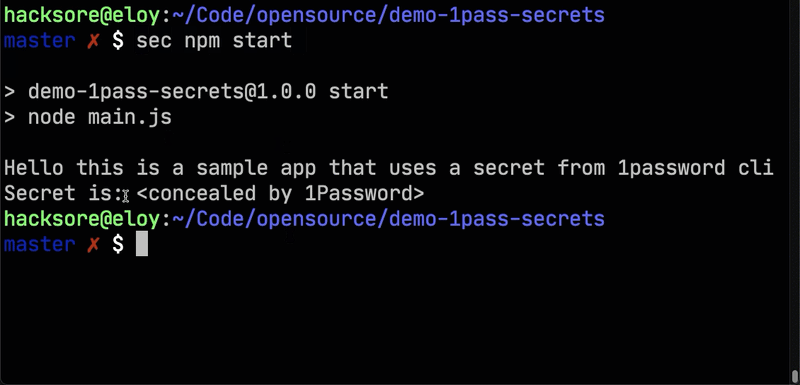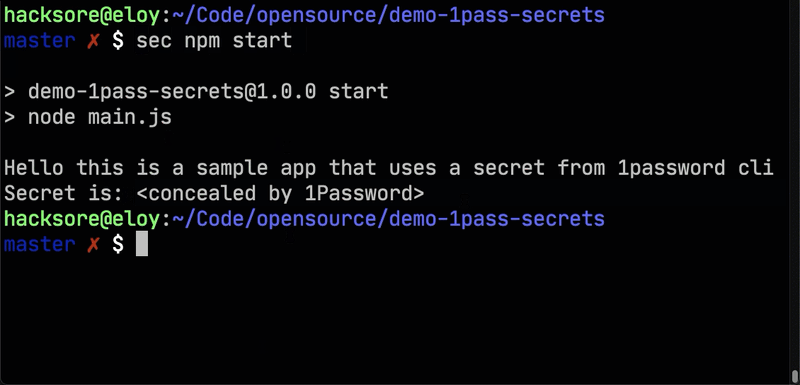
sec npm start
And there you have it! You can now start apps that require secrets in environment variables just by prepending the sec util.
It should work well for any language as long as you can start your app from the CLI.
Additional Resources
Demo Repo
1Password Docs
1Password Blog
Inspiration







Top comments (0)