Hi there!
Days ago I wrote about Kali Linux installation on AWS.
Article No Longer Available
Now let's try and have some scans running with OWASP ZAP ⚡.
Connection
I'm running Kali on AWS so I want to connect to the instance using SSH.
I have the .pem file, so I need to run just few commands.
sudo chmod 400 kali.pem
ssh -i kali.pem ec2-user@your-public-dns
For Windows users there is a good article - Connecting to your Linux instance from Windows using PuTTY
Installation
I expected to have zaproxy preinstalled, but no. So, let's install it. Though I've installed the 2019.4 version of Kali.
Let's run the command and get the zaproxy installed:
sudo apt-get update && sudo apt-get install zaproxy
Hopefully you've completed the installation successfully.
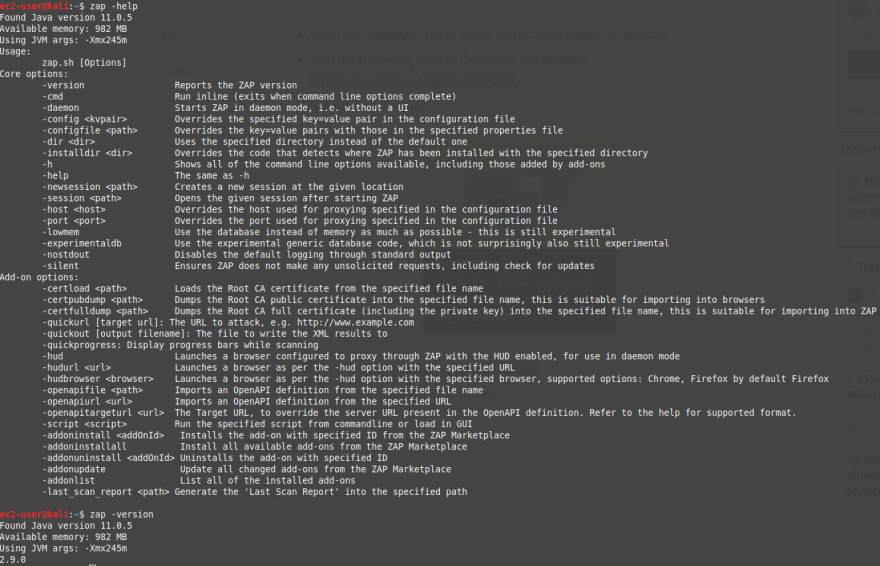
If you run the command zaproxy, you should probably see output like this:
Found Java version 11.0.5
Available memory: 982 MB
Using JVM args: -Xmx245m
0 [main] INFO org.zaproxy.zap.GuiBootstrap - OWASP ZAP 2.9.0 started 30/05/2020, 14:57:21 with home /home/ec2-user/.ZAP/
2 [main] FATAL org.zaproxy.zap.GuiBootstrap - ZAP GUI is not supported on a headless environment.
Run ZAP inline or in daemon mode, use -help command line argument for more details.
ZAP GUI is not supported on a headless environment.
Run ZAP inline or in daemon mode, use -help command line argument for more details.
We're using zap on a headless environment, so let's figure out how to use this tool in command line.
For some reason zaproxy -cmd -help command didn't work for me, so I had to figure out another way to run the tool.
The whereis zaproxy command shows us the following output zaproxy: /usr/bin/zaproxy /usr/share/zaproxy.
We're looking for zap.sh file located at /usr/share/zaproxy directory. Windows users should look for zap.bat file.
You can simply run it with bash /usr/share/zaproxy/zap.sh command.
Making a globally available command zap
If you're too lazy to type as many characters, then you can make an alias zap to /usr/share/zaproxy/zap.sh
To do that, we need to perform few simple steps and edit the .bashrc file.
- Open the
.bashrcfile using vim or nano -nano ~/.bashrc - Add the following code to the end of file -
alias zap="bash /usr/share/zaproxy/zap.sh" - Save the file and quit
- Run
source ~/.bashrcto apply changes, otherwise you need to log out and log in again - Run
zap -helporzap -version
As you can see I'm using version 2.9.0.
If your output is similar to mine, then we're done here! 🚀
Scan
Now we are ready to execute our first scan. Simply, run the following command:
zap -cmd -quickurl http://example.com -quickprogress -quickout ~/out.xml
Replace the "example.com" with whatever host you want to scan.
Here is my console output:
ec2-user@kali:~$ zap -cmd -quickurl http://example.com -quickprogress -quickout ~/out.xml
Found Java version 11.0.5
Available memory: 982 MB
Using JVM args: -Xmx245m
Accessing URL
Using traditional spider
Active scanning
[====================] 100%
Attack complete
Writing results to /home/ec2-user/out.xml
So, we just ran an attack on example.com host and got the output in XML format - the out.xml file located in /home/ec2-user directory.
Good start. But there is a one problem - I don't want output to be in XML format. I want PDF!
Add-ons
There are lot of useful add-ons in the ZAP Marketplace. We need the one named "Export Report".
ZAP allows us to install add-ons by their ID. Let's install the add-on:
zap -cmd -addoninstall exportreport
What's next?
In the next post I want to figure out the usage of Export Report add-on.
In the end I want to have scheduled scans running automatically and generating me nice PDF reports.
Have a great day! ☀️








Top comments (4)
Can you please suggest me how to run active scan through Shell script in Jenkins?
Hey, for Jenkins you can use the Official OWASP ZAP plugin.
Can i do that through shell script the way you have done in quickurl above?
Is there anyone who can reply to my query?
This is an urgency and i am blocked right now.