When you try to access a web resource that needs authentication to access, the web container (browser) activates the authentication mechanism configured specifically for that type of resource. This HTTP authentication is used by a server to challenge a client request and by a client to provide authentication information.
The main types of authentication are:
- Basic
- Form Based Authentication
- Bearer
- Digest
- HOBA
- Mutual
- Client
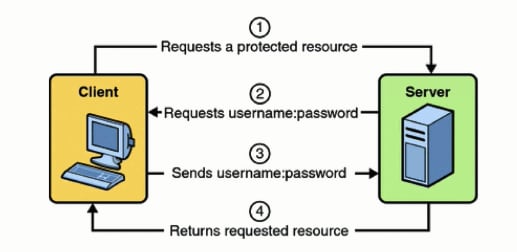
HTTP Basic Authentication
HTTP Basic Authentication (BA) is a simple technique to implement for enforcing access controls to web resources. It uses the model where the client needs to authenticate itself with a user-id and a password for each protected space by means of the HTTP Authentication header.
-
The client (browser or other proxy) makes a request to a server for protected information.
GET /securefiles/ HTTP/1.1 Host: www.somewebsitehere.com -
The server rejects the request and responds with a
401status code saying that the access was denied and aWWW-Authenticateheader.
HTTP/1.1 401 Access Denied WWW-Authenticate: Basic realm="My Server" Content-Length: 0
Note theBasicandrealmin the response. These are here to guide the client and tells you that the authentication type isBasicand therealmis a specific secure area trying to be accessed. The user might receive a Login dialog box at this time and will use it to send in their username and password.

-
The user credentials are now sent by the browser to retry the request for the
AuthorizationRequest Header.
GET /securefiles/ HTTP/1.1 Host: www.somewebsitehere.com Authorization: Basic bXl1c2VybmFtZTpteXBhc3N3b3Jkcw==
TheAuthorizationRequest Header will also contain theBasickeyword to specify the authentication mechanism and also a base64 encoding of the users credentials as<username>:<password>.
BA can remove the need for handshakes and it doesn't require cookies, session identifiers, or login pages (because BA uses standard HTTP header fields.), but it's not secure. (3)
BA uses base64 encoding for generating a cryptographic string that contains the users credentials and sends it over a HTTP request. Base64 encoding is not encryption and is easily decoded. Furthermore, sending any base64 encoded string over an HTTP request protocol to unauthenticated targets (usually servers) is not secure because the transmission is susceptible to a (hu)Man-In-The_Middle attack. (1)
Solution?
A possible solution would be to only use BA with other security mechanisms, such as HTTPS/SSL. If the connection between the client and the server is secure the HTTP Basic Authentication scheme can be considered secure. (13)
Form Based Authentication.
Form-based authentication allows the developer to control the look and feel of the login authentication screens by customizing the login screen and error pages that an HTTP browser presents to the end user. When form-based authentication is declared the content of the user dialog box is sent as plain text (like basic authentication), and the target server is not authenticated. This can expose usernames and passwords unless connecting over SSL. (6)
- A client requests access to a protected resource.
- If the client is unauthenticated, the server redirects the client to a login page.
- The client submits the login form to the server.
- The server attempts to authenticate the user.
Bearer Authentication
Bearer Authentication is a token based system used to access OAuth 2.0-protected resources. A Bearer token is an random string, used only by the server, that can be either a short string of hexadecimal characters or a more structured token such as JSON Web Tokens. (10)
HTTP Digest Access Authentication
Digest Access Authentication uses MD5 hashing to ensure that no usernames, passwords, HTTP methods, or requested URIs are sent to the server in plaintext.(8) HTTP Digest access authentication is a more complex form of authentication because for every call needed, the client must make 2. But, though Digest uses encryption, it is still vulnerable to man-in-the-middle attacks.
STEP 1 : a client sends a request to a server
STEP 2 : the server responds with a special code (called a nonce i.e. number used only once), another string representing the realm(a hash) and asks the client to authenticate
STEP 3 : the client responds with this nonce and an encrypted version of the username, password and realm (a hash)
STEP 4 : the server responds with the requested information if the client hash matches their own hash of the username, password and realm, or an error if not. (1)
HTTP Origin-Bound Authentication (HOBA)
HOBA is a digital-signature-based design of HTTP authentication that uses JavaScript-based authentication that is embedded in HTML, and is an alternative to HTTP authentication schemes that require passwords. (11)
By using digital signatures as an authentication mechanism the client creates a new public-private key pair for each host it authenticates. These keys are used in HOBA for HTTP clients to authenticate themselves to servers in the HTTP protocol or in a Javascript authentication program. The keys are not stored in public key certificates, "but instead in subjectPublicKeyInfo structures from PKIX [RFC5280]. Because these are generally "bare keys", there is none of the semantic overhead of PKIX certificates, particularly with respect to naming and trust anchors. Thus, client public keys ("CPKs") do not have any publicly-visible identifier for the user who possesses the corresponding private key, nor the web-origin with which the client is using the CPK." (12)
Mutual Authentication
Mutual Authentication is a process/technology where both entities authenticate each other. For example, the client authenticates the server and vice-versa by an exchange of certificates. In this way, the network users can be assured that they are doing business with legitimate entities and servers can be certain that all users attempting to gain access to resources are legitimate.

HTTPS Client Authentication.
Client side authentication using HTTPS is a strong authentication mechanism as it is one that requires the user to possess a Public Key Certificate (PKC), or a two-factor-authentication item.
"Secure Sockets Layer (SSL) provides data encryption, server authentication, message integrity, and optional client authentication for a TCP/IP connection." (5)

- A client requests access to a protected resource.
- The web server presents its certificate to the client.
- The client verifies the server’s certificate.
- If successful, the client sends its user name and password to the server, which verifies the client’s credentials.
- If the verification is successful, the server grants access to the protected resource requested by the client.
Which Type to Use?
As a developer, the authentication mechanism you choose is very important to the security of resource.
The authentication type depends greatly on the type of information being transmitted. Anything with sensitive information should use a client based authentication, mutual authentication, or a digest based authentication as these use SSL, most require a token of sorts to authenticate, and before the credentials are transmitted, they are encrypted through a cryptographic hash function and used with arbitrary number values to prevent replay attacks, as the values are used only once. (8)
References
- http://mark-kirby.co.uk/2013/how-to-authenticate-apis-http-basic-vs-http-digest/
- https://stackoverflow.com/questions/9534602/what-is-the-difference-between-digest-and-basic-authentication
- https://en.wikipedia.org/wiki/Basic_access_authentication
- https://en.wikipedia.org/wiki/Digest_access_authentication
- http://java.boot.by/wcd-guide/ch05s03.html
- https://docs.oracle.com/cd/E19226-01/820-7627/bncbq/index.html
- https://docs.oracle.com/cd/E19226-01/820-7627/bncbk/index.html
- https://www.techopedia.com/definition/13609/digest-authentication
- https://developer.mozilla.org/en-US/docs/Web/HTTP/Authentication#Basic_authentication_scheme
- https://oauth.net/2/bearer-tokens/
- https://tools.ietf.org/html/rfc7486
- https://tools.ietf.org/id/draft-ietf-httpauth-hoba-00.html
- https://www.ibm.com/support/knowledgecenter/SSGMCP_5.1.0/com.ibm.cics.ts.internet.doc/topics/dfhtl2a.html








Top comments (0)