Let’s say, hypothetically, that we receive an email from an old university address that looks like this:
Looks 👌legit.👌
It came from a .edu email address! It doesn't look spoofed. The headers match the address.
Maybe it's just someone who graduated 5 years ago and really likes to use their birthday as their password. We might even recruit a current senior, Maxwell Dulin to help us explore.
Let’s say, purely for story-purposes, that we clicked on this “verify now” business to see what all the fuss was about.
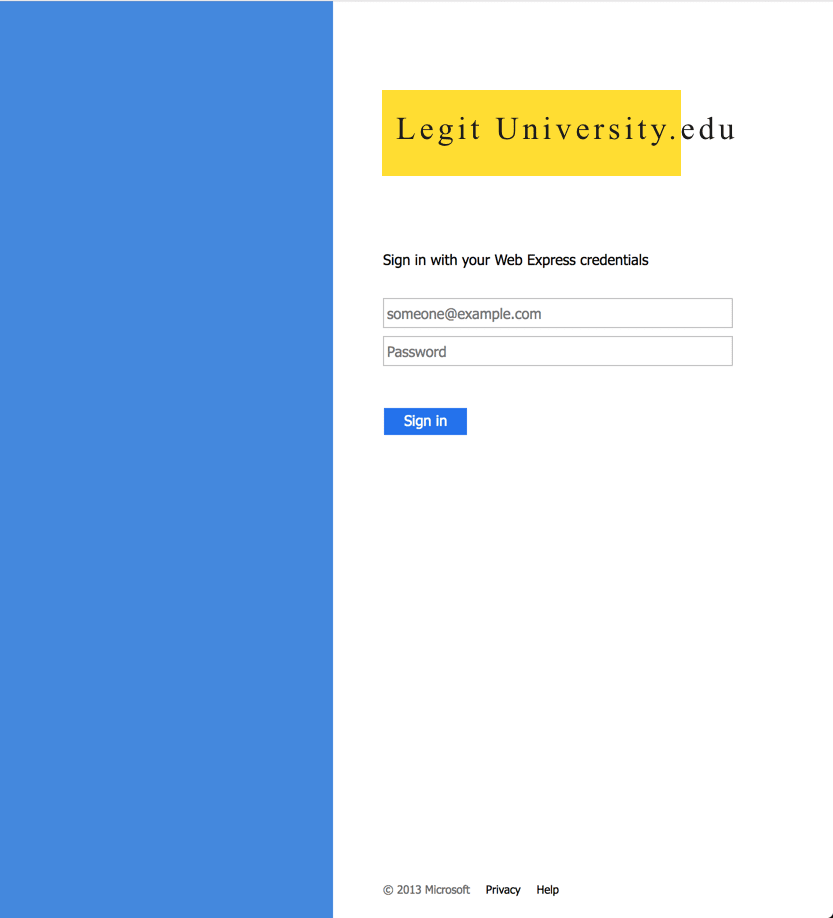
Password plz
It may look something like, I dunno, this:
And maybe it's coming from some url like:
https://bougurh.club/%20yaga/legit.edu/index.html
Let's do some peeking
We should checkout who this https://bougurh.club site is at the root.
They just show you their structure. They're even hitting multiple universities at once:
Well what can we find out?
The site's using https, so where did that certificate come from? We can use SSLHopper to see where it came from. Our SSL was only created a few days ago, so this guy probably hasn't been at this for very long.
Well, we can use dig to peer into his DNS. This guy isn't using www! The horror! He's also got an IP like this:
184.95.x.x
If we google the IP, that tells us he's using Secured Servers LLC, which doesn't have the greatest reputation for dealing with abuse claims.
What happens when we log in?
If we try to enter our details into this site, they try to send a POST to a /post.php which just logs the email and password in plaintext, then redirects us to Microsoft Outlook.
Since most students are already logged into their emails, it will appear as if the login worked. Victims might not even notice.
And that's... probably bad.
So what can we do?
Well we can reach out to the IT departments of the schools. But it's the holidays and no one's going to get back to us.
We could reach out to their domain name provider. But again: holidays.
Host provider? Lemme spell it out for you:
them.stuffFaceWithTurkey();
So what could we really do?
