FIDO2 Introduction
FIDO2 is a passwordless technology, meaning you don't need to create and remember a secret. Instead, the secret will be generated for you and stored by any supported authenticator. Authenticators can be a platform (laptop, desktop, mobile) or roaming device (security key, e.g. Yubikey). For simplicity, we can refer to authenticators as devices.
From a security perspective, if a platform device uses a TPM, it can provide the same level of assurance as a security key. A secret never leaves a device; instead, it supports API to perform basic cryptographic operations. The device can be tamper-proof and compliant with FIPS 140-2 standards. It is a good idea to check what devices are FIPS 140 certified. Not all security keys are FIPS 140 certified, but it doesn't make a difference for a regular user.
You can take a roaming device with you and provide access to any device that supports USB or NFC (at least in theory). In practice, it is more complicated, and depending on the browser and the operating system (OS) you may have different outputs. From my experience, security keys work best with laptops and desktops.
You don't need a security key to start using FIDO2 Passwordless.
A security key is not something that a typical user has. It will cost you ~25-50 USD. Double it if you need a spare. But everyone has a laptop (desktop) or a mobile device. Let's use it!
How FIDO2 works
The official FIDO website provides great illustrations for registration and login flows.
Registration
Login
FIDO2me follows the same pattern! Keep in mind, it is not limited to mobile devices.
FIDO2me Registration
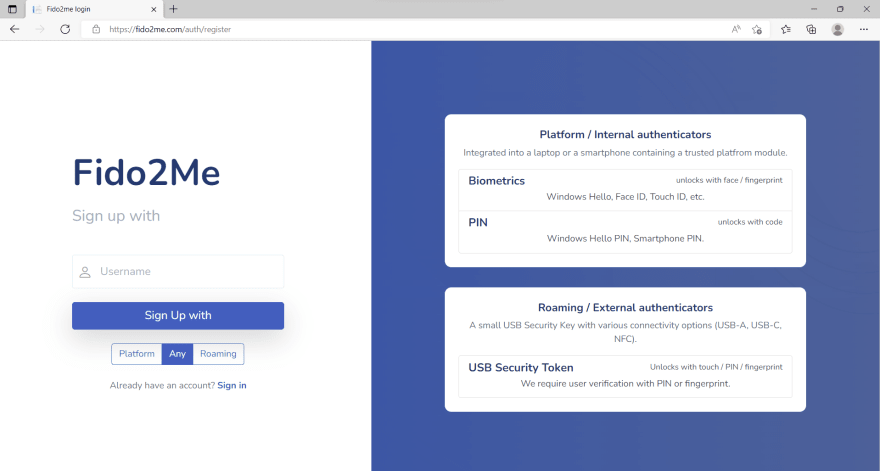
Let's visit the FIDO2me website. if it is your first use, you will be redirected to the login page. But we don't have an account yet, click on Sign up.
On the left, we have the "Username" required field, the "Sign up" button, and device selection. On the right side, a couple of examples of platform/roaming authenticators to give an idea of what you can use. Provide your username and click the button. The Username needs to be unique - it is your main identifier for Fido2me.
Congratulations, you've just asked a browser to create a new credential for you. The browser will ask available authenticators on the system to handle the request.
Register with Platform authenticator
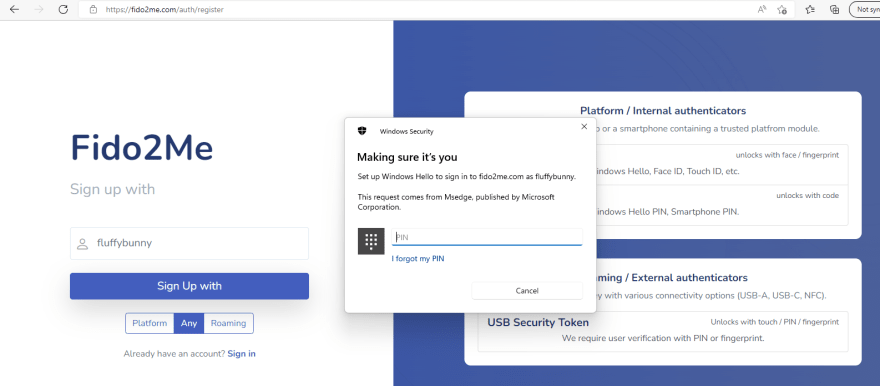
Platform authenticators are preferred options. If you didn't change a default "Any" device type selection, it will ask you to unlock your platform authenticator. In my case, unlock with a PIN (Windows Hello). Note: Windows Hello needs to be enabled with at least a single verification method, e.g. PIN.
