Many organizations and enterprises keep secrets without being mindful of their security. A February 2020 study by the Ponemon Institute found that 75 percent of respondents experienced compromised keys and certificates. This is just an example of a larger problem with mismanagement of secrets. Individuals and organizations are not careful in handling their API keys, encryption keys, tokens, private certificates, system-to-system passwords, and other secrets.
Such secrets need to be secured since they provide access to services, sensitive systems, data, and specific accounts. If it falls into the wrong hands, such secrets can thus be used to obtain other secrets or access your critical systems.
The good news is that achieving a high level of security does not have to be too complicated and technically cumbersome. This article is a review of Akeyless Vault, a secrets management solution that ensures your secrets are safe through distributed fragments cryptography and ephemeral secrets delivery.
Akeyless Vault Basics
Akeyless Vault makes it possible to manage numerous types of secrets through a graphical user interface (GUI), command-line interface (CLI), and plug-ins for native cloud platforms.
Technical users can be at home with the CLI option while those who are new to secrets management can take advantage of the simplified GUI and plug-in options. More technical users and developers can also utilize its SDKs and REST API to interface existing applications.
As a vault-as-a-service system, Akeyless provides plugin capability with popular cloud platforms, including Kubernetes, Terraform, Ansible, Docker, Jenkins, CircleCI, Puppet, Chef, Slack, and many others. This simplifies and enhances the security of secrets management with these platforms.
To make logging into the Akeyless system fast but still highly secure, it supports third-party authentication including Okta, Azure Active Directory, and AWS IAM. It is also compatible with the SAML, LDAP, and OpenID authentication schemes. This is highly convenient especially for DevOps teams whose members are working on different platforms.
Additionally, it has a well-built role-based access management system. This allows the specification of who should be allowed to use the system and which secrets and keys they are permitted to access.
Akeyless Vault also comes with powerful dashboards and analytics to enable detailed monitoring. These tools facilitate the investigation of who made requests to access specific secrets and which secrets have been viewed.
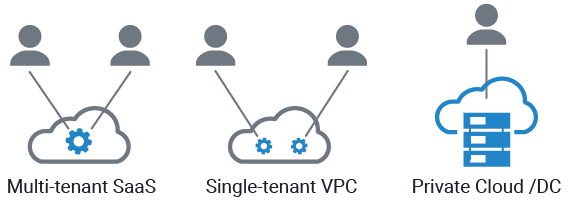
This review focuses on the software-as-a-service (SaaS) flavor, but Akeyless Vault is also available as a single-tenant VPC and on-prem solution. Whichever deployment type you choose, you can expect dependable protection and similar intuitiveness in both onboarding and ongoing usage.
Secrets supported and use cases
Akeyless supports any kind of secret in any environment and for any use case. The Akeyless Vault works with five secret types, namely static and dynamic secrets, encryption keys, SSH certificate issuer and PKI certificate issuer. The platform can also be used to manage the TLS certificate lifecycle, enabling a highly-secure and automated creation, renewal, and revocation of certificates.
Static secrets are key/value-variable and include secrets such as passwords, API tokens, PII, and credit card numbers. Dynamic ones involve the creation of ad-hoc temporary credentials for specific resources, such as SQL DB and kubectl. Encryption keys refer to AES or RSA keys used to first full-encrypt any kind of data as well as to sign binaries or app transactions.
Akeyless also provides managed on-demand access in lieu of issuing permanent SSH keys. Instead of issuing SSH key pairs (public and private), the solution provides ephemeral certificates to allow access via SSH protocol, thus eliminating the need for permanent SSH keys.
Akeyless Vault is not only an excellent tool for storing secrets securely. It can also be used for TLS certificate automation, automated code signing from within the CI/CD pipeline, and on-the-fly data encryption.
It’s also worth mentioning that Akeyless can employ a Just-in-Time approach in storing and using secrets. This is made possible by the dynamic secrets function, through which users can automate the process of generating and using ephemeral secrets for specific tasks involving human-to-machine and machine-to-machine interactions. Akeyless can create short-lived credentials on a need-to-access basis, which are set to automatically expire shortly after a specific task has been completed.
The Akeyless architecture
You can use Akeyless for hybrid and multi-cloud environments. It also supports multi-region cloud to provide reliable service availability without the latency issues. This makes it suitable for low-connectivity environments.
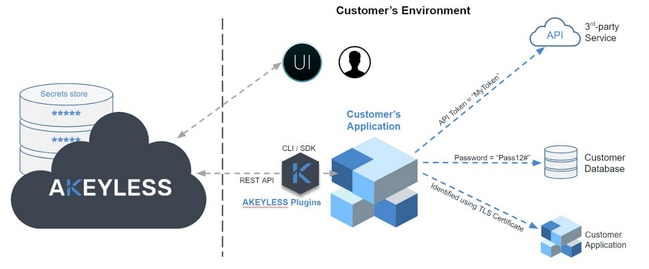
Akeyless is completely separate from a customer’s environment and is only linked to the customer environment through GUI, CLI, or plugins. Customer secrets with regards to third-party services, databases, and applications are not duplicated and stored in the Akeyless secrets store. Instead, a unique technology (discussed below) is used to make sure that these sensitive data are never revealed to anyone, not even to the Akeyless service.