Well, we could send them ascii art pictures of dogs:
_.-.._ _._
_,/^^,y./ ^^^^"""^^\= \
\y###XX;/ / \ ^\^\
'\Y^ / .-==||==-.)^^
,.-=""""=-.__ /^ ( ( -/<0>++<0>(
.^ .: . . :^===(^ \ ( ( /'''^^^^^^^)
/ .: .,GGGGp,_ .( \ / /-(o'~'o))
.^ : . gGG"""YGG}. \ ) / / _/-====-\
/ (. .gGP __ ~~ . .\ \ ( ( _.---._)
/ (. (GGb,,)GGp. . . \_-^-.__(_ /______./
( \ . '"!GGP^ . . . . ^=-._--_--^^^^^~)
( /^^^\_. . . . . . . . . . . . . . . . )
) / /._. . . . . . . . . . . . . ._.=)
\ / | ^"=.. . . . . . . ._++""\"^ \
\ | | )^|^^~'---'~^^ \ )
) / ) / \ \ \
|' | \ /\ \ ( /
| | ( ( \ . .\ | (
) | ) ) ^^^^^^ | |
/. . \ | '| ) (
^^^^^^ ) \ /. . \
/ . . \ ^^^^^^
^^^^^^^
s'ko go dem zig zags
zippity zooms
See, if I was a l33t hacker, I would definitely love to see my victims best friends sending me ascii art pictures of dogs as the username and randomized compliments and fun facts as the password:
const passwords = [
'hello mr hackerman we love you very much',
'mr hackerman come join our club, we need new members',
'do it dude we wana be your friends',
'did you know bunnies actually die if they eat too many carrots',
'https://i.ytimg.com/vi/Lv4SQy_9VLI/maxresdefault.jpg',
'https://b0bcbb6c170cbb78f6d6-94268459969555eabeaba635a28d70e3.ssl.cf2.rackcdn.com/landing/april2015/bunny5.jpg',
'http://3.bp.blogspot.com/-xfI3IZT7-8E/UgQb6czrRpI/AAAAAAAAEvA/FOICuW1x_YY/s1600/36+forgot+to+stop+being+a+fetus.jpg',
'https://readjack.files.wordpress.com/2012/02/cute_bunny.jpg',
'mr hackerman dont feed bunnies too much lettuce; its like candy for them and theyll get fat',
'mr hackerman feed your bunnies a lot of lettuce so theyll get fat its adorable',
'mr hackerman you should rate our bunnies 0-10 how good of a bunny is it (this is a test the answer is 11)',
'if our ascii art doesnt show up correctly blame cpanel not us',
'mr hackerman did you red pandas use their tails as blankets',
'mr hackerman did you know sheep can recognize facial expression and they like smiles',
'mr hackerman did you know polarbears touch noses when they meet each other',
'mr hackerman did you know baby elephants suck on their trunk for comfort',
'mr hackerman did you know that monkeys make snowballs and throw them at each other',
'mr hackerman did you know that a cat has been the mayor of a town in alaska for 17 years',
'mr hackerman did you know that dogs exist',
'mr hackerman did you know that cats exist',
'mr hackerman did you know that you can save 15% or more when you switch to geico'
]
And nothing would make my day more than seeing my logs flooded so that it's hard to read any "legit" requests.
Well okay, we can send them compliments and dogs? So what? Won't they just filter it out?
Well yeah. But what if we did something a little more devious.
Instead, what if we sent them "real" requests? We could craft a little cURL like this:
const curl = (username, password, userAgent) => {
const cmd = `curl '${kiddysite}'
-H 'User-Agent: ${userAgent}'
-H 'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8'
-H 'Accept-Language: en-US,en;q=0.5' --compressed
-H 'Referer: https://bougurh.club/%20yaga/someuni.edu/Sign-In.html'
-H 'Content-Type: application/x-www-form-urlencoded'
-H 'Connection: keep-alive'
-H 'Upgrade-Insecure-Requests: 1'
--data
'UserName=${username}&Password=${password}&AuthMethod=FormsAuthentication'`
exec(cmd, (err, stdout, stderr) => {
console.log(`stdout: ${stdout}`);
console.log(`stderr: ${stderr}`);
if (err !== null) {
console.log(`exec error: ${err}`);
}
})
}
Then, we could use something like faker.js to generate real sounding email addresses like:
jwhite@someUniversity.edu
mMcarthy2@otherUniversity.edu
Then we could generate "real sounding" passwords with a little function like this:
function randomFakePassword() {
switch (Math.floor(Math.random() * 10)) {
case 0:
return randomFakeEmail()
case 1:
return faker.date.past() + faker.commerce.color()
case 2:
return faker.hacker.abbreviation + Math.floor(Math.random() * 10)
case 3:
return faker.address.streetAddress()
case 4:
return faker.address.country() + Math.floor(Math.random() * 10) + faker.address.state()
case 5:
return "passw" + Math.floor(Math.random() * 10) + "rd" + faker.commerce.color()
case 6:
return faker.company.companyName()
case 7:
return faker.finance.bitcoinAddress()
case 8:
return faker.address.streetName() + Math.floor(Math.random() * 10) + "pass"
default:
return faker.finance.accountName()
}
}
For extra fun, we can even create different user agents using faker again.
Then, we could create random timeouts and drip requests in as the day goes on. That way our hacker gets "caught" with the ascii art, but also can't easily filter out the "good" data.
Is this actually doing anything?
A lot of l33t hackers are newbs. They're copy/pasting code and setting things up pretty poorly. They're not experts.
That means they're often skittish. In this case, it only took a hundred requests or so before they shut down their site.
But let's say they didn't shut it all down in a fit of panic. What could this have accomplished?
It could slow them down.
They're reading emails and passwords off CPanel logs; they're not the NSA. Lots of their work is going to be manual.
If we can load them up with a bunch of fake passwords and emails, we can give the chance for the IT departments to block the domain and issue warnings to students.
We also give ourselves time to reach out to their hosting providers and report abuse.
Is this the correct way to handle the situation?
No. Report it to the authorities and let them deal with it. This is all just hypothetical after all.
This article was heavily helped in creation, content, and misadventure by Maxwell Dulin, a fantastic security enthusiast and engineer who's looking for a job! Send me a message and I'll give you his contact info.









Top comments (7)
Absolutely loving your posts!
Just wanna check in to let you know we’re actively working on the stuff you outlined in the recent DEV UX post. 😊
Kind of just felt like re-iterating that out of appreciation for the knowledge-share you’ve been providing.
Thanks so much Ben! :)
And awesome! If I get a chance I'd like to try and help! Though at the moment I'm so swamped from other duties 😅
Friend of mine did this on two phishing attempts. Both times it turned out to be a pentest.
Maybe you could even delete any data they might have successfully phished:
Here I think about the importance of 2FA on every important account in the first place. It does not solve everything, but it is another (important) layer of protection. Clever phishing attacks are incredibly hard to detect. Nice article, Evan!
My New Hobby : Trolling Phishers 😎
Is this the correct way to handle the situation? Maybe... 😝
So funny