One of the most important things about a website is to make sure it is secure, and Magento is no exception. Business owners work every day to learn the many different ways to keep Magento websites safe.
I had a client once who hired a Magento developer, made their first payment, and then the developer disappeared. They tried to reach the developer time and time again, with no success.
Once they missed the second payment, the developer suddenly contacted them and said that he wouldn’t do any work until the second payment was made. Naturally, the client refused.
The next day, the client found their website completely down and the code was an absolute mess.
I was hired to see if I can clean up the hack. Here are the steps I took to verify and clean up the hack.
1. Identify the hack
If you believe your website has been hacked, the first thing you must do is confirm the hacking.
Confirming a hacking may sometimes be as easy as looking at your homepage and seeing something wrong with the screen.
Other times, hacks can be a little more difficult to confirm.
Here are some useful tips to confirm that your website has been hacked.
Scan Your Website
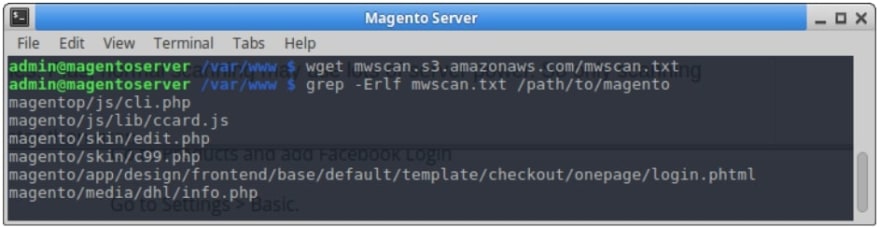
On a standard Linux or OSX server, Magento recommends that you do the following:
If there is no malware detected on your site, your code should be looking like this:
If additional items pop up from your code, be sure to make note of the additional lines, or errors, you might find. Be sure to do the following:
Looking for small things on your Magento website can help you save your business.
Check Magento File System
Check for any new or recently modified files in your Magento backend. During this time, it would help to have a backup of the website live while you go into the code.
Having code that appears unfamiliar or malicious is a sure sign that your website was hacked.
To check for new or recently modified files, you will have to check with your host to gain access to your SSH files.
Once you have access, you may access the core file integrity by running the following codes:
$ mkdir magento-2.1.3
$ cd magento-2.1.3
$ diff -r 2.1.3 ./public_html
When using SSH, you can also look for files that have been modified within the last 15 days by running the following code:
$ find ./ -type f -mtime -15
Once you have found the new files, it is recommended that you look for the ones you recognize and the ones that you don’t. New, unrecognizable, files should be investigated by a Certified Magento Developer.
Verify Site Users
When you believe your Magento website has been hacked, you need to go and make sure there are no new or strange users on the site. You can go to the backend to make sure of this. To do this, simply follow the instructions below:
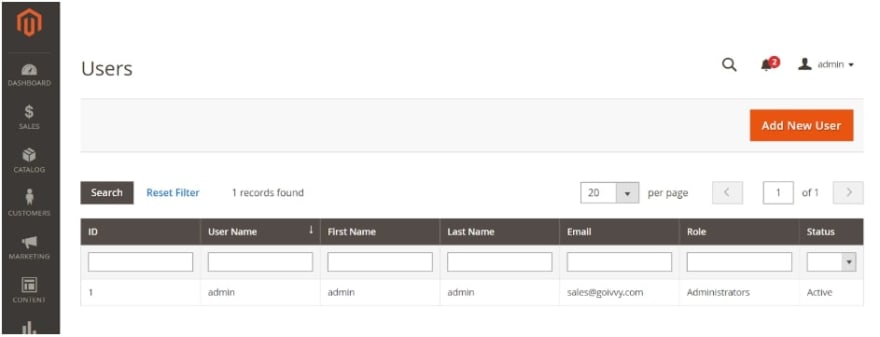
Systems → Permissions → All Users
You should be taken to the following screen:
Once there, you should be able to see all the users and you should be able to filter them out by role, name, email and all the other filters you see there.
The best way to filter out your users is to go to your backup and compare your backup user list to the hacked user list.
2. Clean the Hack
Verifying a cyber attack can be stressful and having to clean the cyber attack can cost you more than just stress. It can also cost a lot of downtimes and, ultimately, money.
However, cleaning the hack by yourself is not an impossible task.
