Project: Meissner Lop
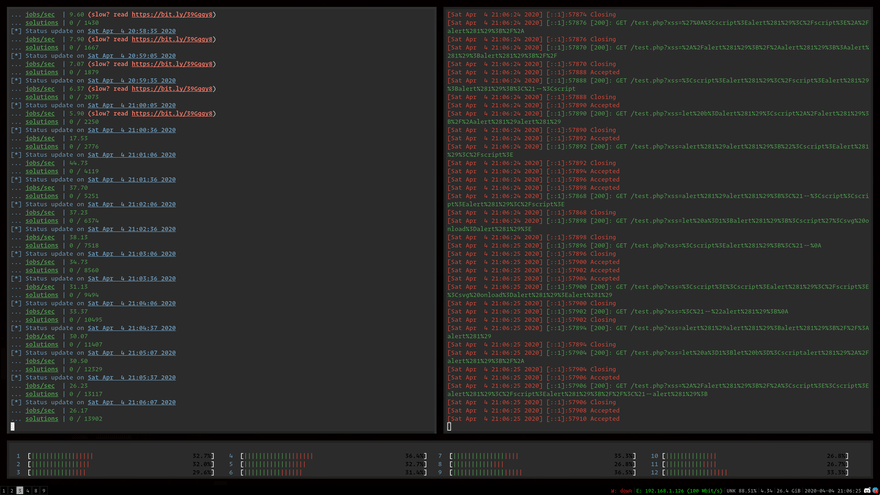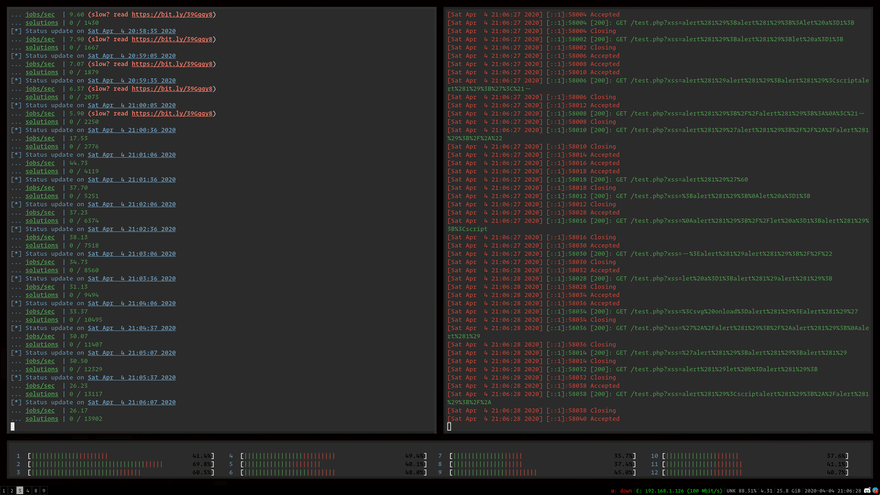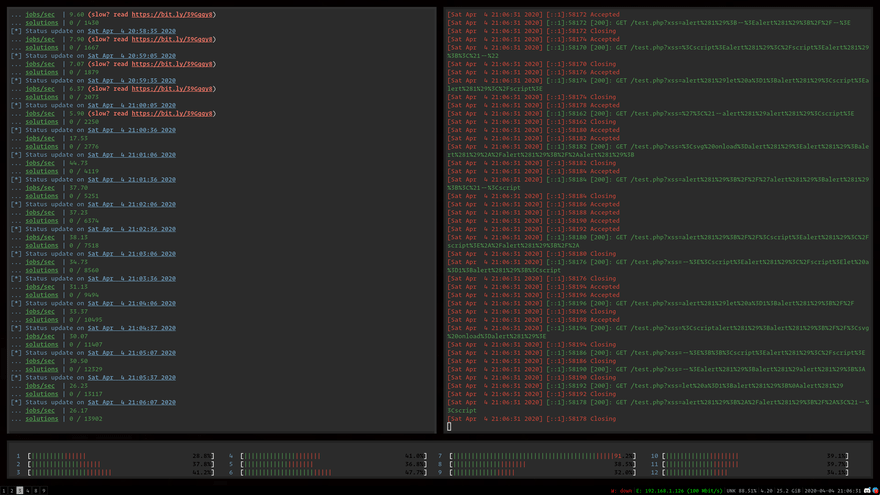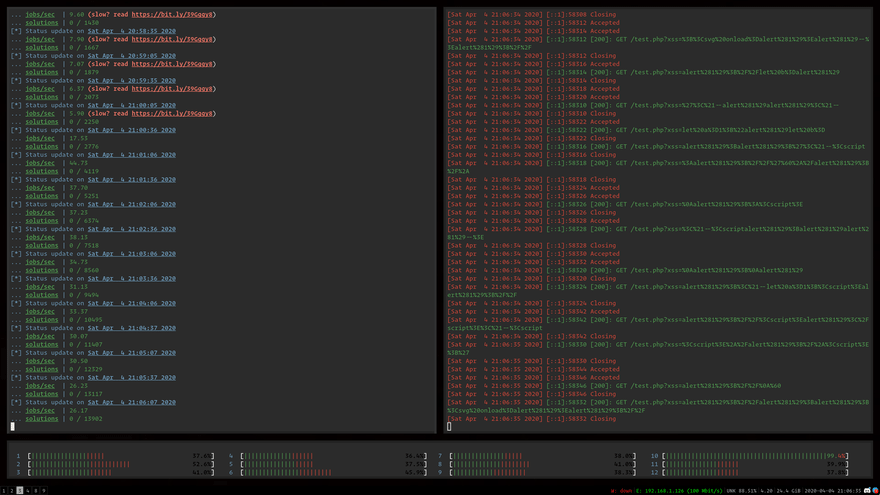
Meissner Lop is a multithreaded dictionary/mutation-based CLI XSS exploit fuzzer capable of automatically identifying filter bypasses and injection contexts.
Demo
Link to Code
About
Meissner Lop is a dictionary-based exploit fuzzer for mutation XSS.
Installation
Automatic
pip3 install meissnerManual
git clone https://github.com/arinerron/meissner.git
cd meissner
sudo ./setup.py install
Usage
usage: meissner [-h] [--no-ansi] [--log-level LOG_LEVEL] [--url URL] [--dictionary DICTIONARY] [--threads THREADS] [--filter FILTER] [--engine ENGINE] [cmd [cmd ...]]
Meissner Lop - Dictionary-based fuzzer for mutation XSS
positional arguments
cmd the command to execute, where {xss} is the injection point
optional arguments:
-h, --help show this help message and exit
--no-ansi, -c disable ANSI coloring on all output
--log-level LOG_LEVEL, -v LOG_LEVEL
set logging level
--url URL, --uri URL, -u URL
use a URL harness, where {xss} is the injection point
--dictionary DICTIONARY, --dict DICTIONARY, -d DICTIONARY
the Meissner mutation dictionary to use
--threads THREADS, --threads-count THREADS, -t THREADS
the number of threads allocated to use for engines
--filter FILTER, -f FILTER
pass the input through a filter before the program
--engine ENGINE, --browserHow I built it
Basically, it has three main components:
- the CLI. It handles HTTP requests and raw binaries/commands by abstracting the input through "harnesses".
- the XSS verification engines (selenium, etc). It actually verifies whether or not the
alert()dialog will pop, which is cool. - the mutator / payload generator. This part needs the most work.
Honestly the project still has a lot of work to do. There's not really a way to "prioritize" interesting XSS cases, so all we can do is identify the filters and context, then bash it.
Hm, the template for this post asks for my stack:
- Distro: Arch Linux
- AUR Helper:
trizen - WM:
i3-gaps - Shell: zsh+omz (
$ZSH_THEME=kolo) - Emulator:
kitty - Editor: (neo)
vimoratom - Dotfiles: https://github.com/arinerron/dotfiles
Additional Thoughts
i use arch btw







Top comments (0)