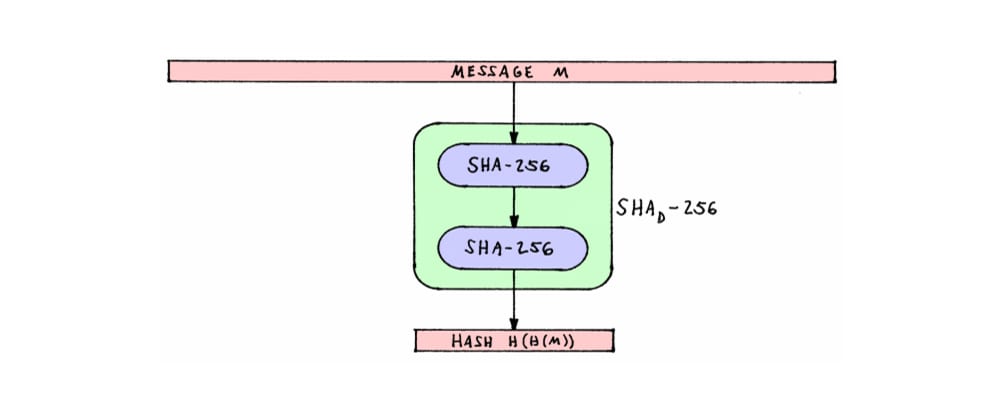
What is it?
Hashing is a method of determining the equivalence of two chunks of data. A cryptographic hash function generates a unique s...
For further actions, you may consider blocking this person and/or reporting abuse


Just a quick point, but it's important. As the hash can't be 100% guaranteed to be unique (it's just highly likely to be unique) it can only be used to determine if something is different, not to see if two things are the same (although the typical mis-use is to compare for similarities). Given the hash space of Sha1, it's fairly unlikely there will be a hash collision, but not impossible (just look to the recent issues on WebKits SVN repository caused by hash collisions). Like I said, it's a small point, but an important one nonetheless.
Hashes are also used for passwords, which are the epitome of "hey, make sure that the hash is unique to only one password!"
It's important to know that there are special hash algorithms for passwords that are specifically made for shorter strings (rather than files), and take a relatively long time to compute (so that it's harder to brute-force them).
I would not recommend shadowing the built in hash function, as it may cause problems. I'd name the import crypt_hash, just to distinguish between the two. Other than that this is a good article! Simple and to the point as I like it :)
First two lines more mislead than explain, and as Ashley Sheridan pointed out they are not completely correct.
This is a great, simple article!
Sweet and Simple.
what abount salting?
Thought it was an article about Data Structures . Nice One . But try to write something more .