Complete unlocking the device and let your browser send the attestation response back to our server. New Credential ID will be generated by the device. The server (Fido2me) will complete the registration ceremony according to FIDO2 specifications and create a new user account for you. You will be redirected back to the Login screen.
Device Type Selection
If you didn't specify the authenticator type, it will first ask a platform authenticator. Don't want to use it - press Esc or click Cancel - Now you work with a roaming device. You will need to create a new PIN or unlock the device.
If you specified a device type, it will ask only for this particular authenticator type.
Register with Roaming authenticator
A browser / OS will guide you, just follow the process. This is what it will look like.
Privacy aspect
You may notice that the website would like to know the make and model of the security key. It is called Direct Attestation. The device will provide a cryptographically signed statement about itself. As a part of the attestation, it will return the AAGUID field. Using AAGUID we can identify the model of the device with the FIDO2 Metadata service (technically, it is just a file). If something terrible happens with the specific model, it should be reflected in the metadata service (MDS). But for our needs, we just need AAGUID to get the model and properly display it in a list of registered devices.
The type will be empty if AAGUID is unknown (not in the MDS). You can try using the nickname field if it is not provided.
AAGUID is not a piece of private information. It is a part of the MDS which is publicly available for everyone. Feel free to check all AAGUIDs of Yubikey as an example.
FIDO2me Login
Can you spot the difference?
The "Username" is optional, and the device type is defaulted to "Any" authenticator (so no selection).
Woah, why I don't need my username? The credential is stored on the device if we create a new credential as a resident key (typical case for security keys).
This is what I hear every day during the login process.
- Fido2me: I prepared a challenge already on the initial load and provided it to your browser.
- Browser / OS: Hey, known devices, does anyone have a credential for fido2me? I have the challenge to sign from fido2me. Anyone?
- Platform device: Okay, I have fluffybunny1 and fluffybunny3 records associated with fido2me.com, what do you want to use? Or maybe you want to try a security key?
- User: I feel like fluffybunny3 today; let's do it!
- Platform device: You are the boss, but you know I need to verify your PIN
- User: Click-clack
- Platform device: You did it; now I will send a special response back to the server, so it can complete the login process.
- Fido2me: Looks good, you shall pass.
You can still provide the username to speed up the process. In this case, the credential selection is skipped.
...
- Browser / OS: Hey, known devices, does anyone have this credential for fido2me? I have the challenge to sign from fido2me.
- Device with this credential: It is me, sir! Give me your challenge.
...
Non-resident keys
Not all devices support resident keys!
Non-resident keys cannot find a record based on the username, but they work with the Credential ID. They need some help from the server.
During the registration, your device will create a new one. The Credential ID is a long random string, it doesn't relate to your private key in any way. The server (Fido2me) stores this credential along with the username. The server can find your Credential ID by the username and provide it back to the device.
Now the device can find the private key by the Credential ID and complete the challenge.
It means that a username is required for the non-resident key flow.
Fido2me combines both flows and makes username optional. If you know that you work with resident keys, you can immediately click the "Sign in" button and enjoy the Usernameless experience. If you are not sure, always type the "Username".
And that's it! Now you can play with this cool technology on the fido2me website.














Top comments (0)