Guaranteed security with the Akeyless DFC technology
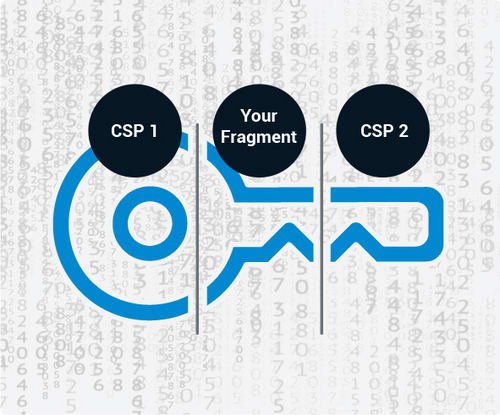
One of the most distinguishing features of Akeyless Vault is its use of its proprietary Distributed Fragments Cryptography (DFC) technology. This patent-pending tech entails the fragmentation of the key, as well as its retrieval and use without having to assemble it. Since secrets are encrypted with keys that are fragmented, this makes it virtually impossible for hackers or bad actors to obtain the secret.
Akeyless does not keep a copy of the complete secret on its servers. Also, the system ensures that there is no instance of the encrypted secret fragments appearing as a whole, not even within the customer’s environment. If anyone manages to steal something, the most they can get is a fragment of the actual secret--encrypted at that.
DFC enables zero-trust encryption in any multi-cloud or hybrid environment. This works as follows:
Keeping the key fragments of a secret in multiple regions or different cloud providers;
Constant and independent mathematical refresh of all fragments; and,
Storage of one fragment of every key in the customer’s environment.
Not even the technical team at Akeyless can access the full secrets of customers since one fragment of the split secrets is always kept in the customer’s server or computer, beyond the reach and control of Akeyless.
Other secrets management systems that employ fragmentation methods eventually have to combine the fragments whenever the user needs to retrieve and use the stored secrets. This is not the case for Akeyless. With DFC, combining the fragments is unnecessary, not even at the point of encryption or decryption.
Akeyless Vault is also NIST-FIPS 140-2 certified. The National Institute of Standards and Technology conducted rigorous third-party testing for the cryptography validation standards of Akeyless, and the platform passed. DFC technology was also found to be reliable and resistant to known key attacks as per peer review by renown cryptography researchers.
Solving the Secrets Zero problem
Akeyless developed a universal identity system that allows users to identify the customer’s machines without requiring an initial secret. It can securely authenticate client requests for services as well as for the distribution of secrets without asking for more credentials than what is necessary. When CSP IAM is not available, especially with legacy systems and private clouds involved, Akeyless uses short-lived starting tokens and periodically rotated identity tokens to preserve and secure an identity. This unique solution automates identity creation based on identification details derived from the parent server.
Intuitiveness and usability
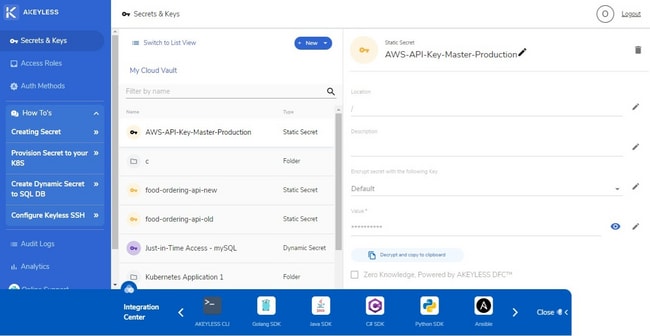
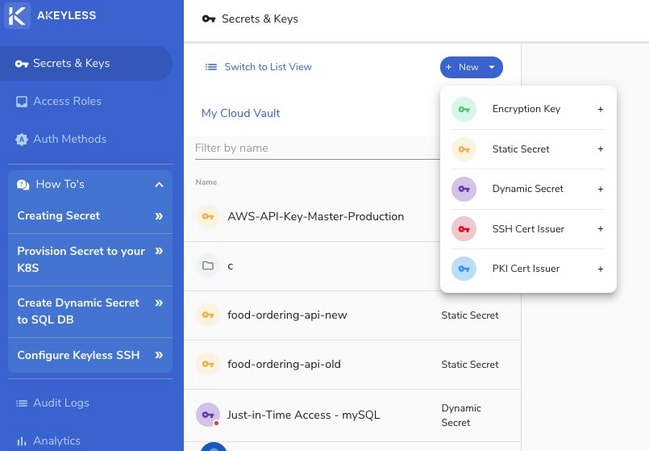
Akeyless Vault has a minimalistic interface that should be easy to become familiar with. The links and buttons for the important functions are shown on the left sidebar. These include links for creating or configuring the secrets and keys, access roles, and authentication methods.