Here are the three best steps to take when you are cleaning a hack.
Clean Files and Datatables
The first thing you need to do is get rid of the malicious code that the hacker left. The best place to start looking for those files is through SSH or FTP.
At this point, it is advisable to consult a Certified Magento Developer. However, if you choose to clean your database yourself, you should do the following after logging into the SSH:
Remove the Backdoors
If a hacker was able to go into your site, they most likely left a backdoor. Hackers generally leave backdoors on sites so that they have the opportunity to go back again.
Backdoors tend to be hidden in the core files. You may find an entirely new folder in your code. Folders like these are meant to look like core files that belong to your website.
You can access these files in the content section of the backend. All you have to do is the following:
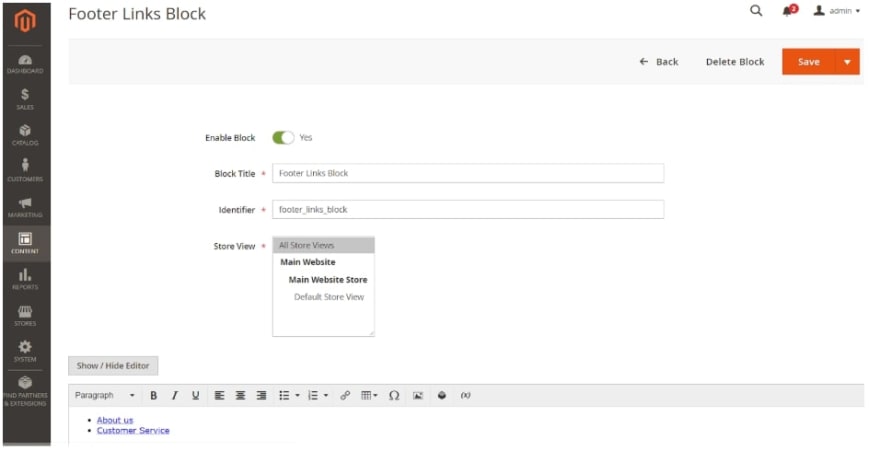
Content → Elements → Blocks
Your screen should look like the screen below:
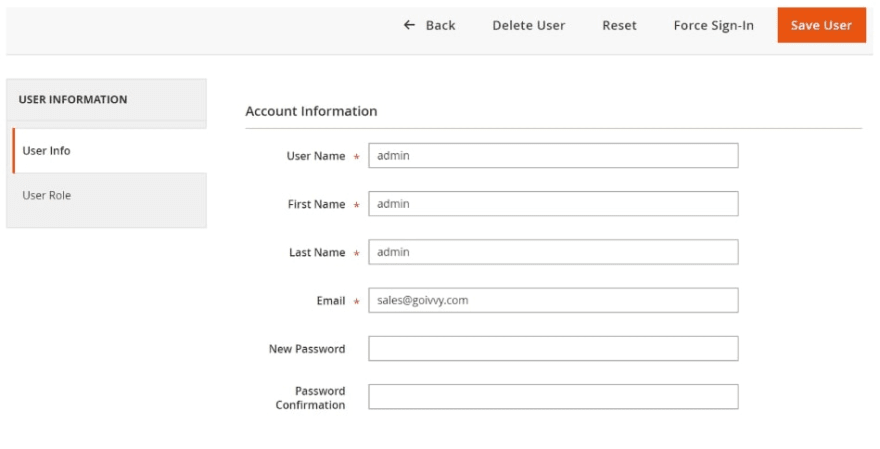
From there, just click on the block that you want to check and under “action”, select “edit”. You should be taken to the following screen:
On this page, you can check for any suspicious activity on your site.
To look deeper into the website’s coding, such as looking into PHP folders, the best thing that you can do would be to have a Certified Magento Developer take a deeper look into the site to make sure all the hidden backdoors have been scrubbed away.
Reset Passwords
Once the files have been cleaned and the backdoors have been removed, the most important thing to do is to take steps to make sure that a hacker will not have such an easy entry next time.
One of the most effective ways to do this is to reset all of your user passwords. You can accomplish this by doing the following:
It is also important to consider adding two-factor authentication to make your site harder to break into.
You should also consider having your team change their password every 30 days, as an extra precaution. It would give hackers a smaller time window to configure your password and use it, thus making cyber attacks harder to carry out.







Top comments (0)