The saved secrets and keys in Akeyless are displayed in the middle section of the user interface. You can view them as a list or collection of folders. The view mode toggle is located to the left of the New button.
Clicking on a secret or key on the list opens the details in a panel to the right of the list. This panel has editable fields. You can add more details such as the location and description. You may also delete the secret by clicking on the Delete icon on the top right corner.
Adding a secret, key, or certificate issuer to Akeyless Vault is a quick and simple process. Click on the New button to display the different options available: Encryption Key, Static Secret, Dynamic Secret, SSH Cert Issuer, and PKI Cert Issuer. Click on the option you want and fill out the form that appears.
If you are not sure about using some of Akeyless Vault’s functions, you can refer to the how-to guides linked on the left sidebar. There are tutorials on configuring keyless SSH and creating dynamic secrets to SQL DB, among many others, as quick reference. Akeyless does have full documentation of its solution, which provides a more comprehensive coverage.
If the written guides don’t suffice, you can click on the Online Support link on the bottom part of the left sidebar to ask for technical assistance through Slack or email.
Adding and configuring access roles and authorization follows the same process as adding secrets and keys. Again, if you are not sure about the information you need to enter in the different form fields, use the how-to guides. They provide enough simplified information even newbies in using secrets management tools should easily figure out.
Audit logs and analytics
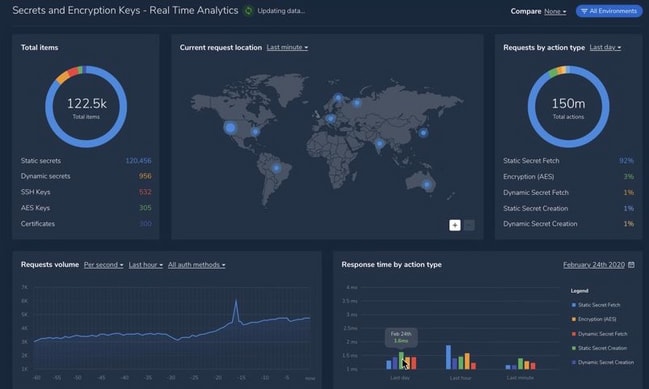
Akeyless Vault has audit logs and analytics features useful in monitoring secrets and the use of the system. The audit logs provide a detailed list of instances of access to the Akeyless Vault system. The lists include the time and date of access, the kind of activities undertaken, status code, access ID, and IP address.
The Analytics feature provides a visual guide on the use of the secrets and keys stored in the Vault. It presents a chart of the different items stored, a cartographic representation of the secret access requests made (within the last minute, hour, or day), data on requests by action, and graphs for request volumes and response times.
Integration Center
Akeyless has a sliding integration bar at the bottom part of the interface. You can hide it if you find it obstructive by clicking on the Close button to the right. This provides quick guides on how to integrate various applications, libraries, scripts, and services with Akeyless.
Akeyless Pricing
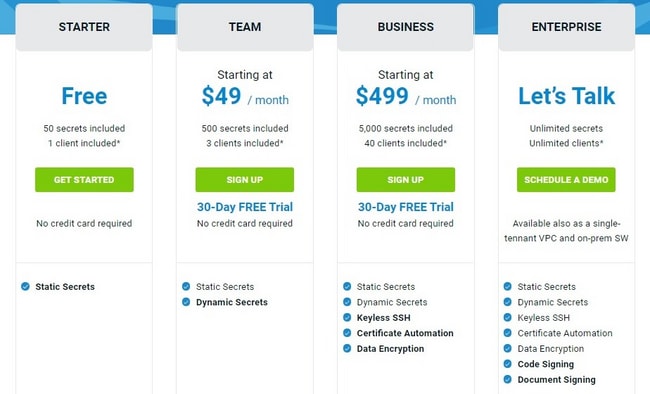
Akeyless is available for free for starter users, providing space for up to 50 static secrets. If you need to use dynamic secrets, you have to subscribe to the Team version for $49/month with a free 30-day trial. For access to more features such as keyless SSH and certificate automation, you need to upgrade to the Business package for $499/month. You can add unlimited secrets and clients with the Enterprise plan along with access to more advanced features by contacting Akeyless.
Give the range of features and the security and reliability Akeyless Vault affords, the quoted prices are certainly reasonable. You can use the free version to give the system a try or sign up for the month-long free trial under the Team and Business packages.
Verdict
Akeyless Vault is an ideal solution for a range of secrets management needs. It can scale from basic to enterprise use. The features and functions it provides easily outmatch all of the free secrets management systems and most of the enterprise solutions available. While the SaaS option is particularly notable as it does not require any installation and configuration, an on-premises solution is available for enterprise users that prefer data sovereignty. Seamless integration and various plugins make Akeyless a no-brainer choice for teams that use various platforms.










Latest comments (0)